Security for two-way untrusted relay against constant and reactive jamming with fixed signals
Active attacking in physical-Layer security has not been significantly studied while potentially causing serious consequences for the legitimate networks. In this paper, we propose a novel method to estimate and remove the jamming signals from multiple multi-antenna jammers in a two-way relay network with multi-antenna legitimate and relay nodes. We carefully consider the signals in the time slots in order to exploit the repetition of the signals and design the transmitted signals which can work in different cases. The numerical results show that the secrecy rate at the legitimate nodes of the proposed scheme is higher than that of the conventional method when considering the affect of transmit signal-to-noise ratio (SNR); the number antennas at the legitimate and relay nodes; normalized distance between one legitimate node and the relay; and the vertical coordinate of the relay

Trang 1

Trang 2

Trang 3

Trang 4

Trang 5
Trang 6

Trang 7

Trang 8
Tóm tắt nội dung tài liệu: Security for two-way untrusted relay against constant and reactive jamming with fixed signals

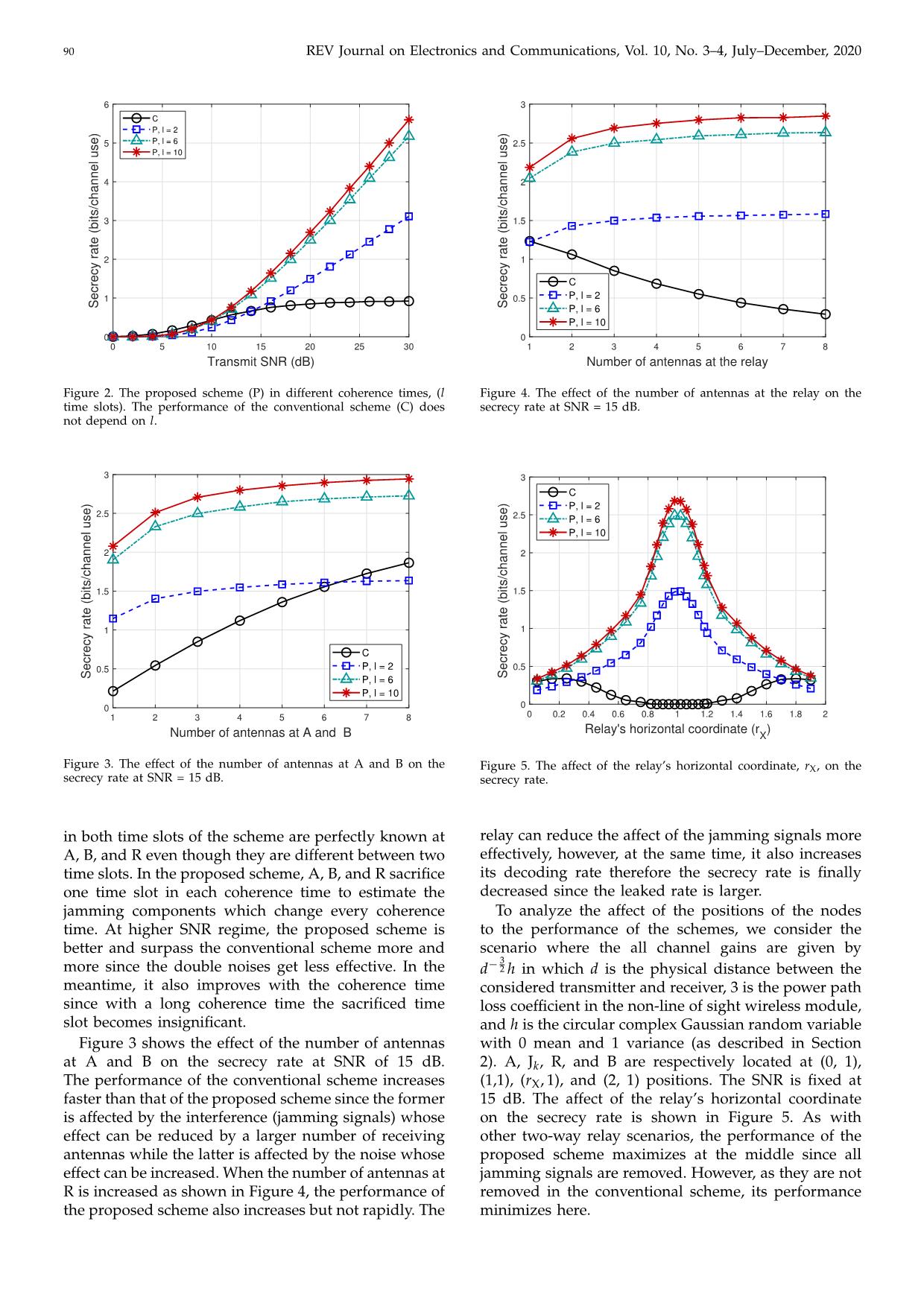
tect- to the receivers. Obviously, the secrecy sum-rate of this ing that the legitimate nodes are transmitting. When case is the same as in constant jamming. Consequently, the legitimate nodes stop transmitting, they also stop in section Numerical Results we do not distinguish jamming. However, it takes a short period of time these two jamming modes for both conventional and for them to detect a transmission. So in this period, proposed schemes. the legitimate receivers can receive and decode their needed information signals in a jamming-free way. In 5 Numerical Results this paper, we assume that this period is equal to one time slot [5]. In this section, we present several numerical results to show the superiority of the proposed scheme to 4.1 Conventional Scheme the conventional scheme in many scenarios. In the first scenario, we consider three antennas at all nodes In the first time slot of the conventional scheme, the including three jammers. The powers at a non-jamming legitimate and relaying nodes enjoy a jamming-free slot. node (A, B, and R) and a jamming node are 1 and However, from the second slot, they are continuously † 0.02 , respectively. All A-R, B-R, Jk-A, Jk-B, and Jk-R jammed. Therefore, if we consider a very large time channels are circular complex Gaussian with mean of 0 scale, the affect of the first slot is insignificant. Note and variance of 1. Since in this paper, we focus on the that the time scale we mention here is not related to the estimation and removal of the jamming signals rather coherence time since the working of the conventional than on optimization of precoding vectors, we choose scheme does not depend on the coherence time as long these precoding vectors as corresponding vectors 1. as it is at least two time slots. As a result, we almost Figure 2 shows the maximum achievable sum-rate can approximate the secrecy rate of the conventional of the proposed and conventional schemes as the SNR scheme in reactive jamming mode to