Secure localization against malicious attacks on wireless sensor network
Abstract:
Wireless sensor networks (WSN) are very susceptible to location errors due to malicious attacks on
sensor nodes that distort the position of the sensor nodes, which will lead to an error during unknown
node localization. In this paper, we propose a localization algorithm to defend against independent
attacks and collusion attacks. In the algorithm, we first select three random reference nodes, then use the
trilateral detection method and the confidence interval to get rid of the malicious nodes. We then use the
PSO optimization algorithm to locate the unknown node, is called (Secure localization algorithm against
advanced attacks-SL4A). Through the simulation results, we prove that our proposed algorithm outperforms the existing algorithms, in terms of the variability of malicious nodes and noise, average localization error and degree computational complexity.

Trang 1
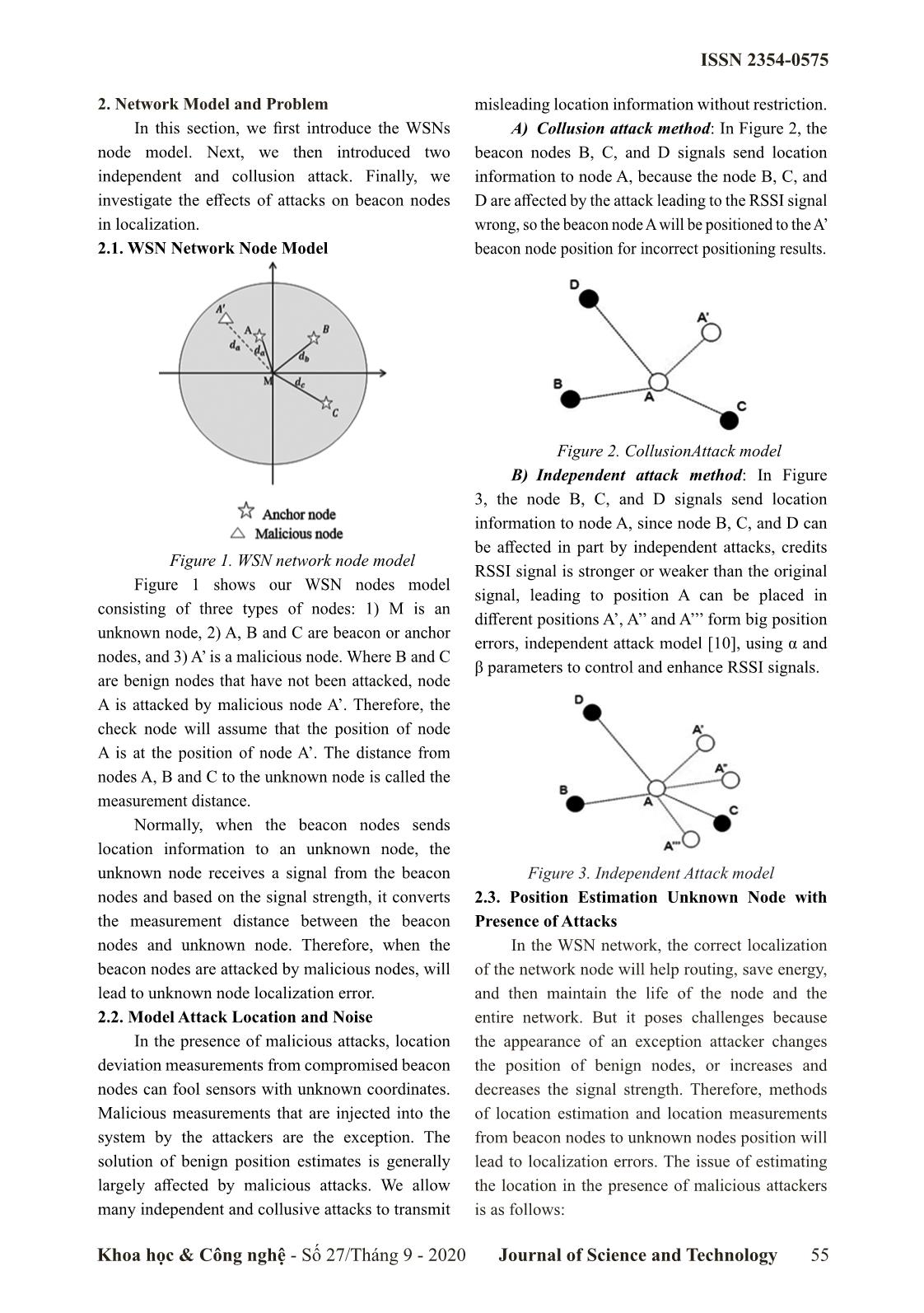
Trang 2

Trang 3

Trang 4
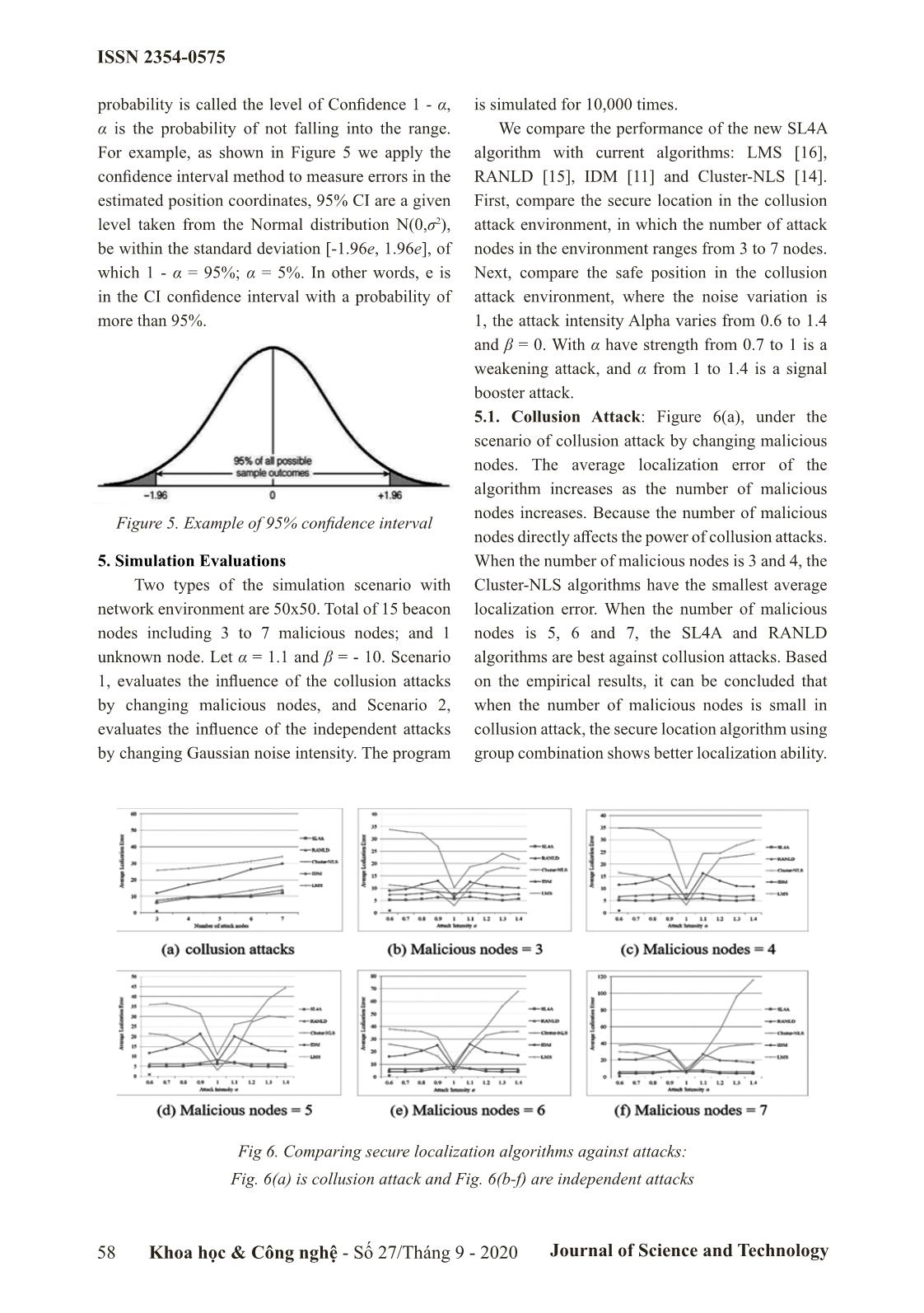
Trang 5

Trang 6

Trang 7
Tóm tắt nội dung tài liệu: Secure localization against malicious attacks on wireless sensor network

e. Assume, in an N-dimensional objective search space. Three N-dimensional vectors are used to describe a particle i: (1) current location Xi = [xi1, xi2, xiN]; (2) the previous location Pbesti = [pi1, pi2, , piN] of the best fitness; and (3) current velocity Vi = [Vi1, Vi2, , ViN] . Besides, Gbest = [G1, G2, , GN] denotes the position of the best particle so far (ie, Gbestd is the smallest of all Pbestid). At each iteration k, the velocity vid and position Xid of each particle are updated according to the following equations. 1 1 2 2( 1) ( ) ( ) ( )id id id id d idV k V k c r Pbest X c r Gbest Xw (3) ( 1) ( ) ( 1)id id idX k X k V k (4) where, d =1,2, , N; i=1, 2, , K; and K is the size of the swarm population, it is denotes iteration number, r 1 and r 2 are random numbers between [0,1], and c 1 =c 2 =2 are respectively the cognitive and social learning parameters, ω is the inertia weight. The inertial weight is added to element w of the original PSO algorithm as in Eq. (5). The bigger value of ω is beneficial for particles to jump out of local minimum points, the smaller value of ω is favor the algorithm convergence. As originally developed, ω often decreases linearly with the number of iterations. Therefore, ω can be set according to the following equation. max max ( ) (5)ini end end T t T w ww w where iniw is the initial weigh. endw is the final weight value, maxT is the total number of iterations, and t is the current number of iterations. In previous experimental studies, ω was often set from 0.9 reducing linearly to 0.4. 