SSG - A solution to prevent saturation attack on the data plane and control plane in SDN/Openflow networks
Abstract: The SDN/Openflow architecture opens new opportunities for effective solutions to address network security problems; however, it also brings new security challenges compared to the traditional network architectures. One of these challenges is that the mechanism of reactive installation for new flow entries can make the data plane and control plane easily become a target for resource saturation attacks with spoofing techniques such as SYN flood. There are a number of solutions to this problem, e.g., the Connection Migration (CM) mechanism in Avant-Guard solution. Nevertheless, most of the solutions increase the load at commodity switches and/or split benign TCP connections, which can increase the packet latency and disable some features of the TCP protocol. This paper presents a solution, referred to as SDNbased SYN Flood Guard (SSG), which takes advantages of the OpenFlow’s abilities to match TCP Flags fields and the RST Cookie technique to authenticate the three-way handshake process of TCP connections in a separated device from SDN/Openflow switches. Experiment results reveal that SSG solves the aforementioned problems and improves the SYN Flood attack tolerance compared to the existing solutions

Trang 1

Trang 2

Trang 3
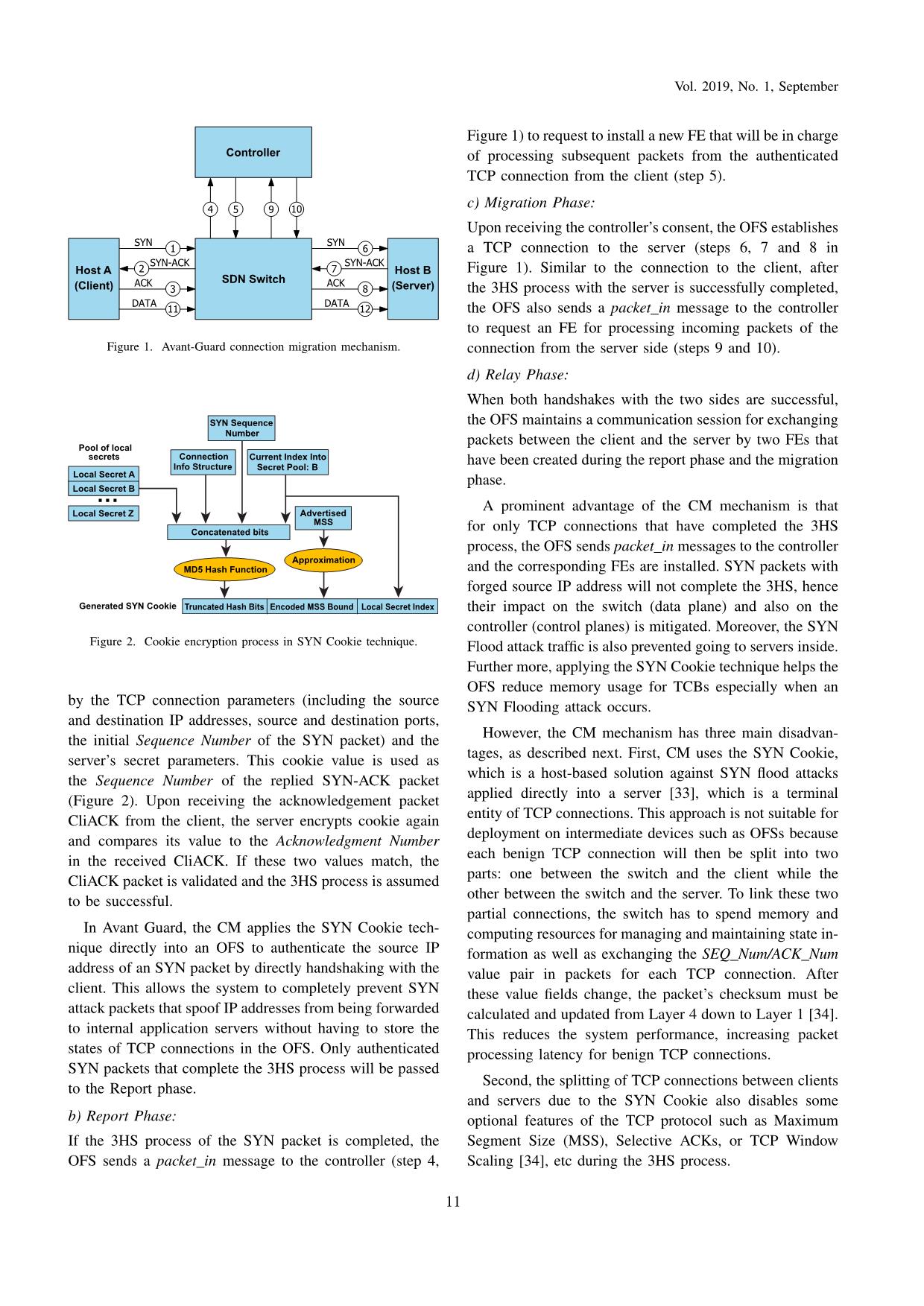
Trang 4

Trang 5
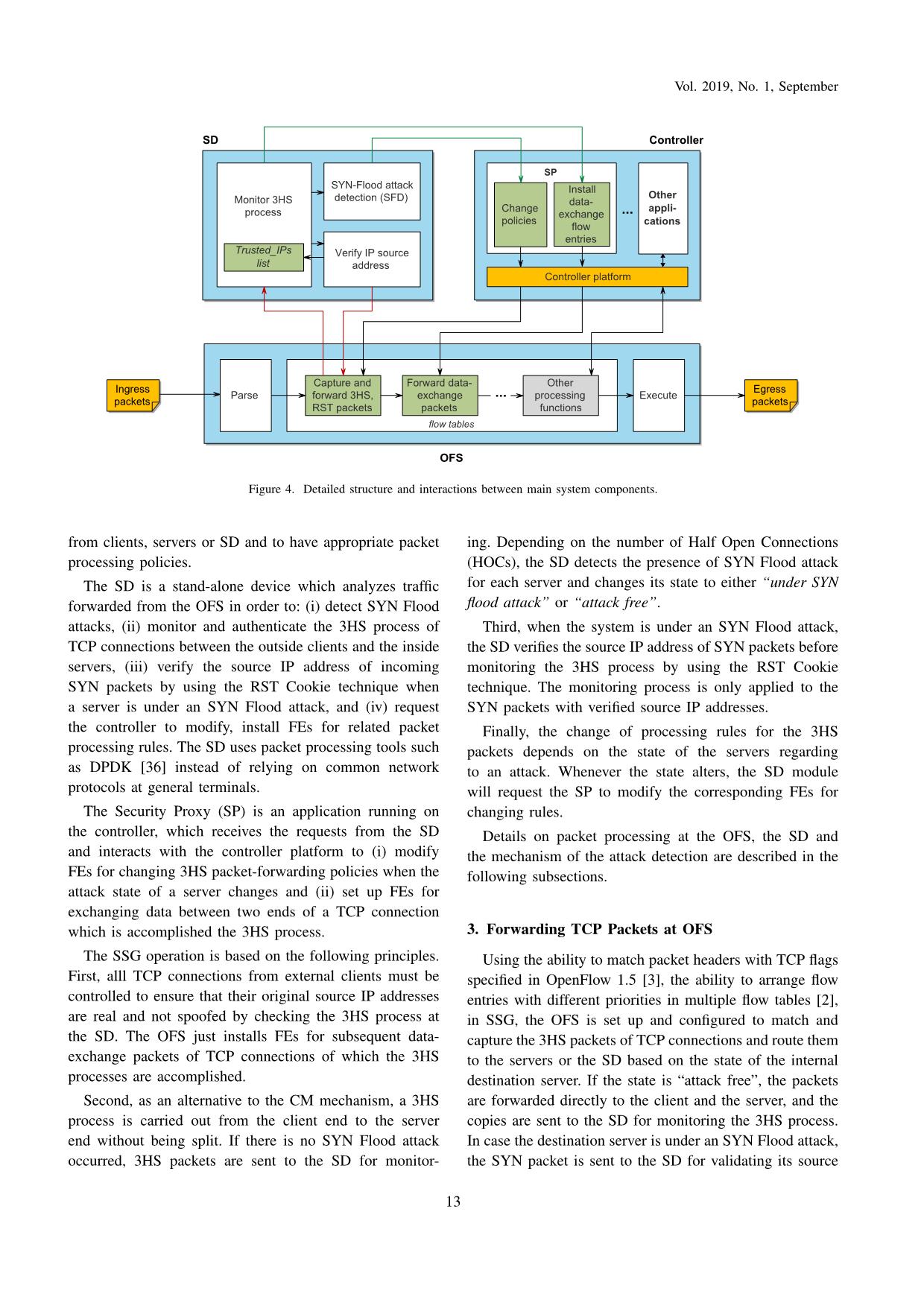
Trang 6
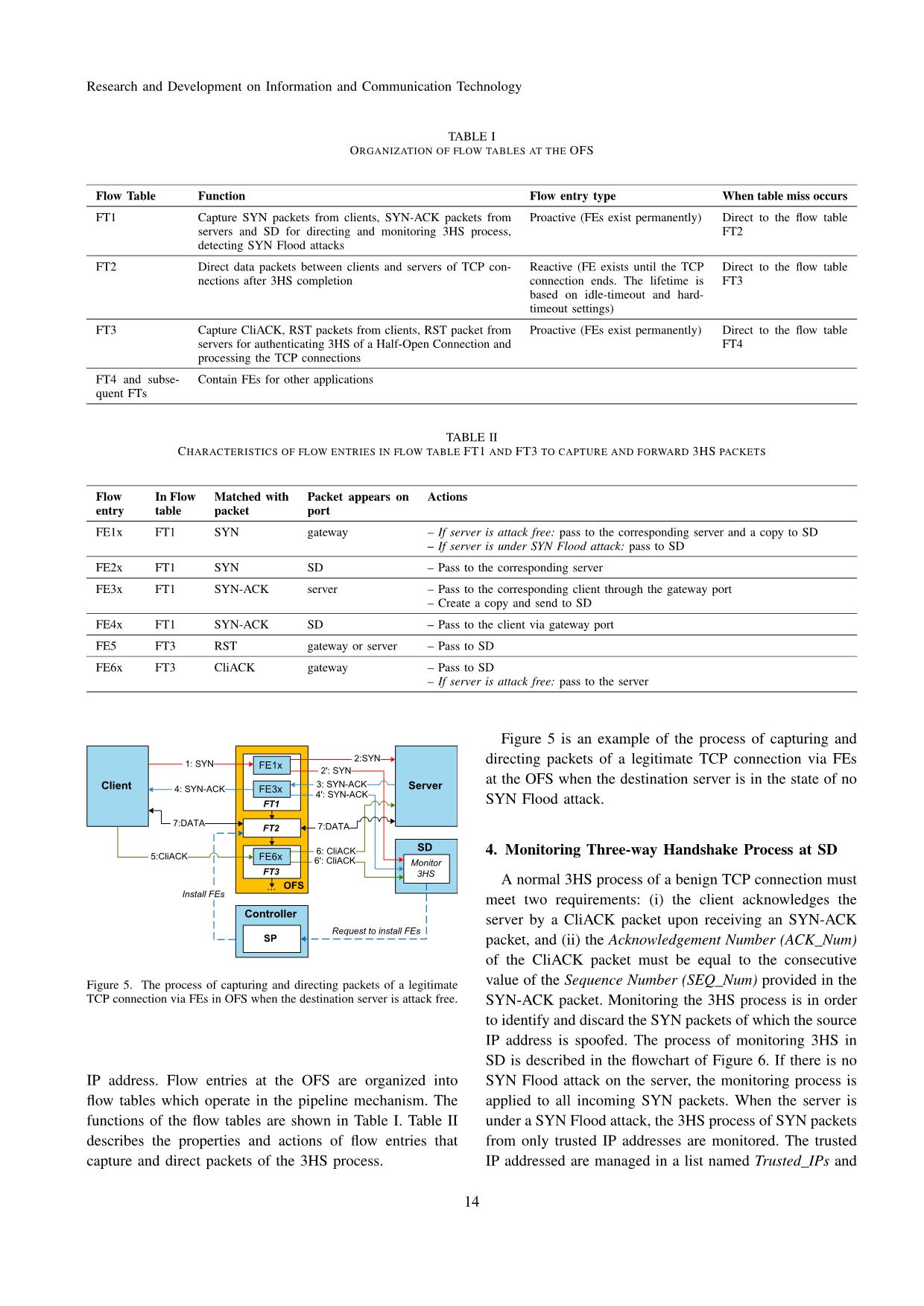
Trang 7
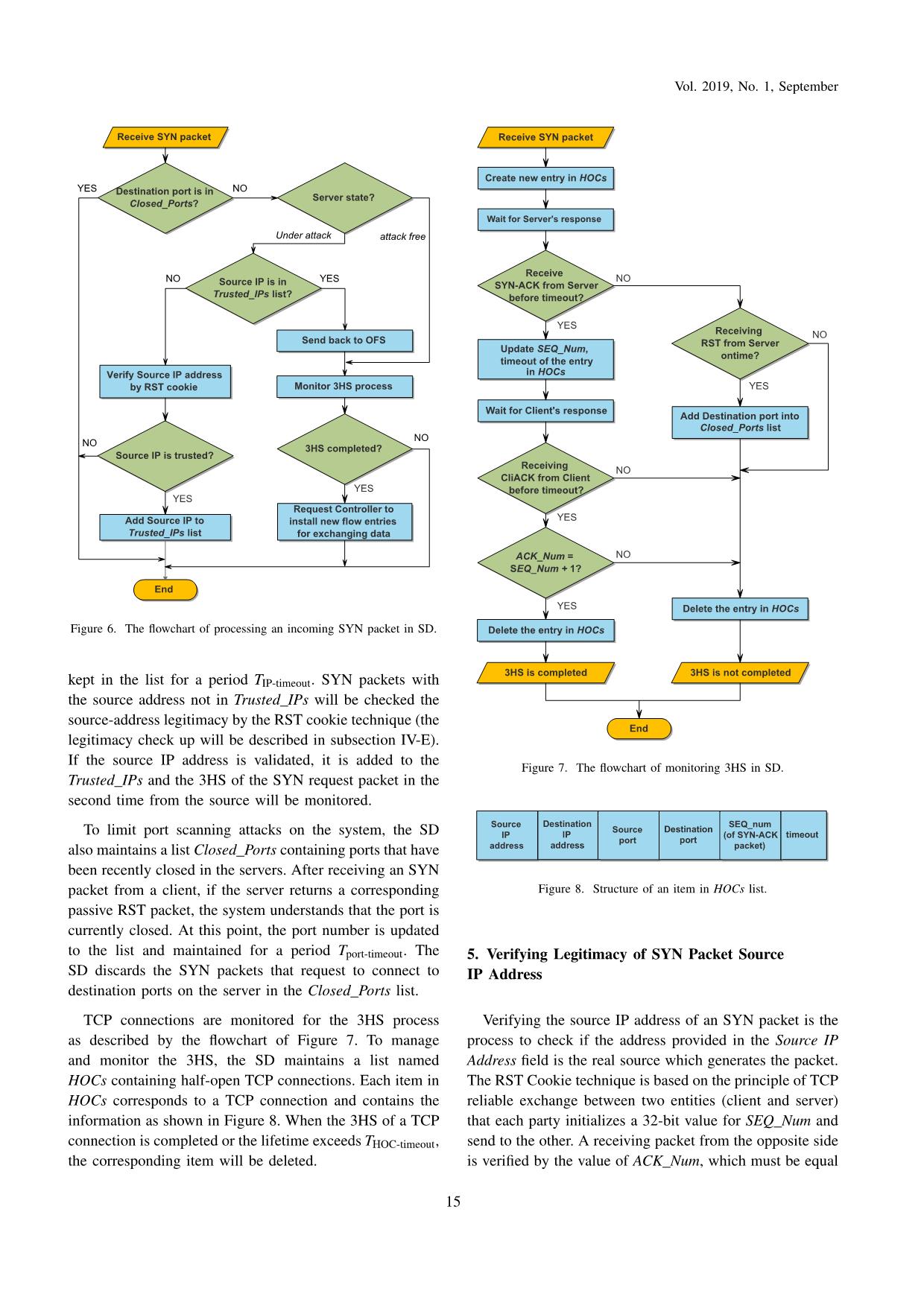
Trang 8
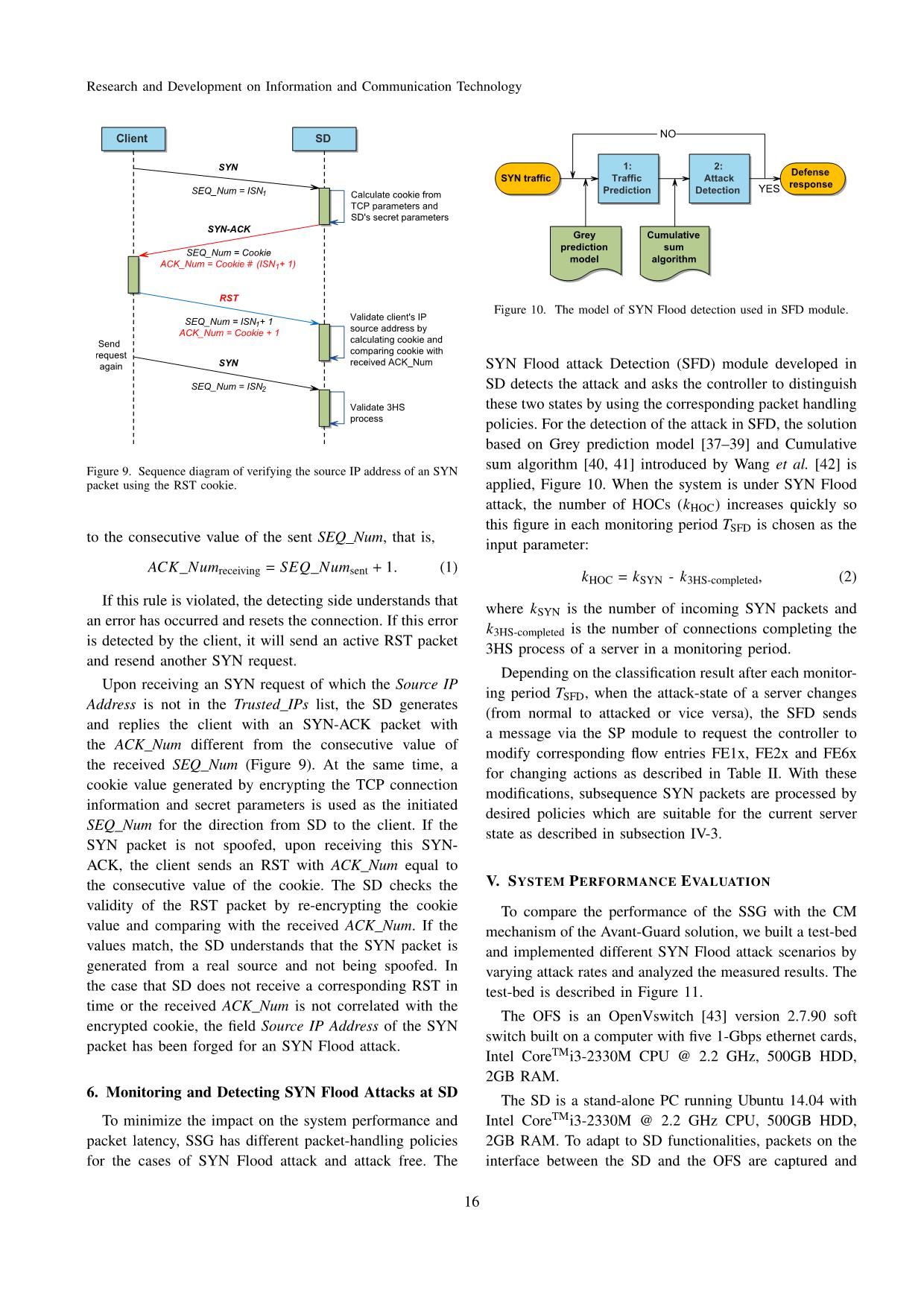
Trang 9
Trang 10
Tải về để xem bản đầy đủ
Tóm tắt nội dung tài liệu: SSG - A solution to prevent saturation attack on the data plane and control plane in SDN/Openflow networks