that in constant is varied with different coherence times of l time slots. jamming mode. Note that the performance of the conventional does not depend on the coherence time as A-R and B-R channels 4.2 Proposed Scheme †We choose a low jamming power in order to show relative The proposed scheme is designed as follows. In the comparison between the proposed and conventional schemes. As first slot of the first phase, A and B simultaneously the performance of the proposed scheme does not depend on the 1 1 jamming power since all jamming signals are estimated and removed. transmit xA and xB, respectively. R receives the mixed The factors to deteriorate its performance is double noises as shown information signal jamming-free. In the second slot, in (24) and (25). 90 REV Journal on Electronics and Communications, Vol. 10, No. 3–4, July–December, 2020 6 3 C P, l = 2 5 P, l = 6 2.5 P, l = 10 4 2 3 1.5 2 1 C 1 0.5 P, l = 2 Secrecy rate (bits/channel use) Secrecy rate (bits/channel use) P, l = 6 P, l = 10 0 0 0 5 10 15 20 25 30 1 2 3 4 5 6 7 8 Transmit SNR (dB) Number of antennas at the relay Figure 2. The proposed scheme (P) in different coherence times, (l Figure 4. The effect of the number of antennas at the relay on the time slots). The performance of the conventional scheme (C) does secrecy rate at SNR = 15 dB. not depend on l. 3 3 C P, l = 2 2.5 2.5 P, l = 6 P, l = 10 2 2 1.5 1.5 1 1 C 0.5 P, l = 2 0.5 Secrecy rate (bits/channel use) Secrecy rate (bits/channel use) P, l = 6 P, l = 10 0 0 1 2 3 4 5 6 7 8 0 0.2 0.4 0.6 0.8 1 1.2 1.4 1.6 1.8 2 Relay's horizontal coordinate (r ) Number of antennas at A and B X Figure 3. The effect of the number of antennas at A and B on the Figure 5. The affect of the relay’s horizontal coordinate, rX, on the secrecy rate at SNR = 15 dB. secrecy rate. in both time slots of the scheme are perfectly known at relay can reduce the affect of the jamming signals more A, B, and R even though they are different between two effectively, however, at the same time, it also increases time slots. In the proposed scheme, A, B, and R sacrifice its decoding rate therefore the secrecy rate is finally one time slot in each coherence time to estimate the decreased since the leaked rate is larger. jamming components which change every coherence To analyze the affect of the positions of the nodes time. At higher SNR regime, the proposed scheme is to the performance of the schemes, we consider the better and surpass the conventional scheme more and scenario where the all channel gains are given by − 3 more since the double noises get less effective. In the d 2 h in which d is the physical distance between the meantime, it also improves with the coherence time considered transmitter and receiver, 3 is the power path since with a long coherence time the sacrificed time loss coefficient in the non-line of sight wireless module, slot becomes insignificant. and h is the circular complex Gaussian random variable Figure 3 shows the effect of the number of antennas with 0 mean and 1 variance (as described in Section at A and B on the secrecy rate at SNR of 15 dB. 2). A, Jk, R, and B are respectively located at (0, 1), The performance of the conventional scheme increases (1,1), (rX, 1), and (2, 1) positions. The SNR is fixed at faster than that of the proposed scheme since the former 15 dB. The affect of the relay’s horizontal coordinate is affected by the interference (jamming signals) whose on the secrecy rate is shown in Figure 5. As with effect can be reduced by a larger number of receiving other two-way relay scenarios, the performance of the antennas while the latter is affected by the noise whose proposed scheme maximizes at the middle since all effect can be increased. When the number of antennas at jamming signals are removed. However, as they are not R is increased as shown in Figure 4, the performance of removed in the conventional scheme, its performance the proposed scheme also increases but not rapidly. The minimizes here. C. D. T. Thai et al.: Security for Two-Way Untrusted Relay against Constant and Reactive Jamming with Fixed Signals 91 3 References C P, l = 2 [1] A. Mukherjee, S. Fakoorian, J. Huang, and A. Swindle- 2.5 P, l = 6 hurst, “Principles of physical layer security in multiuser P, l = 10 wireless networks: A survey,” IEEE Communications Sur- 2 veys & Tutorials, vol. 16, no. 3, pp. 1550–1573, Feb. 2014. [2] Y. Wu, A. Khisti, C. Xiao, G. Caire, K. Wong, and X. Gao, 1.5 “A survey of physical layer security techniques for 5G wireless networks and challenges ahead,” IEEE Journal on Selected Areas in Communications 1 , vol. 36, no. 4, pp. 679–695, Apr. 2018. [3] T. Lv, H. Gao, and S. Yang, “Secrecy transmit beamform- 0.5 Secrecy rate (bits/channel use) ing for heterogeneous networks,” IEEE Journal on Selected Areas in Communications, vol. 33, no. 6, pp. 1154–1170, 0 Jun. 2015. 0 0.2 0.4 0.6 0.8 1 1.2 1.4 1.6 1.8 2 [4] J. Y. Ryu, J. Lee, and T. Q. S. Quek, “Confidential co- Relay's vertical coordinate (r ) Y operative communication with trust degree of potential eavesdroppers,” IEEE Transactions on Wireless Communi- Figure 6. The affect of the relay’s vertical coordinate, rY, on the secrecy cations, vol. 15, no. 6, pp. 3823–3836, 2016. rate. [5] Q. Yan, H. Zeng, T. Jiang, M. Li, W. Lou, and Y. T. Hou, “Jamming resilient communication using MIMO interference cancellation,” IEEE Transactions on Informa- A, Jk, and B are kept at the same positions as in tion Forensics and Security, vol. 11, no. 7, pp. 1486–1499, Figure 5. However, the relay (1, rY) moves from (1, Jul. 2016. 0) to (1, 2), i.e., on the line perpendicular to the line [6] M. Karlsson, E. Björnson, and E. G. Larsson, “Jamming a connection A and B positions. This means that the affect TDD point-to-point link using reciprocity-based MIMO,” IEEE Transactions on Information Forensics and Security, of the position change is weaker therefore the the curve vol. 12, no. 12, pp. 2957–2970, 2017. near the maxima are more rounded than in the previous [7] A. Mukherjee and A. L. Swindlehurst, “Jamming games case. We can find the maxima of the performance of the in the mimo wiretap channel with an active eavesdrop- per,” IEEE Transactions on Signal Processing, vol. 61, no. 1, conventional scheme near rY = 0.3 and rY = 1.7. These two maximum values are symmetrical across the line of pp. 82–91, 2013. [8] L. Xiao, X. Lu, D. Xu, Y. Tang, L. Wang, and W. Zhuang, rY = 1. At these maxima, there is a balance between the “UAV relay in VANETs against smart jamming with negative affect of the jammers and the positive affect of reinforcement learning,” IEEE Transactions on Vehicular the optimal position of the relay which both culminate Technology, vol. 67, no. 5, pp. 4087–4097, 2018. [9] C. Pu, “Jamming-resilient multipath routing protocol for at rY = 1. flying Ad Hoc networks,” IEEE Access, vol. 6, pp. 68 472– 68 486, 2018. 