4. Secure Localization Algorithm Against Advanced Attacks (SL4A) Existing algorithms for estimating attack resistance positions often use as many beacon nodes as possible to estimate unknown node coordinates [12], [8]. The idea behind the algorithm LS4A is that we select three random points for an initial subset, using the trilateral detection paradigm and the PSO optimization algorithm to identify measurements in confidence intervals. To find the coordinates of a node requires at least 3 distance measurements. Therefore, to estimate the position of an unknown node from a randomly chosen subset of 3 nodes, Ωi (Step 4). In ISSN 2354-0575 Khoa học & Công nghệ - Số 27/Tháng 9 - 2020 Journal of Science and Technology 57 an attack network model, any node can be attacked, so that to detect an attack beacon node, (Step 5) uses the trilateral detection method to detect whether a set Ωi has been maliciously attacked. If the set Ωi is not attacked (Step 6) use the PSO algorithm to find the location estimate. Next (Step 7), calculate the K value by the Equations (7), of all cases falling into the confidence interval e. When K = N, the estimated location ofc 0Z is within the confidence interval of all the beacons, and its coordinates are completely removed by malicious attacks. 1 ( 1.96 1.96),1 where (7) ,0 N i i i i if e K u u otherwise= − ≤ ≤ = = = ∑ If the value of K is greater than the threshold value of t given (Step 8). Once a consistency set has been identified, the algorithm uses all points in the confidence interval set to form the final estimate ofc 0Z and it terminates (Steps 9). In our experiments, we use the PSO optimization algorithm to calculate the initial estimate from the Zi subset and for the final estimate obtained from the set within the confidence interval. If the algorithm performs all iterations and does not find the confidence interval have a minimum size t. Then it will either declare a failure or give an 0Z position estimate acceptable from the largest confidence interval (Steps 13). Algorithm Secure Localization Algorithm Against Advanced Attacks (SL4A) 1: Input: unknown node Z 0 , maximum number of interations imax, Set L, confidence interval CI, threshold t; 2: Ouput: estimated positionc 0Z 0 0( , )x y ; 3: for iter=0 to imax do 4: Randomly select a subset Ωi of size 3 from L; 5: if TriEdgeCheck(Ωi) then 6: Call PSO-Based Localization Algorithm; 7: Calculate K, the number of points in the confidence interval with to the estimatedc 0Z in e; 8: if K > t then 9: return 0 0( , )x y ; 10: end if 11: end if 12: end for 13: return 0 0( , )x y ; 4.1. The Trilateral Detection Method: [13] is derived from a beacon node detection method developed from the theorem of a triangle. The total 2 sides of the triangle are larger than the third side, and the subtraction of 2 sides of the triangle is smaller than the third side. Given a triangle ∆ABC and the corresponding edges are a, b, c, the three sides must satisfy a + b > c, a + c > b, b + c > a, a − b < c, a − c < b and b − c< a. Figure 4. The trilateral detection method For example, in Figure 4 M is called an unknown node or a measured node, A and B are anchor nodes that provide positioning information. M node is measured uses RSSI signal strength to convert the distance between A and B anchor nodes into dAM distance and dBM, and then use the known distance dAB to perform trilateral detection, then assess whether or not to meet the principles of a triangle. 