Combining power allocation and superposition coding for an underlay two-way decode-and-forward scheme
In this paper, we analyze an underlay two-way decode-and-forward scheme in which
secondary relays use successive interference cancellation (SIC) technology to decode data of two
secondary sources sequentially, and then generate a coded signal by superposition coding (SC)
technology, denoted as SIC-SC protocol. The SIC-SC protocol is designed to operate in two time
slots under effects from an interference constraint of a primary receiver and residual interference
of imperfect SIC processes. Transmit powers provided to carry the data are allocated dynamically
according to channel powers of interference and transmission, and a secondary relay is selected
from considering strongest channel gain subject to increase in decoding capacity of the first data
and decrease in collection time of channel state information. Closed-form outage probability
expressions are derived from mathematical manipulations and verified by performing Monte Carlo
simulations. An identical scheme of underlay two-way decodeand-forward relaying with random
relay selection and fixed power allocations is considered to compare with the proposed SIC-SC
protocol, denoted as RRS protocol. Simulation and analysis results show that the non-identical
outage performances of the secondary sources in the proposed SIC-SC protocol are improved by
increasing the number of the secondary relays and the interference constraint as well as decreasing
the residual interference powers. Secondly, the performance of the nearer secondary source is
worse than that of the farther secondary source. In addition, the proposed SIC-SC protocol
outperforms the RRS comparison protocol, and effect of power allocations through channel
powers is discovered. Finally, derived theory values are precise to simulation results.

Trang 1

Trang 2

Trang 3
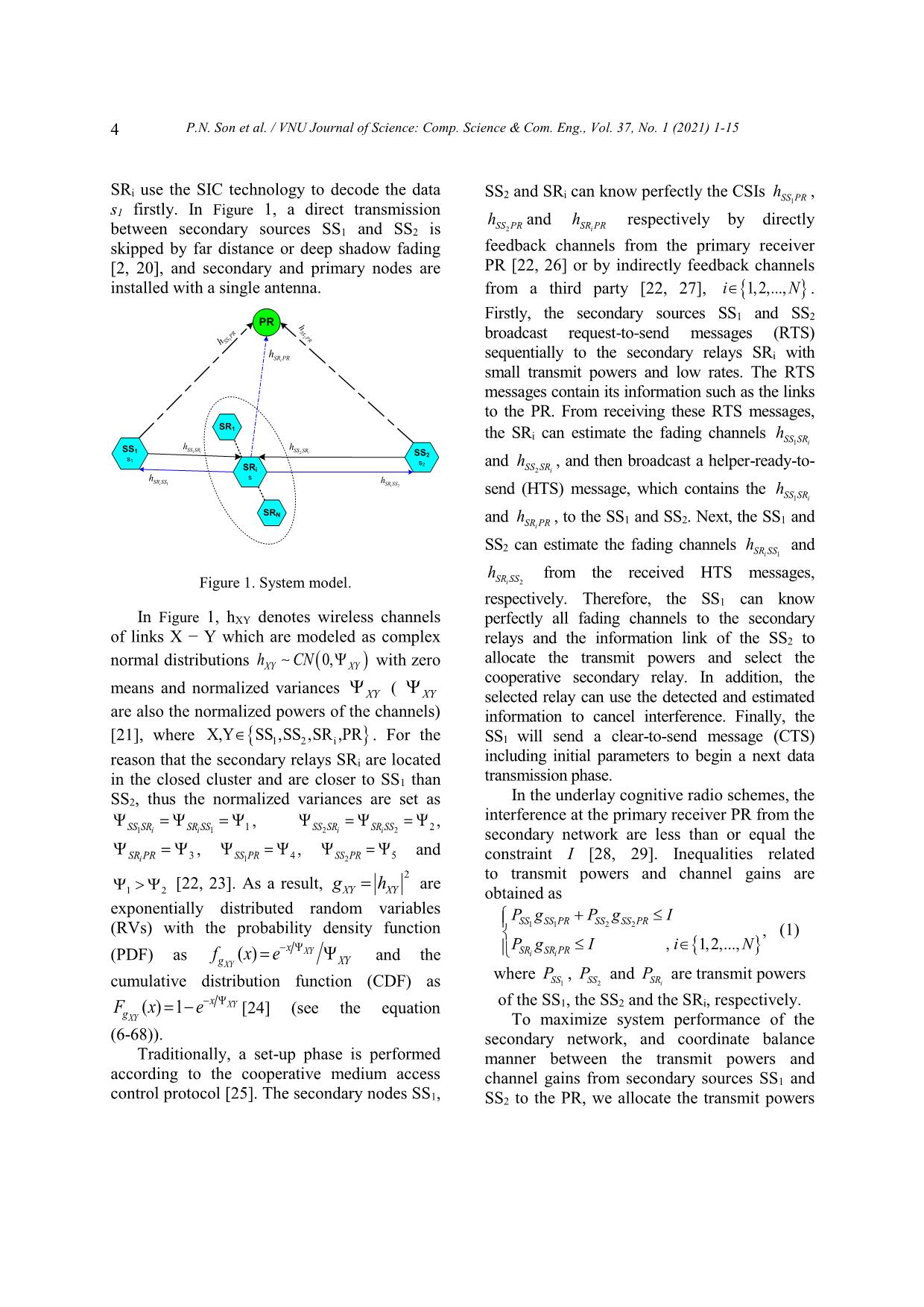
Trang 4

Trang 5

Trang 6

Trang 7

Trang 8
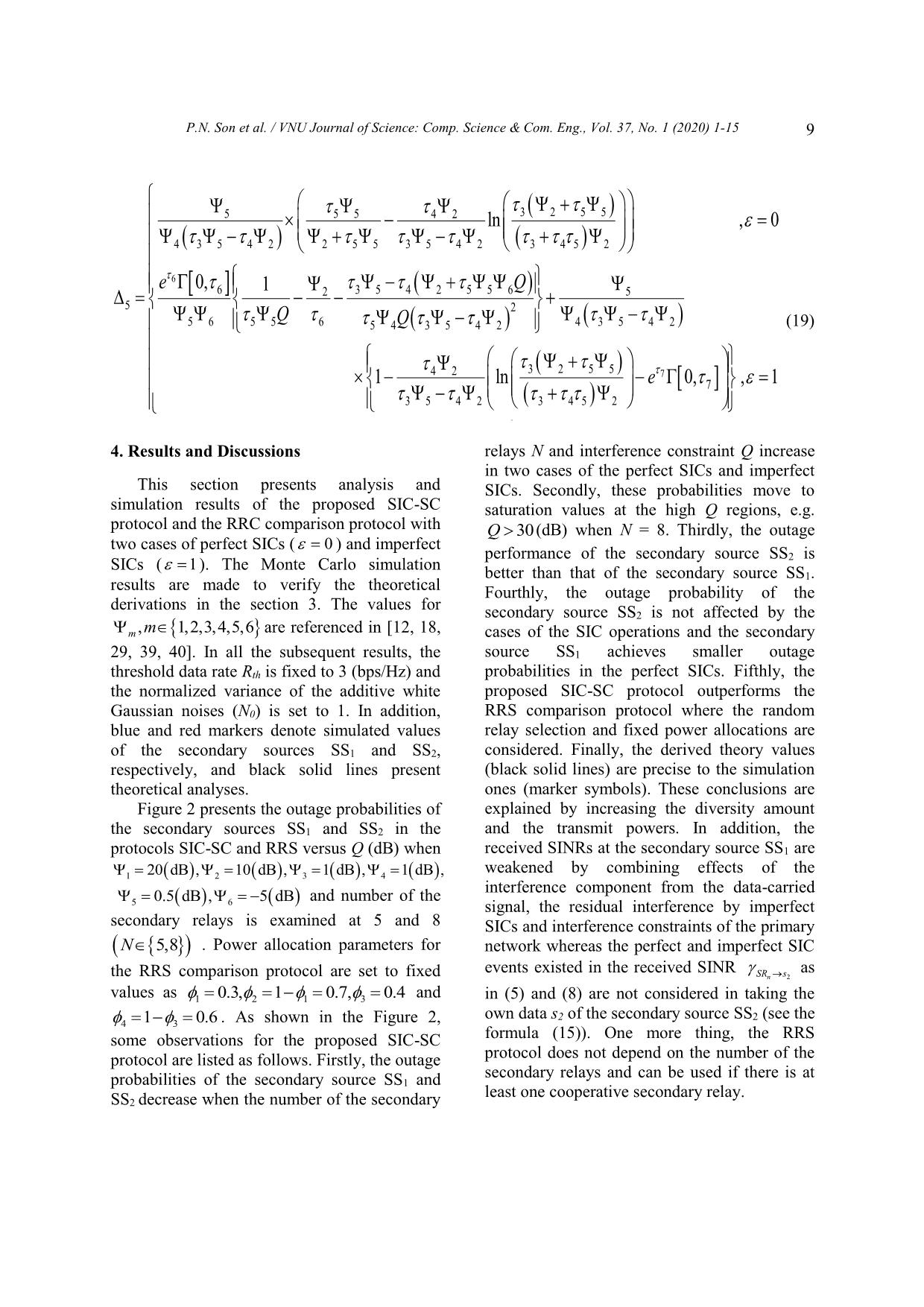
Trang 9