,7 % 0 0.5 1 1.5 2 2.5 3 0 10 0 20 0 30 0 40 0 50 0 60 0 70 0 80 0 90 0 1, 00 0 1, 50 0 2, 00 0 2, 50 0 3, 00 0 3, 50 0 4, 00 0 4, 50 0 5, 00 0 5, 50 0 R at e of tr af fic in cr ea se (% ) Attack rate (SYN pps) 1/4 servers under attack 2/4 servers under attack 3/4 of servers under attack all servers under attack Figure 16. Traffic increase rate of SSG in comparison with the CM mechanism. in Table III. The combined traffic is analyzed for four cases: 1/4, 1/2, 3/4 and all of internal application servers being attacked by SYN Flood with the source IP spoofing technique. The analyzed result in Figure 16 shows that when the system is attacked by SYN Flood, in comparison with the CM mechanism, OFS traffic increases with a small rate, just about 1.8% in case half of internal servers being attacked and over 2.5% when all the servers in the system are attacked with the rate of 5500 SYN pps each server. 4. Reduction in OpenFlow Traffic and Load on the Controller Both the Avant-Guard’s CM mechanism and the SSG solution operate based on monitoring the 3HS process of a TCP connection before requesting the controller to install FEs on the OFS. This not only prevents the resource consumption in the OFS by useless attack SYN packets but also protects the controller from being overloaded by messages of those attack TCP connections and reduces the OpenFlow traffic between the OFS and the controller. 19 Research and Development on Information and Communication Technology Comparing the interaction between the controller and system entities in CM shown as Figure 1 and in SSG described as in Figures 5 and 14, it can be seen that for each TCP connection, SSG needs only one request to the controller but this figure is two in CM. With such a difference, the total number of messages exchanged with the controller to install FEs for legitimate TCP connections in SSG solution would be a half of the number in CM mechanism. This enhancement diminishes the load on the controller and so makes SSG more resistant to SYN Flood attacks than the Avant-Guard CM mechanism. VI. CONCLUSION Inspired by the CM mechanism in Avant-Guard scheme, the proposed SSG solution moves the SYN proxy, which monitors TCP 3HS connection processes, inside the OFS to locate it in a separated device, termed the SD. The ability to match the TCP Flag fields specified in OpenFlow 