4.2. Confidence Interval (CI): We assume that not all beacon nodes are attacked by malicious nodes, meaning that non-toxic distance measurement errors are Gaussian random variables distributed according to N(0,σ2), error variance is the RSSI distance measurement technique in this paper. The distance measurement error e computes the distance between the actual position of with the reference position (xi , yi) according to the Equations (8). 2 2 0 0( ) ( ) (8)i i ie d x x y y= − − + − In statistics, the confidence interval of the probability sample means estimating the interval of some of the overall parameters of the sample [17]. The confidence interval is a distance estimation method that uses a range to estimate a parameter. This shows that the true value of this parameter is likely to fall into the measurement result, the ISSN 2354-0575 Journal of Science and Technology58 Khoa học & Công nghệ - Số 27/Tháng 9 - 2020 probability is called the level of Confidence 1 - α, α is the probability of not falling into the range. For example, as shown in Figure 5 we apply the confidence interval method to measure errors in the estimated position coordinates, 95% CI are a given level taken from the Normal distribution N(0,σ2), be within the standard deviation [-1.96e, 1.96e], of which 1 - α = 95%; α = 5%. In other words, e is in the CI confidence interval with a probability of more than 95%. Figure 5. Example of 95% confidence interval 5. Simulation Evaluations Two types of the simulation scenario with network environment are 50x50. Total of 15 beacon nodes including 3 to 7 malicious nodes; and 1 unknown node. Let α = 1.1 and β = - 10. Scenario 1, evaluates the influence of the collusion attacks by changing malicious nodes, and Scenario 2, evaluates the influence of the independent attacks by changing Gaussian noise intensity. The program is simulated for 10,000 times. We compare the performance of the new SL4A algorithm with current algorithms: LMS [16], RANLD [15], IDM [11] and Cluster-NLS [14]. First, compare the secure location in the collusion attack environment, in which the number of attack nodes in the environment ranges from 3 to 7 nodes. Next, compare the safe position in the collusion attack environment, where the noise variation is 1, the attack intensity Alpha varies from 0.6 to 1.4 and β = 0. With α have strength from 0.7 to 1 is a weakening attack, and α from 1 to 1.4 is a signal booster attack. 