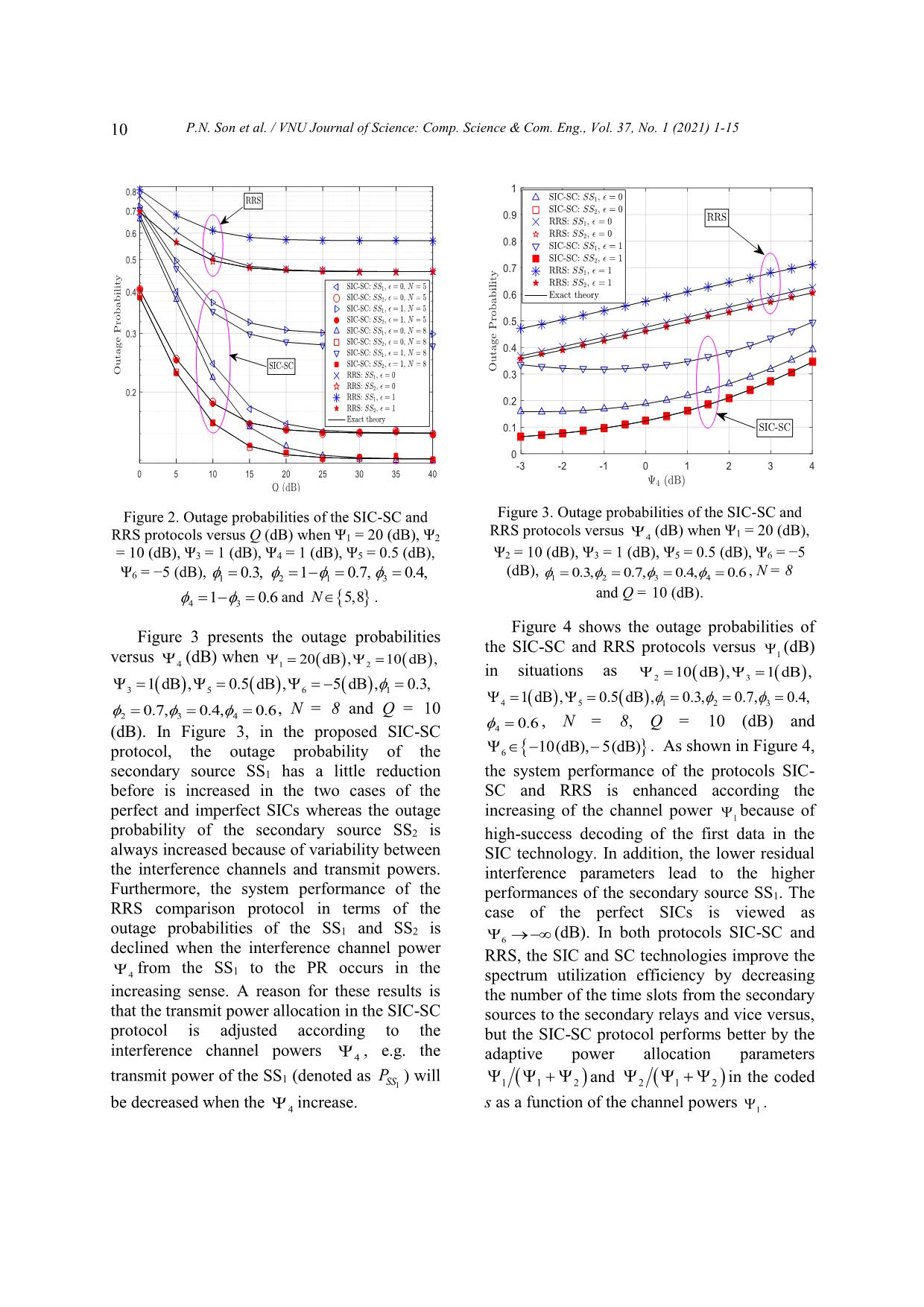
Trang 10
Tải về để xem bản đầy đủ
Tóm tắt nội dung tài liệu: Combining power allocation and superposition coding for an underlay two-way decode-and-forward scheme

B) when Ψ2 = 10 (dB), 1 system performance of the proposed SIC-SC Ψ3 = 1 (dB), Ψ4 = 1 (dB), Ψ5 = 0.5 (dB), 1 0 . 3, protocol outperforms that of the RRS protocol 234 0.7,0.4,0.6 , N = 8, Q = 10 (dB) and in terms of the outage probabilities. 6 10(dB),5(dB) . Appendix A: Proof of Lemma 1 Substituting (7) into the probability of as 5. Conclusions 1 in (9), the 1 is expressed as In this paper, we analyzed the underlay 1 Pr log 1 R 12 SRn sth1 two-way DF scheme in which the secondary 2 relays use the SIC technology to decode the 2R Pr21 th data of two secondary sources sequentially, and SRn s1 Qgg then make a coded signal by the SC technology, 5 SS12 SRn SS PR Qgggg known as the SIC-SC protocol. The SIC-SC Pr 445 SS2112 SRn SS PRSS PR SS PR protocol was designed to operate in two time 2Rth 21 slots under effects from the interference 2Rth ggSS SRSS SR 21 4 constraint of the primary receiver and residual 12nn gg interference of the imperfect SIC processes. SS12 PRSS PR 5 Transmit powers provided to carry the data Pr 1 2Rth were allocated dynamically according to 21 45 channel powers of interference and 5Q transmission. The secondary relay was selected (A.1) 2 from considering strongest channel gain subject to increase decoding capacity of the first data fxgggg Fxdx 12 , SS2211 SRnn SS PRSS SR SS PR and decrease collection time of the CSIs. The 0 where fx are Fx are the identical underlay two-way DF operation with ggXY ggXY the random relay selection and the fixed power PDF and CDF of the RVs gg, allocations (called the RRS protocol) was also XY investigated to compare the proposed SIC-SC XY,SS ,SS 12 ,SR ,PR n , nN 1,2,..., . protocol. The closed-form outage probability By referring from [29] (see equations expressions were derived from mathematical (24–25)), the fxgg is obtained as manipulations and verified exactly by SS22 SRSSn PR 12 P.N. Son et al. / VNU Journal of Science: Comp. Science & Com. Eng., Vol. 37, No. 1 (2021) 1-15 Fxgg 411 pp , the Lemma 1 is proven SS22 SRSSn PR fxgg SS22 SRSSn PR x completely. (A.2) 25 2 . Appendix B: Proof of Lemma 2 25 x From (8) and (A.1), the probability 2 as in The Fxgg is expressed as SSSRSSPR11n (9) is expressed as g 5QggSS SRSS PR Fxx Pr SS1 SRn 12n ggSS SRSS PR Qgggg 11n g 445 SS2112 SRSSn PRSS PR SS PR SS1 PR Pr 2Rth 2 21 Pr gxgSS SRSS PR (A.3) 1 11n log1 R 2 SRsthn 2 2 fyFxydygg , ggSS SRSS SR1 SS11 PRSS SR n 12nn 0 gg 2 SS12 PRSS PR Pr where Fxg is the CDF of the RV SSSR1 n PgSSSS SR 2R 22n 21th 2 g and is expressed as (see the equation I hNn 0 S S1 S R n gg (7–14) in [24]) SS12 SRSSnn SR 1 2 N gg N p p SS12 PRSS PR xpx 11(A.4) Fxeeg 11. SS1 SRn g p 0 N Pr. SS2 SRn 2R 21th Q g 454 SS2 PR p In (A.4), denotes the binomial 5 (B.1) N 212Rth g 454 n p N! To solve the in (B.1) by closed-form coefficient . 2 N pNp!! expressions, we consider two cases of perfect Then, the Fxgg is solved as SICs 0 and imperfect SICs 1 as SS11 SRSSn PR y N e 4 p p follows. Fxedy 1 py 1 ggSS SRSS PR 11n N - Perfect SICs ( 0 ): By referring from 0 4 p 0 (A.5) (A.2) and using (A.5), the 2 is obtained as N p 1 p 5 1 . N 212 fxFxdxgggg 1 p 0 14 px SS2211 SRnn SS PRSS SR SS PR 0 Substituting (A.2) and (A.5) into (A.1), the Fgg 5 is manipulated equivalently as SS22 SRn SS PR (B.2) 1 5 p N fxgggg Fxdx 12 25 p 1 SS2211 SRnn SS PRSS SR SS PR 11 dx 0 2 N px 0 25 x p 0 14 12 N (A.6) 55 p p 1 2 5 1 N p N p 1 dx 25 5 p 0 1 2 5 . N 2 5 dx p 0 0 14 24ppxx 125 . 2 0 ppxx By performing variable transformations as 14 24 12 55 2 Also performing as (A.6), 2 is solved as in 1 p p y yx and 5 3 2 4 25 xp 4 Lemma 2 with the case 0 . 25 - Imperfect SICs ( 1): The 2 in this , where 3 pp 1 4 2 1 4 and case ( 1) is presented as P.N. Son et al. / VNU Journal of Science: Comp. Science & Com. Eng., Vol. 37, No. 1 (2020) 1-15 13 5 1 Qx [4] T.M.C. Chu, H. Zepernick, Performance 212 fxFyggg 1 Optimization for Hybrid Two-Way Cognitive nSS SRSS PR 11n 00 Cooperative Radio Networks With Imperfect fydydxgg Spectrum Sensing, IEEE Access 6 (2018) 70582- SS22 SRSSn PR 70596. https://doi.org/10.1109/ICC.2007.121. x 6 e 55 1 Qx [5] K. Ho-Van, T. Do-Dac, Security Analysis for 1 Qx 0 6255 Underlay Cognitive Network with Energy- p 1 N p 1 Scavenging Capable Relay over Nakagami-m Fading Channels, Wireless Communications and p 0 N pp 45324 Mobile Computing 2019 1-16. https://doi.org/ 1 Qxp 2 10.1155/2019/5080952. 55254 2555324 1 Qxpp [6] X. Zhang, Z. Zhang, J. Xing, R. Yu, P. Zhang, W. dx. Wang, Exact Outage Analysis in Cognitive Two- 2553 1 Qxp ln Way Relay Networks With Opportunistic Relay pQxp 1 2354 (B.3) Selection Under Primary User’s Interference, IEEE Transactions on Vehicular Technology 64(6) (2015) ln By extending , changing varibables 2502-2511. https://doi.org/10.1109/ and then solving the integrals in (B.3), the TVT.2014.2346615. [7] T.T. Duy, H.Y. Kong, Exact outage probability of probability 2 is answered as in Lemma 2 with cognitive two-way relaying scheme with the remaining case 1. Hence, the Lemma 2 opportunistic relay selection under interference is verified commpletely. constraint, IET Communications 6(16) (2012), 2750- 2759. https://doi.org/ 10.1049/iet-com. 2012.0235. Acknowledgments [8] H.V. Toan, V.N.Q. Bao, Opportunistic relaying for cognitive two-way network with multiple primary This research is funded by Vietnam receivers over Nakagami-m fading, presented at National Foundation for Science and 2016 International Conference on Advanced Technology Development (NAFOSTED) under Technologies for Communications (ATC), Hanoi city, 2016, 141-146. grant number 102.04-2019.13. Khuong Ho-Van https://doi.org/10.1109/ATC.2016.7764762. acknowledges the support of time and facilities [9] H.V. Toan, V.N.Q. Bao, H. Nguyen-Le, Cognitive from Ho Chi Minh City University of two-way relay systems with multiple primary Technology (HCMUT), VNU-HCM, for receivers: exact and asymptotic outage formulation, this study. IET Communications 11(16) (2017), 2490-2497. https://doi.org/10.1049/iet-com.2017. 