1.5 is applied to filter related packets in the OFS and forward them to the SD for monitoring the 3HS process. SSG uses the RST Cookie technique to authenticate Source IP address instead of SYN Cookie as in CM. Besides, by integrating SYN-Flood attack detection module, SSG processes incoming SYN packets depending on the attack state of the destination application server. Thanks to these improvements, SSG overcomes the shortcomings of the CM mechanism and can be used as an alternative solution that can be applied to all OpenFlow 1.5 supported switches without any modification. The experiment results show that during attack-free state, SSG does not affect packet exchange between the external clients and the internal application servers. When an internal server is under SYN Flood attack, SSG consumes less resources than CM with a negligible total traffic increase at the OFS interfaces. This shows that SSG is more resistant than CM under saturation attack by SYN Flooding on the data and control planes. REFERENCES [1] Open Networking Foundation, “SDN architecture overview Version 1.0,” 2013. [Online]. Available: https://www. opennetworking.org/images/stories/downloads/sdn-resources/ technical-reports/SDN-architecture-overview-1.0.pdf [2] ——, “OpenFlow switch specification version 1.3.0 (Wire protocol 0x04),” 2012. [Online]. Available: https://www. opennetworking.org/wp-content/uploads/2014/10/openflow- spec-v1.3.0.pdf [3] ——, “OpenFlow switch specification version 1.5.1 (Proto- col Version 0x06),” 2015. [Online]. Available: https://www. opennetworking.org/wp-content/uploads/2014/10/openflow- switch-v1.5.1.pdf [4] T. Peng, C. Leckie, and K. Ramamohanarao, “Survey of network-based defense mechanisms countering the DoS and DDoS problems,” ACM Computer Survey, vol. 39, no. 1, Article 3, 2007. [5] S. Scott-Hayward, G. O’Callaghan, and S. Sezer, “SDN security: A survey,” in Proceedings of the IEEE SDN for Future Networks and Services (SDN 4FNS), Trento, Italy, Nov. 11-13 2013, pp. 1–7. [6] S. Shin and G. Gu, “Attacking software-defined networks: A first feasibility study,” in Proceedings of the Second ACM SIGCOMM Workshop on Hot Topics in Software Defined Networking (HotSDN’13), Hong Kong, China, Aug. 16 2013, pp. 165–166. [7] R. Kandoi and M. Antikainen, “Denial-of-service attacks in OpenFlow SDN networks,” in Proceedings of the IFIP/IEEE International Symposium on Integrated Network Manage- ment (IM), Ottawa, ON, Canada, May 11-15 2015, pp. 1322– 1326. [8] S. Shin, V. Yegneswaran, P. Porras, and G. Gu, “AVANT- GUARD: scalable and vigilant switch flow management in software-defined networks,” in Proceedings of the ACM SIGSAC Conference on Computer & Communications se- curity (CCS’13), Berlin, Germany, Nov. 04 - 08, 2013, pp. 413–424. [9] Daniel J. Bernstein, “SYN cookies.” [Online]. Available: https://cr.yp.to/syncookies.html [10] M. Ambrosin, M. Conti, F. De Gaspari, and R. Poovendran, “LineSwitch: Tackling control plane saturation attacks in software-defined networking,” IEEE/ACM Transactions on Networking, vol. 25, no. 2, pp. 1206 – 1219, 2017. [11] CAIDA: Center for Applied Internet Data Analysis, “The CAIDA anonymized internet traces 2013 dataset.” [On- line]. Available: 2013 dataset.xml [12] P. Porras, S. Shin, V. Yegneswaran, M. Fong, M. Tyson, and G. Gu, “A security enforcement kernel for OpenFlow networks,” in Proceedings of the first workshop on Hot topics in software defined networks (HotSDN ’12), Helsinki, Finland, Aug. 13 2012, pp. 121–126. [13] L. Wei and C. Fung, “FlowRanger: A request prioritizing algorithm for controller DoS attacks in software defined net- works,” in Proceedings of the IEEE International Conference on Communications (ICC), London, UK, Jun. 8-12, 2015, pp. 5254–5259. [14] N.-N. Dao, J. Park, M. Park, and S. Cho, “A feasible method to combat against DDoS attack in SDN network,” in Proceedings of the International Conference on Information Networking (ICOIN), Siem Reap, Cambodia, Jan. 12-14 2015, pp. 309–311. [15] R. Sahay, G. Blanc, Z. Zhang, and H. Debar, “Towards auto- nomic DDoS mitigation using software defined networking,” in Proceedings of the Workshop on Security of Emerging Networking Technologies, San Diego, CA, Feb. 8 2015, p. 7 pages. [16] S. Shin, Y. Song, T. Lee, S. Lee, J. Chung, P. Porras, V. Yegneswaran, J. Noh, and B. B. Kang, “Rosemary: A robust, secure, and high-performance network operating system,” in Proceedings of the ACM SIGSAC Conference on Computer and Communications Security (CCS’14), Scotts- dale, Arizona, USA, Nov. 03 - 07 2014, pp. 78–89. [17] S. Hong, L. Xu, H. Wang, and G. Gu, “Poisoning network visibility in software-defined networks: New attacks and countermeasures,” in Proceedings of the Network and Dis- tributed System Security Symposium, San Diego, CA, Feb. 8-11 2015, p. 15 pages. [18] M. Dhawan, R. Poddar, K. Mahajan, and V. Mann, “SPHINX: Detecting security attacks in software-defined networks,” in Proceedings of the Network and Distributed System Security Symposium, San Diego, CA, Feb. 8-11 2015, p. 15 pages. [19] D. Kreutz, F. M. Ramos, and P. Verissimo, “Towards secure 20 Vol. 2019, No. 1, September and dependable software-defined networks,” in Proceedings of the second ACM SIGCOMM workshop on Hot topics in software defined networking (HotSDN ’13), Hong Kong, China, Aug. 16 2013, pp. 55–60. [20] R. Kloti, V. Kotronis, and P. Smith, “OpenFlow: A security analysis,” in Proceedings of the 21st IEEE International Conference on Network Protocols (ICNP), Goettingen, Ger- many, Oct. 07-10 2013, pp. 1–6. [21] T. Koponen, M. Casado, N. Gude, J. Stribling, L. Poutievski, M. Zhu, R. Ramanathan, Y. Iwata, H. Inoue, T. Hama, and S. Shenker, “Onix: A distributed control platform for large-scale production networks,” in Proceedings of the 9th USENIX Conference on Operating Systems Design and Implementation (OSDI’10), Vancouver, BC, Canada, Oct. 4– 6 2010, pp. 351–364. [22] A. Tootoonchian and Y. Ganjali, “HyperFlow: A distributed control plane for OpenFlow,” in Proceedings of the Internet Network Management Conference on Research on Enterprise Networking (INM/WREN’10), San Jose, CA, Apr. 28-30 2010, p. 6 pages. [23] P. Berde, W. Snow, G. Parulkar, M. Gerola, J. Hart, Y. Higuchi, M. Kobayashi, T. Koide, B. Lantz, B. O’Connor, and P. Radoslavov, “ONOS: towards an open, distributed SDN OS,” in Proceedings of the Third Workshop on Hot Top- ics in Software Defined Networking (HotSDN’14), Chicago, Illinois, USA, Aug. 22 2014, pp. 1–6. [24] A. Vishnoi, R. Poddar, V. Mann, and S. Bhattacharya, “Ef- fective switch memory management in OpenFlow networks,” in Proceedings of the 8th ACM International Conference on Distributed Event-Based Systems (DEBS’14), Mumbai, India, May 26-29 2014, pp. 177–188. [25] L. Dridi and M. F. Zhani, “SDN-guard: DoS attacks miti- gation in SDN networks,” in Proceedings of the 5th IEEE International Conference on Cloud Networking (Cloudnet), Pisa, Italy, Aug. 17 2016, pp. 212–217. [26] H. Wang, L. Xu, and G. Gu, “FloodGuard: A DoS at- tack prevention extension in software-defined networks,” in Proceedings of the 45th Annual IEEE/IFIP International Conference on Dependable Systems and Networks, Rio de Janeiro, Brazil, Jun. 22-25 2015, pp. 239–250. [27] M. Yu, J. Rexford, M. J. Freedman, and J. Wang, “Scalable flow-based networking with DIFANE,” in Proceedings of the ACM SIGCOMM 2010 Conference, New Delhi, India, Aug. 30 - Sep. 03 2010, pp. 351–362. [28] A. R. Curtis, J. C. Mogul, J. Tourrilhes, P. Yalagandula, P. Sharma, and S. Banerjee, “DevoFlow: Scaling flow man- agement for high-performance networks,” in Proceedings of the ACM SIGCOMM conference, Toronto, ON, Canada, Aug. 15 - 19 2011, pp. 254–265. [29] H. Mekky, F. Hao, S. Mukherjee, Z.-L. Zhang, and T. Laksh- man, “Application-aware data plane processing in SDN,” in Proceedings of the Third Workshop on Hot Topics in Soft- ware Defined Networking (HotSDN’14), Chicago, Illinois, USA, Aug 2014, pp. 13–18. [30] D. Kotani and Y. Okabe, “A packet-in message filtering mechanism for protection of control plane in OpenFlow switches,” IEICE Transactions on Information and Systems, vol. E99.D, no. 3, pp. 695–707, 2016. [31] C. Schuba, I. Krsul, M. Kuhn, E. Spafford, A. Sundaram, and D. Zamboni, “Analysis of a denial of service attack on TCP,” in Proceedings of the IEEE Symposium on Security and Privacy, Oakland, CA, USA, May 04-07 1997, pp. 208– 223. [32] C. Douligeris and A. Mitrokotsa, “DDoS attacks and defense mechanisms: Classification and state-of-the-art,” Computer Networks, vol. 44, pp. 643–666, 2004. [33] Eddy Wesley M., “Defenses against TCP SYN flooding attacks,” The Internet Protocol Journal, vol. 9, no. 4, pp. 2–16, 2006. [34] Postel, J., “Transmission control protocol, DAPRA internet program - protocol specification, rfc 793,” 1981. [Online]. Available: https://tools.ietf.org/html/rfc793 [35] D. V. Tuyen and T.T. Huong, “A multi-criteria based soft- ware defined networking system architecture for DDoS- attack mitigation,” REV Journal on Electronics and Com- munications, vol. 6, no. 3, pp. 50–60, 2017. [36] The Linux Foundation Projects, “Data plane development kit (DPDK).” [Online]. Available: https://www.dpdk.org [37] J. L. Deng, “Introduction to grey system theory,” The Journal of Grey Systems, vol. 1, no. 1, pp. 1–24, 1989. [38] T. Bohlin, Practical Grey-box Process Identification: Theory and Applications (Advances in Industrial Control). Berlin, Heidelberg, Germany: Springer-Verlag, 2006. [39] E. Kayacan, B. Ulutas, and O. Kaynak, “Grey system theory- based models in time series prediction,” Expert Systems with Applications, vol. 37, no. 2, pp. 1784–1789, 2010. [40] D. Zhang, H. Wang, and K. G. Shin, “Change-point moni- toring for the detection of DoS attacks,” IEEE Transactions on Dependable and Secure Computing, vol. 1, no. 4, pp. 193–208, 2004. [41] J. L. Hellerstein, F. Zhang, and P. Shahabuddin, “A statis- tical approach to predictive detection,” Computer Networks, vol. 35, no. 1, pp. 77–95, 2001. [42] S. Wang, Q. Sun, H. Zou, and F. Yang, “Detecting SYN flooding attacks based on traffic prediction: A demonstration of the security communication networks class file,” Security and Communication Networks, vol. 5, no. 10, pp. 1131– 1140, 2012. [43] The Linux Foundation Collaborative Project, “Open vSwitch.” [Online]. Available: https://www.openvswitch.org [44] Project Floodlight, “Floodlight OpenFlow controller.” [On- line]. Available: [45] M. Goldstein, “BoNeSi: the DDoS botnet simulator.” [Online]. Available: https://github.com/Markus-Go/bonesi [46] W. Foundation, “Wireshark.” [Online]. Available: https:// www.wireshark.org [47] Fred Klassen, “TCPreplay-PCAP editing and replaying utilities.” [Online]. Available: https://tcpreplay.appneta.com Dang Van Tuyen obtained his Bache- lor degree in Electronics and Telecommu- nications in 1999 and Master degree in Telecommunication Engineering in 2008 from Hanoi University of Science and Technology (HUST), Vietnam. He is a lecturer at the Faculty of Electronics and Telecommunications, People’s Police Uni- versity of Technology and Logistics, Ministry of Public Security, Vietnam. Currently, he is pursuing the PhD program in the field of Telecommunication Engineering of HUST. His research interest includes: network security, SDN network, quality of service, wireless sensor network. 21 Research and Development on Information and Communication Technology Truong Thu Huong is Associate Pro- fessor of the School of Electronics and Telecommunication, Hanoi University of Science and Technology (HUST). She is also Vice Director of Elitech, a project to promote all elite education programs of HUST. Truong’s educational, research, and development work is oriented toward next generation networks, protocols and mechanism, traffic analyses, QoE/QoS measuring, green networking and deployment of new integrated multimedia services into fixed and mobile networks, network security and applications in the Internet of Things. She has been serving various international research conferences in dif- ferent roles such as TPC member, publicity chair, organizer, track chair and serving international journals as reviewer. She is also active in capacity building; research and education development. 22
File đính kèm:
 ssg_a_solution_to_prevent_saturation_attack_on_the_data_plan.pdf
ssg_a_solution_to_prevent_saturation_attack_on_the_data_plan.pdf