5.1. Collusion Attack: Figure 6(a), under the scenario of collusion attack by changing malicious nodes. The average localization error of the algorithm increases as the number of malicious nodes increases. Because the number of malicious nodes directly affects the power of collusion attacks. When the number of malicious nodes is 3 and 4, the Cluster-NLS algorithms have the smallest average localization error. When the number of malicious nodes is 5, 6 and 7, the SL4A and RANLD algorithms are best against collusion attacks. Based on the empirical results, it can be concluded that when the number of malicious nodes is small in collusion attack, the secure location algorithm using group combination shows better localization ability. Fig 6. Comparing secure localization algorithms against attacks: Fig. 6(a) is collusion attack and Fig. 6(b-f) are independent attacks ISSN 2354-0575 Khoa học & Công nghệ - Số 27/Tháng 9 - 2020 Journal of Science and Technology 59 5.2. Independent attack: Figure 6(b) to Figure 6(f) with the scenario of independent attacks by changing Gaussian noise intensity. In the cases of number of attack nodes changer from 3 to 7 nodes. We can see that when the attack intensity α = 0.9 and α = 1.1, all algorithms are affected by the worst attacks power. With different attack intensities, the SL4A and RANLD algorithms have the smallest average localization error. IDM algorithm randomly chooses 5 nodes to estimate position. Therefore, the average localization error in the middle. As the signal strength increased, the Cluster-NLS and LMS algorithms had average localization errors increased accordingly. 6. Conclusions In WSNs there is practically a lot of noise caused by malicious attacks on anchor nodes. Most localization algorithms are suffer from malicious attacks, resulting in a large difference between the estimated location and the actual location of an unknown node. However, there are a few localization algorithms that considers independent attack mechanisms, due to inappropriate algorithmic architectural design, the ability to resist malicious attacks is limited and the complexity of the algorithm is too high compared to hardware devices. In this paper, we have proposed a anti-attack security algorithms SL4A with stability and robustness, algorithm focused on combating independent attacks and collusion attacks. Compared to existing secure localization algorithms, our two algorithms resist malicious attacks and calculate the location coordinates of the unknown node more accurately. References [1]. Y.S.I.F.Akyildiz,W.SuandE.Cayirci,“Asurveyonsensornetworks,” IEEE Communications Magazine, 2002, vol. 40, no. 8, pp. 102–114. [2]. L.Doherty and K. Pister, “Convex position estimation in wireless sensor networks,” in Proceeding of IEEE International Conference on Computer and Communications Societies (INFOCOM), 2001, vol. 3, pp. 1655–1663. [3]. T. He and C. Huang, “Range-free localization schemes for large scale sensor networks,” ACM MobiCom, San Diego, 2003, pp. 