0400. [10] H.V.Toan, V.N.Q. Bao, K.N. Le, Performance References analysis of cognitive underlay two-way relay networks with interference and imperfect channel [1] P. Popovski, H. Yomo, Physical Network Coding in state information, EURASIP Journal on Wireless Two-Way Wireless Relay Channels, presented at Communications and Networking 2018 53 (2018). 2007 IEEE International Conference on https://doi.org/10.1186/s13638-018-1063-z. Communications (ICC), Glasgow, 2007, 707-712. [11] S. Solanki, P.K. Sharma, P.K. Upadhyay, Adaptive https://doi.org/10.1109/ICC.2007.121. Link Utilization in Two-Way Spectrum Sharing [2] Z. Cao, X. Ji, J. Wang, S. Zhang, Y. Ji, J. Wang, Relay Systems Under Average Interference Security-Reliability Tradeoff Analysis for Underlay Constraints, IEEE Systems Journal 12(4) (2018), Cognitive Two-Way Relay Networks, IEEE 3461-3472. https://doi.org/10.1109/ Transactions on Wireless Communications 18(12) JSYST.2017.2713887. (2019) 6030-6042. https://doi.org/10.1109/ [12] X. Yue, Y. Liu, S. Kang, A. Nallanathan, Y. Chen, TWC.2019.2941944. Modeling and Analysis of Two-Way Relay Non- [3] J. Mitola, G.Q. Maguire, Cognitive radio: making Orthogonal Multiple Access Systems, IEEE software radios more personal, IEEE Personal Transactions on Communications 66(9) (2018), Communications 6(4) (1999) 13-18. https://doi. org 3784-3796. https://doi.org/10.1109/TCOMM. /10.1109/98.788210. 2018.2816063. 14 P.N. Son et al. / VNU Journal of Science: Comp. Science & Com. Eng., Vol. 37, No. 1 (2021) 1-15 [13] X. Zou, B. He, H. Jafarkhani, An Analysis of E98-B(4) (2015), 661-672. TwoUser Uplink Asynchronous Non-orthogonal https://doi.org/10.1587/transcom.E98.B.661. Multiple Access Systems, IEEE Transactions on [23] K. Tourki, K.A. Qaraqe, M. Alouini, Outage Wireless Communications 18(2) (2019), 1404-1418. Analysis for Underlay Cognitive Networks Using https://doi.org/10.1109/TWC.2019.2892486 Incremental Regenerative Relaying, IEEE [14] Z. Yang, Z. Ding, P. Fan, N. Al-Dhahir, The Impact Transactions on Vehicular Technology 62(2) (2013) of Power Allocation on Cooperative Nonorthogonal 721-734. https://doi.org/10.1109/TVT. Multiple Access Networks With SWIPT, IEEE 2012.2222947. Transactions on Wireless Communications 16(7) [24] A. Papoulis, S.U. Pillai, Probability, random (2017), 4332-4343. variables and stochastic processes, 4th ed., https://doi.org/10.1109/TWC.2017.2697380. McGrawHill, New York, 2002. [15] P.N. Son, T.T. Duy, K. Ho-Van, SIC-Coding [25] L. Pei, T. Zhifeng, L. Zinan, E. Erkip, S. Panwar, Schemes for Underlay Two-Way Relaying Cooperative wireless communications: a cross-layer Cognitive Networks, Wireless Communications and approach, IEEE Wireless Communications 13(4) Mobile Computing 2020 1-24. https://doi.org/ (2006) 84-92. https://doi.org/10.1109/ 10.1155/2020/8860551. MWC.2006.1678169. [16] M.F. Kader, M.B. Shahab, S.Y. Shin, Exploiting [26] A. Ghasemi, E.S. Sousa, Fundamental limits of Non-Orthogonal Multiple Access in Cooperative spectrum-sharing in fading environments, IEEE Relay Sharing, IEEE Communications Letters 21(5) Transactions on Wireless Communications 6(2) (2017) 1159-1162. https://doi.org/ (2007) 649-658. https://doi.org/10.1109/TWC. 10.1109/LCOMM.2017.2653777. 2007.05447. [17] X. Yue, Y. Liu, S. Kang, A. Nallanathan, Z. Ding, [27] J. M. Peha, Approaches to spectrum sharing, IEEE Spatially Random Relay Selection for Full/Half- Communications Magazine 43(2) (2005) 10-12. Duplex Cooperative NOMA Networks, IEEE https://doi.org/10.1109/MCOM.2005. 1391490. Transactions on Communications 66(8) (2018) [28] H. Kim, S. Lim, H. Wang, D. Hong, Optimal Power 3294-3308. https://doi.org/10.1109/TCOMM. Allocation and Outage Analysis for Cognitive Full 2018.2809740. Duplex Relay Systems, IEEE Transactions on [18] Y. Liu, Z. Ding, M. Elkashlan, J. Yuan, Wireless Communications 11(10) (2012) 3754-3765. Nonorthogonal Multiple Access in Large-Scale https://doi.org/10.1109/TWC. 2012.083112.120127. Underlay Cognitive Radio Networks, IEEE [29] P.N. Son, T.T. Duy, Performance analysis of Transactions on Vehicular Technology 65(12) underlay cooperative cognitive full-duplex networks (2016) 10152-10157. https://doi.org/10.1109/ with energy-harvesting relay, Computer TVT.2016.2524694. Communications 122 (2018) 9-19. https://doi.org/ [19] Y. Song, W. Yang, Z. Xiang, N. Sha, H. Wang, Y. 10.1016/j.comcom.2018.03.003. Yang, An Analysis on Secure Millimeter Wave [30] T.V. Nguyen, T. Do, V.N.Q. Bao, D.B.d. Costa, B. NOMA Communications in Cognitive Radio An, On the Performance of Multihop Cognitive Networks, IEEE Access 8 (2020), 78965-78978. Wireless Powered D2D Communications in WSNs, https://doi.org/10.1109/ACCESS.2020.2989860. IEEE Transactions on Vehicular Technology 69(3) [20] X. Ding, T. Song, Y. Zou, X. Chen, L. Hanzo, (2020) 2684-2699. Security-Reliability Tradeoff Analysis of Artificial https://doi.org/10.1109/TVT.2020.2963841. Noise Aided Two-Way Opportunistic Relay [31] Y. Ruan, Y. Li, C. Wang, R. Zhang, H. Zhang, Selection, IEEE Transactions on Vehicular Energy Efficient Power Allocation for Delay Technology 66(5) (2017) 3930-3941. Constrained Cognitive Satellite Terrestrial Networks https://doi.org/10.1109/TVT.2016.2601112. Under Interference Constraints, IEEE Transactions [21] B. Zheng, M. Wen, F. Chen, J. Tang, F. Ji, Secure on Wireless Communications 18(10) (2019) 4957- NOMA Based Full-Duplex Two-Way Relay 4969. https://doi.org/10.1109/TWC. 2019.2931321. Networks with Artificial Noise against [32] H. Gao, S. Zhang, Y. Su, M. Diao, M. Jo, Joint Eavesdropping, presented at 2018 IEEE International Multiple Relay Selection and Time Slot Allocation Conference on Communications (ICC), Kansas City, Algorithm for the EH-Abled Cognitive Multi-User 2018, 1-6. https://doi.org/ Relay Networks, IEEE Access 7 (2019) 111993- 10.1109/ICC.2018.8422946. 112007. https://doi.org/10.1109/ [22] P.N. Son, H.Y. Kong, Exact Outage Analysis of ACCESS.2019.2932955. Energy Harvesting Underlay Cooperative Cognitive Networks, IEICE Transactions on Communications P.N. Son et al. / VNU Journal of Science: Comp. Science & Com. Eng., Vol. 37, No. 1 (2020) 1-15 15 [33] H. Arezumand, H. Zamiri-Jafarian, E. Soleimani- Networks, Wireless Communications and Mobile Nasab, Exact and Asymptotic Analysis of Partial Computing 2019 1-7. Relay Selection for Cognitive RF-FSO Systems https://doi.org/10.1155/2019/1839256. With Non-Zero Boresight Pointing Errors, IEEE [37] A.A. Nasir, Z. Xiangyun, S. Durrani, R.A. Kennedy, Access 7 (2019) 58611-58625. https://doi.org/ Relaying Protocols for Wireless Energy Harvesting 10.1109/ACCESS.2019.2914480. and Information Processing, IEEE Transactions on [34] P.N. Son, H.Y. Kong, Energy-Harvesting Relay Wireless Communications 12(7) (2013) 3622-3636. Selection Schemes for Decode-and-Forward Dual- https://doi.org/10.1109/TWC. 2013.062413.122042. Hop Networks, IEICE TRANSACTIONS on [38] R.I. Gradshteyn, I.M. Ryzhik, A.Jeffrey, D. Communications E98-B(12) (2015) 2485-2495. Zwillinger, Table of integral, series and products, 7th https://doi.org/10.1587/transcom.E98.B.2485. ed., Elsevier, Amsterdam, 2007. [35] T.N. Nguyen, T.H. Quang Minh, P.T. Tran, M. [39] H. Haiyan, L. Zan, S. Jiangbo, G. Lei, Underlay Voznak, T.T. Duy, T.-L. Nguyen, P.T. Tin, cognitive relay networks with imperfect channel Performance enhancement for energy harvesting state information and multiple primary receivers, based two-way relay protocols in wireless ad-hoc IET Communications 9(4) (2015) 460-467. networks with partial and full relay selection https://doi.org/10.1049/iet-com.2014.0429. methods, Ad Hoc Networks 84 (2019) 178-187. [40] B. Zhong, Z. Zhang, Opportunistic Two-Way Full- https://doi.org/10.1016/j.adhoc.2018.10.005. Duplex Relay Selection in Underlay Cognitive [36] L. Pan, Z. Li, Z. Wang, F. Zhang, Joint Relay Networks, IEEE Systems Journal 12(1) (2018) 725- Selection and Power Allocation for the Physical 734. https://doi.org/10.1109/JSYST. 2016.2514601. Layer Security of Two-Way Cooperative Relaying I
File đính kèm:
 combining_power_allocation_and_superposition_coding_for_an_u.pdf
combining_power_allocation_and_superposition_coding_for_an_u.pdf