6 Conclusion [10] L. Xiao, T. Chen, J. Liu, and H. Dai, “Anti-jamming transmission stackelberg game with observation errors,” IEEE Communications Letters, vol. 19, no. 6, pp. 949–952, In this paper, we have considered a two-way relay 2015. network with multi-antenna legitimate, relaying, and [11] L. Li, A. P. Petropulu, and Z. Chen, “MIMO secret jamming nodes. We proposed a novel scheme to es- communications against an active eavesdropper,” IEEE timate and eliminate the jamming signals in case of Transactions on Information Forensics and Security, vol. 12, constant and reactive jamming modes. The numerical no. 10, pp. 2387–2401, Oct. 2017. [12] S. Vahidian, S. Hatamnia, and B. Champagne, “On the results showed that the secrecy rate of the proposed security analysis of a cooperative incremental relaying scheme is larger than that of the conventional scheme. protocol in the presence of an active eavesdropper,” IEEE The superiority of the proposed scheme increases with Access, vol. 7, pp. 181 812–181 828, Sep. 2019. the coherence time. Generally, the performance of the [13] T. Lv, Y. Yin, Y. Lu, S. Yang, E. Liu, and G. Clapworthy, conventional scheme is affected by interference and “Physical detection of misbehavior in relay systems with unreliable channel state information,” IEEE Journal on therefore significantly improved by a larger number Selected Areas in Communications, vol. 36, no. 7, pp. 1517– of antennas at A and B. Meanwhile, that of the pro- 1530, Jul. 2018. posed scheme is affected by doubled and amplified [14] H. Pirayesh, P. K. Sangdeh, and H. Zeng, “Securing noise due to the process of eliminating jamming signals ZigBee communications against constant jamming attack and therefore slightly improved by a larger number of using neural network,” IEEE Internet of Things Journal, vol. 8, no. 6, pp. 4957 – 4968, 2021. antennas at A and B. The larger number of antennas at [15] K. Panyim, T. Hayajneh, P. Krishnamurthy, and D. Tip- the relay helps to reduce the effect of the jamming but per, “On limited-range strategic/random jamming at- also increases the leaked rate. The optimal position of tacks in wireless ad hoc networks,” in Proceedings of the the relay is achieved at the midpoint between A and B IEEE 34th Conference on Local Computer Networks, 2009, as in other relay networks. pp. 922–929. [16] M. Spuhler, D. Giustiniano, V. Lenders, M. Wilhelm, and J. B. Schmitt, “Detection of reactive jamming in DSSS- Acknowledgment based wireless communications,” IEEE Transactions on Wireless Communications, vol. 13, no. 3, pp. 1593–1603, 2014. This study was funded by Scientific Research Project [17] C. Zhang, J. Ge, J. Li, F. Gong, and H. Ding, “Complexity- B2019-VGU-05, Ministry of Education and Training aware relay selection for 5G large-scale secure two-way (MOET) of Vietnam. relay systems,” IEEE Transactions on Vehicular Technology, 92 REV Journal on Electronics and Communications, Vol. 10, No. 3–4, July–December, 2020 vol. 66, no. 6, pp. 5461–5465, 2017. Vo Nguyen Quoc Bao (SMIEEE) is an asso- [18] D. Tse and P. Viswanath, “Fundamentals of wireless ciate professor of Wireless Communications communications,” Cambridge Univ. Pr., 2005. at Posts and Telecommunications Institute of Technology (PTIT), Vietnam. He is currently serving as the Dean of Faculty of Telecom- munications and the Director of the Wireless Communication Laboratory (WCOMM). His Chan Dai Truyen Thai received the B.S. research interests include wireless communi- degree from Posts and Telecommunications cations and information theory with current Institute of Technology (PTIT), Ho Chi Minh emphasis on MIMO systems, cooperative and City, Vietnam; the M.Sc. degree from Korea cognitive communications, physical layer se- Advanced Institute of Science and Technol- curity, and energy harvesting. He is the Technical Editor in Chief of ogy (KAIST), Daejeon, South Korea; and the REV Journal on Electronics and Communications. He is also serving Ph.D. degree from Aalborg University, Den- as an Associate Editor of EURASIP Journal on Wireless Commu- mark, in 2003, 2008, and 2012, respectively. nications and Networking, an Editor of Transactions on Emerging He was with IFSTTAR, LEOST, Villeneuve Telecommunications Technologies (Wiley ETT), and VNU Journal of d’Ascq, France; with Singapore University of Computer Science and Communication Engineering. He served as a Technology and Design (SUTD); and is now Technical Program co-chair for ATC (2013, 2014, 2018), NAFOSTED- the Academic Coordinator cum Senior Lecturer of the Electrical and NICS (2014, 2015, 2016), REV-ECIT (2015, 2017), ComManTel (2014, Computer Engineering (ECE) Study Program, Vietnamese-German 2015), and SigComTel (2017, 2018). He is a Member of the Executive University (VGU). His research interests include cooperative com- Board of the Radio-Electronics Association of Vietnam (REV) and munications, vehicle-to-vehicle communications, communication for the Electronics Information and Communications Association Ho Chi high-speed vehicles, security in wireless communications, and secu- Minh City (EIC). He is currently serving as vice chair of the Viet- rity in smart grid. nam National Foundation for Science and Technology Development (NAFOSTED) scientific Committee in Information Technology and Computer Science (2017-2019). De-Thu Huynh received the Ph.D. degree in Computer Science from Huazhong Uni- versity of Science and Technology, China in 2015. He is working as a lecturer and re- searcher in the Faculty of Information Tech- nology at Ho Chi Minh City University of Economics and Finance, Vietnam. His current research interests were in the areas of Wire- less Sensor Networks, Wireless Body Area Networks, Device-to-Device Communications, Internet of Things, and Network Security.
File đính kèm:
 security_for_two_way_untrusted_relay_against_constant_and_re.pdf
security_for_two_way_untrusted_relay_against_constant_and_re.pdf