81–95. [4]. D. Niculescu and B. Nath, “Dv based positioning in ad hoc networks,” Telecommunication Systems, 2003, vol. 22, no. 1, pp. 267–280. [5]. C. H. Chang and W. Liao, “A probabilistic model for relative location estimation in wireless sensor networks,” IEEE Communications Letters, 2009, vol. 13, no. 12, pp. 893–895. [6]. O.M.R.Weber,E.MademannandS.Zeisberg,“Localizationtechniques for traffic applications based on robust wecols positioning in wireless sensor networks,” Proceedings of Workshop on Positioning Navigation and Communication (WPNC), 2012, pp. 215–219. [7]. J. Cao, “A localization algorithm based on particle swarm optimization and quasi-newton algorithm for wireless sensor networks,” Journal of Communication and Computer 12, 2015, pp. 85–90. [8]. J. M.-S. . E. R.-I. . A. E.-R. . L. Rizo-Dominguez, “A comparative of range free localization algorithms and dv-hop using the particle swarm optimization algorithm,” in 2017 IEEE 8th Annual Ubiquitous Computing, Electronics and Mobile Communication Conference (UEMCON), 2017, no. 17489361, pp. 150–157. [9]. W. T. Y. Chen and R. Martin, “Attack detection in wireless localization,” in Proceeding of IEEE International Conference on Computer Communications (INFOCOM), 2007, pp. 1964–1972. [10]. S. U. M. Jadliwala, S. Zhong and C. Qiao, “Secure distance-based localization in the presence of cheating beacon nodes,” IEEE Transactions on Mobile Computing, 2010, vol. 9, no. 6, pp. 810–823. [11]. C. C. C. S. H. Fang and C. Wang, “Attack-resistant wireless localization using an inclusive ISSN 2354-0575 Journal of Science and Technology60 Khoa học & Công nghệ - Số 27/Tháng 9 - 2020 disjunction model,” IEEE Transactions on Communications, 2012, vol. 60, no. 5, pp. 1209–1214. [12]. L. S. J. Jiang, G. Han and H. C. Chao, “A novel secure localization scheme against collaborative collusion in wireless sensor networks,” Proceedings of Wireless Communications and Mobile Computing Conference (IWCMC), 2011, pp. 308–303. [13]. J. H. N. Bulusu and D. Estrin, “Gps-less low cost outdoor localization for very small devices,” GPS-less low cost outdoor localization for very small devices, 2000, vol. 7, no. 5, pp. 28–34. [14]. V. B. L. J. Yang, Y. Chen and V. Swaminathan, “Robust wireless localization to attacks on access points,” Proceeding of IEEE Sarnoff Symposium, 2009, pp. 208–212. [15]. N. Kiyavash and F. Koushanfar, “Anti-collusion position estimation in wireless sensor networks,” in Proceedings of IEEE International Conference on Mobile Adhoc and Sensor Systems, 2007, pp. 1–9. [16]. Y. Z. Z. Li, W. Trappe, “Robust statistical methods for securing wireless localization in sensor networks,” in IPSN 2005. Fourth International Symposium on Information Processing in Sensor. [17]. Wikipedia, Confidence interval, 2008, https://en.wikipedia.org/wiki/ Confidence interval. BẢN ĐỊA HÓA AN TOÀN CHỐNG LẠI CÁC CUỘC TẤN CÔNG ĐỘC HẠI VÀO MẠNG CẢM BIẾN KHