A study of blackhole and wormhole attacks in Mobile Ad-Hoc Network
In the Mobile Ad-Hoc Network (MANET), there are several ways of attacking network operation bypassing fault routing information between malicious and normal nodes. It will degrade efficiency of the network so we cannot archive the purposes of the designed MANET. Since it is deployed in an open network environment with characteristics of high mobility, lack of physical security and independent management, the network is vulnerable to attacks. In related works, we have seen a lot of works focusing on single type of attacks but in our paper, we study how routing attacks work and study how we can simulate combination of blackhole and wormhole attacks. Our code will be open to community so others can use to test with its security mechanism or secure routing protocols

Trang 1
Trang 2

Trang 3
Trang 4

Trang 5
Tóm tắt nội dung tài liệu: A study of blackhole and wormhole attacks in Mobile Ad-Hoc Network

ficiency of the network so we
cannot archive the purposes of the designed MANET. Since it is deployed in an open network environment
with characteristics of high mobility, lack of physical security and independent management, the network is
vulnerable to attacks. In related works, we have seen a lot of works focusing on single type of attacks but in
our paper, we study how routing attacks work and study how we can simulate combination of blackhole and
wormhole attacks. Our code will be open to community so others can use to test with its security mechanism
or secure routing protocols.
Keywords: MANET, routing attacks, simulation
1. Introduction* being used widely for both MANET and WSNs
simulation. The methods can be re-used by the
Mobile Ad Hoc Networks (MANET) or
community in other routing protocols to simulate the
Wireless Sensor Networks (WSNs) is a type of
performance of other routing protocols.
wireless network made up of countless mobile nodes
that can communicate with each other without 2. Related works
specialized routers like TCP / IP networks in which
In MANET, an attacker can re-route network
the nodes are both able to act as terminals or acting as
traffic, or inject itself into the path between the source
routers for data communication and information
and destination and thus control the network traffic
transmission [1]. Due to the unique characteristics of
flow so that the networ providers cannot receive data
the MANET network, there are now many routing
sensing. A number of attacks on routing of MANET
protocols designed and dedicated to this network such
have been identified and studied in security research
as the AODV [2] (Ad-hoc On-demand Distance
[5-15]. One of the most common routing attacks in
Vector), DSR [ 3] (Dynamic Source Routing), OLSR
MANET is the Blackhole attack [5-7]. In this attack,
[4] (Optimized Link State Routing Protocol), etc.
a “black” node within the network displays itself as
MANET has the ability to automatically self-
having the shortest path to the destination node. Once
configure which use a peer-to-peer connection or
the packets are drawn to the attacker, they are then
does not need centralized administrator to manage or
dropped instead of relayed, and the communication of
control. Therefore, it is understandable that MANET
the MANET will be disrupted [5-6]. Performance of
is more vulnerable than other networks. There are
AODV and OLSR protocols under Blackhole attack
many types of routing attacks in the MANET
is comparative analysis in [7] but with single static
network, such as blackholes, wormholes, link
Blackhole. In [8], the authors propose a global
spoofing, gray holes, link spoofing, etc. Each attack
reputation system that helps AODV protocol in
has different modes of operation and level of
selecting the best path to destination and also
influence which leads to increased complexity in
consider the situation when Blackhole continuously
prevention and detection. Therefore, understanding
moves.
how the network operation works and analyzes the
system's performance against attacks is always the In wormhole attacks, the attacker receives
first task in the mission to protect MANET network. packets at one point in the network and tunnels them
This article focuses on simulating combination of to another part of the network for malicious purposes.
routing attacks that can occur on MANET or WSNs. In MANET with AODV routing protocol, this attack
We will show how the attack patterns are simulated can be done by tunneling every REQUEST to the
and executed by modifying the AODV and AOMDV target destination node directly. When the
protocols in network emulator tool ns2.35. The tool is destination's neighboring nodes hear this REQUEST
packet, they will rebroadcast that REQUEST packet
in a normal operation and then discard any other
* Corresponding author: Tel.: (+84) 983020981 REQUESTS for the same route discovery [12]. There
Email: hai.tranhoang@hust.edu.vn
48
Journal of Science & Technology 144 (2020) 048-052
is a huge work on the study of how blackhole and be assigned to last host and next hop. The blackhole
wormhole can manipulate the network traffic in node behavior is illustrated in Table 3-4 for AODV
MANET but mostly the authors focus on separate, and AOMDV respectively.
single and static routing attack. In [13], the authors
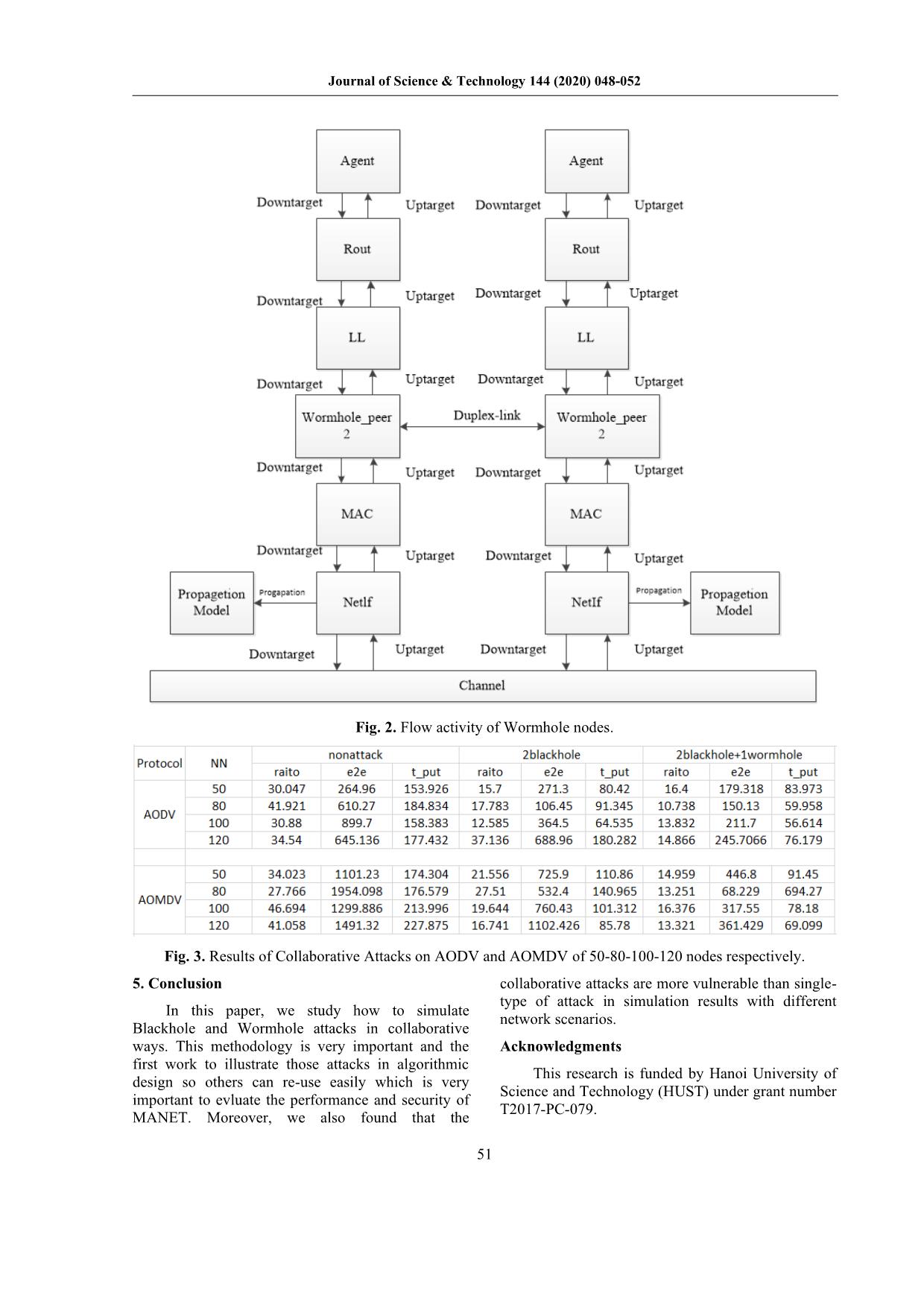
It is difficult for us to simulate Wormhole
alyzed the performance of Mobile Ad-hoc Networks
behavior, we need to update two libraries such as ll.h;
(MANET) under Blackhole and wormhole attack
ll.cc in Table 5-6 respectively. Wormhole_peer is a
separately for AODV protocol. In [14], AODV and
struct data type with 3 parameters which are ll point
DSDV protocols are analyzed in terms of routing
to a link layer; ID and the next pointer points to the
overhead, packet delivery ratio, throughput and end
second worm node in wormhole pair. We define the
to end delay under Blackhole attacks. The authors
main attacking node in wormhole pair is
investigated the performance of the network with
wormhole_peer_head. Wormhole_peer_head is the
single Blackhole attack and collaborative Blackhole
first wormhole node received messages from the
attacks which assume that Blackhole nodes can work
normal node and processing the packet. If the routing
in collaboration. In general, it concludes that AODV
packet forwarded via the wormhole link are data
performs better than DSDV in packet delivery ratio,
packets, there probably more behaviors such as
throughput and routing overhead but the delay of
dropping data packets; forwarding the data packet to
AODV is higher than DSDV.
the destination or forwarding data packet to the
3. Implementation of Collaborative Blackhole and destination and replicating another copy to the
Wormhole attacks on AODV and AOMDV external nodes as malicious behavior.
Table 1. Update on AODV.cc library
• index = id;
• seqno = 2;
• bid = 1;
• LIST_INIT(&nbhead);
• LIST_INIT(&bihead);
• MALICIOUS=false;
• logtarget = 0;
• ifqueue = 0;
Table 2. Setting Blackhole value for a node in
AODV
if(strcmp(argv[1], “blackhole") == 0)
{
Blackhole=True;
return TCL_OK;
}
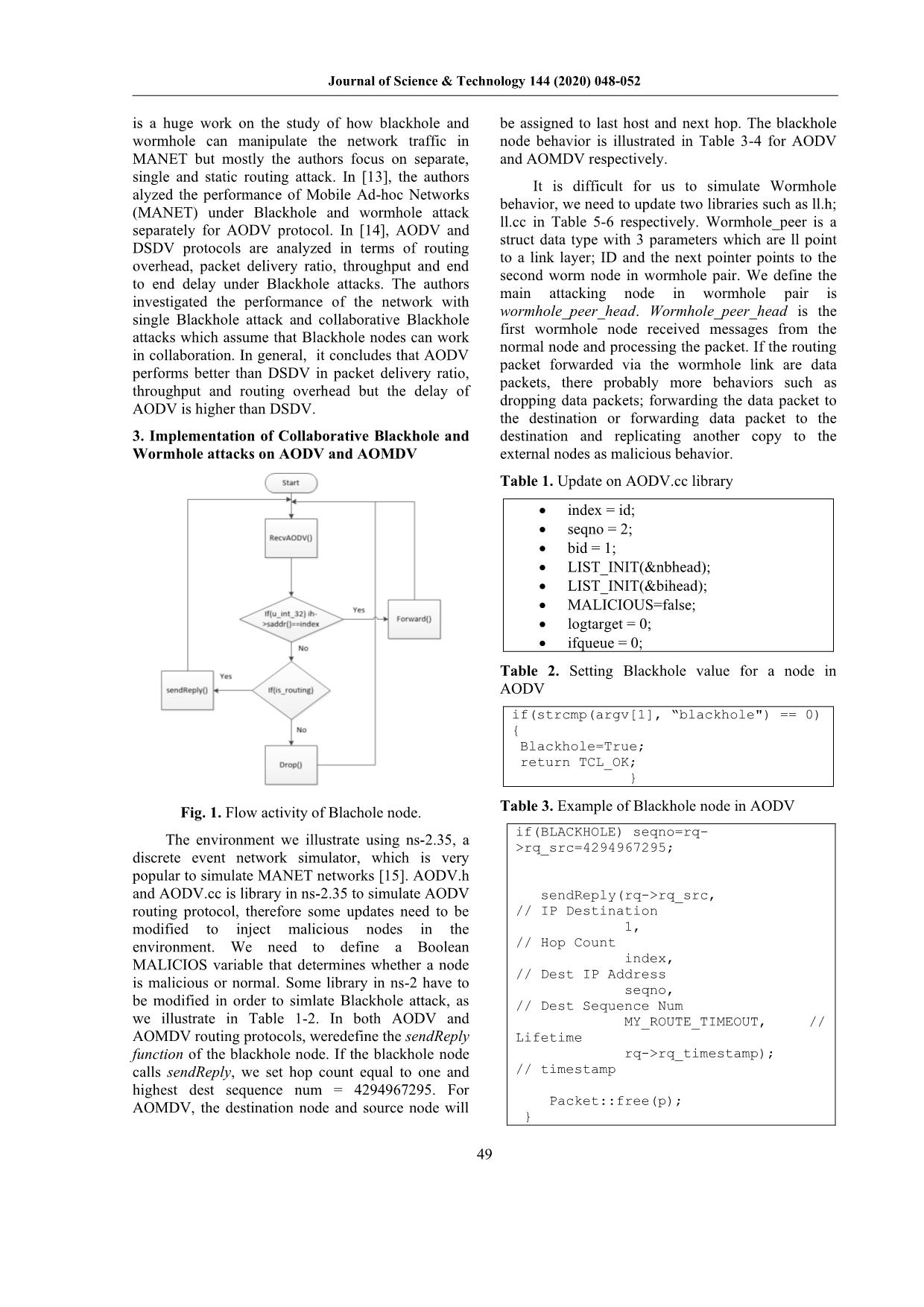
Fig. 1. Flow activity of Blachole node. Table 3. Example of Blackhole node in AODV
if(BLACKHOLE) seqno=rq-
The environment we illustrate using ns-2.35, a >rq_src=4294967295;
discrete event network simulator, which is very
popular to simulate MANET networks [15]. AODV.h
and AODV.cc is library in ns-2.35 to simulate AODV sendReply(rq->rq_src,
routing protocol, therefore some updates need to be // IP Destination
modified to inject malicious nodes in the 1,
environment. We need to define a Boolean // Hop Count
MALICIOS variable that determines whether a node index,
// Dest IP Address
is malicious or normal. Some library in ns-2 have to seqno,
be modified in order to simlate Blackhole attack, as // Dest Sequence Num
we illustrate in Table 1-2. In both AODV and MY_ROUTE_TIMEOUT, //
AOMDV routing protocols, weredefine the sendReply Lifetime
function of the blackhole node. If the blackhole node rq->rq_timestamp);
calls sendReply, we set hop count equal to one and // timestamp
highest dest sequence num = 4294967295. For
Packet::free(p);
AOMDV, the destination node and source node will
}
49
Journal of Science & Technology 144 (2020) 048-052
Table 4. Example of Blackhole node in AOMDV wp->next = wormhole_head.next;
wormhole_head.next = wp;
if(BLACKHOLE) seqno=rq-> if printf( "(%03d) - LL::command - added
(BLACKHOLE) seqno=rq- %d to wormhole peer list\n", mac_-
>rq_src=4294967295; >addr(), wp->id );
return TCL_OK;
}
sendReply(
rq->rq_src, Table 8. Example of wormhole behavior
// IP Destination
1, //from here for Wormhole attack
// Hop Count Scheduler& s =
index, Scheduler::instance();
// (RREQ) Dest IP Address // wormhole decision point (decide if
seqno, this packet is going throught the
// Dest Sequence Num wormhole or not)
MY_ROUTE_TIMEOUT, if( wormhole_head.next
// Lifetime ) {
rq->rq_timestamp, // if( is_broadcast ) {
timestamp // send a copy to each
ih->saddr(), wormhole peer
// nexthop wormhole_peer *wp =
rq->rq_bcast_id, &wormhole_head;
// broadcast id to identify this while( wp->next ) {
route discovery wp = wp->next;
ih->saddr()); Packet *p_copy = p-
>copy();
Packet::free(p); hdr_cmn::access(p_copy)-
} >direction() = hdr_cmn::UP;
s.schedule( wp->ll, p_copy,
Table 5. Update on ll.h library delay_ );
}
if(class LL; ;
typedef struct wormhole_peer_struct {
LL* ll; 4. Results
int id;
struct wormhole_peer_struct* Using our proposed flow activity for Blackhole
next; attack in Figure 1, and Wormhole attack in Figure 1-
} wormhole_peer; 2, and by modifying the libraries in ns2.35, we can
simulate different types of collaborative Blackhole
Table 6. Update on ll.cc library
and Wormhole attacks in different ways to see the
wormhole_head.ll = NULL; impact of these attacks. In general, all properties of
wormhole_head.id = -1; network operation, such as throughput, delay, packet
wormhole_head.next = NULL;; delivery ratio etc. are much worsen by collaborative
Table 7. Example of establishing Wormhole link routing attacks than single type of Blackhole or
Wormhole attack. The results in Figure 3 are network
else if( strcmp( argv[1], "wormhole- performance we collected during implementing
peer" ) == 0 ) { collaborative attacks to evaluate performance of
wormhole_peer* wp =
(wormhole_peer*) malloc( sizeof( AODV and AOMDV routing protocols. More details
wormhole_peer ) ); of the performance of AODV and AOMDV routing
if( !wp ) { protocols under collaborative routing attacks can be
fprintf( found in [16]. We also found that the location of
stderr, "(%03d) - LL::command - error malicious nodes is very important to the impact of
allocating memory for new wormhole these attacks. When nodes are randomly distributed,
peer!" ); malicious nodes seem to appear in the network center
exit(-1); which result in malicious nodes can control more
}
// init fields incoming packets and decreasing transfer rates.
wp->ll = (LL *) Moreover, when the malicious nodes appear in the
TclObject::lookup( argv[2] ); network, the number of neighbor nodes increasing
wp->id = wp->ll->mac_->addr(); leading to malicious nodes penetrating more deeply
into the network. Therefore, the performance
// insert at head of list decreases significantly.
50
Journal of Science & Technology 144 (2020) 048-052
Fig. 2. Flow activity of Wormhole nodes.
Fig. 3. Results of Collaborative Attacks on AODV and AOMDV of 50-80-100-120 nodes respectively.
5. Conclusion collaborative attacks are more vulnerable than single-
type of attack in simulation results with different
In this paper, we study how to simulate
network scenarios.
Blackhole and Wormhole attacks in collaborative
ways. This methodology is very important and the Acknowledgments
first work to illustrate those attacks in algorithmic
This research is funded by Hanoi University of
design so others can re-use easily which is very
Science and Technology (HUST) under grant number
important to evluate the performance and security of
T2017-PC-079.
MANET. Moreover, we also found that the
51
Journal of Science & Technology 144 (2020) 048-052
References Conference on Electronics Computer Technology,
Kanyakumari, 2011, pp. 245-250.
[1] Raja, M.L. and Baboo, C.D.S.S. (2014) An Overview
of MANET: Applications, Attacks and Challenge. [10] Farjamnia, G., Gasimov, Y. & Kazimov, “Review of
the Techniques Against the Wormhole Attacks on
[2] Jhaveri, R.H.; Patel, N.M. (2015). "Mobile Ad-hoc Wireless Sensor Networks”, C. Wireless Pers
Networking with AODV: A Review". International Commun (2019) 105: 1561.
Journal of Next-Generation Computing. 6 (3): 165–
191. [11] Dutta N., Singh M.M. (2019) Wormhole Attack in
Wireless Sensor Networks: A Critical Review. In:
[3] Johnson, David B.; Maltz, David A. (1996). Mandal J., Bhattacharyya D., Auluck N. (eds)
"Dynamic Source Routing in Ad Hoc Wireless Advanced Computing and Communication
Networks". Mobile Computing. The Kluwer Technologies. Advances in Intelligent Systems and
International Series in Engineering and Computer Computing, vol 702. Springer, Singapore.
Science. 353. pp. 153–181.
[12] Raja Datta, Ningrinla Marchang, “Chapter 7 -
[4] Extensions to OSPF to Support Mobile Ad Hoc Security for Mobile Ad Hoc Networks”, Editor(s):
Networking, Madhavi Chandra, Abhay Roy, Mar-10. Sajal K. Das, Krishna Kant, Nan Zhang, Handbook
Computer Science, Volume 3, 2011. on Securing Cyber-Physical Critical Infrastructure,
[5] Gurung, S. & Chauhan, “A survey of black-hole Morgan Kaufmann, 2012.
attack mitigation techniques in MANET: merits, [13] Kumar, Dr Mukesh. (2013). Analysis of Blackhole
drawbacks, and suitability”, S. Wireless Netw (2019). and Wormhole Attack using AODV Protocol.
[6] Elahe Fazeldehkordi, Iraj Sadegh Amiri, Oluwatobi International Journal of Research in Management,
Ayodeji Akanbi, “Chapter 2 - Literature Review”, Science & Technology (E-ISSN: 2321-3264) Vol.1;
Editor(s): Elahe Fazeldehkordi, Iraj Sadegh Amiri, No. 1, June 2013 www.ijrmst.org. 44-28.
Oluwatobi Ayodeji Akanbi, A Study of Blackhole [14] A.A. Chavan, D.S. Kurule, P.U. Dere, Performance
Attack Solutions, Syngress, 2016, Pages 7-57, ISBN Analysis of AODV and DSDV Routing Protocol in
9780128053676. MANET and Modifications in AODV against
[7] K.S. Praveen, H.L. Gururaj, B. Ramesh, Blackhole Attack, Procedia Computer Science,
“Comparative Analysis of Blackhole Attack in Ad Volume 79, 2016.
Hoc Network Using AODV and OLSR Protocols”, [15] Henderson, Tom (2012-06-09). "upcoming ns-2.35
Procedia Computer Science, Volume 85, 2016. release" (Mailing list). ns-235 GSoC 2015 students.
[8] Qussai M. Yaseen, Monther Aldwairi, “An Enhanced Archived from the original on 2012-03-27. Retrieved
AODV Protocol for Avoiding Blackholes in 2013-05-31.
MANET”, Procedia Computer Science, Volume 134, [16] Tran Hoang Hai, Nguyen Dang Toi, Eui-nam Huh
2018, Pages 371-376. (2019) Performance Evaluation of AODV and
[9] P. Nagrath and B. Gupta, "Wormhole attacks in AOMDV Routing Protocols Under Collaborative
wireless adhoc networks and their counter Blackhole and Wormhole Attacks, Advances in
measurements: A survey," 2011 3rd International Computer Science and Ubiquitous Computing. CUTE
2019, CSA 2019.
52 File đính kèm:
 a_study_of_blackhole_and_wormhole_attacks_in_mobile_adhoc_ne.pdf
a_study_of_blackhole_and_wormhole_attacks_in_mobile_adhoc_ne.pdf

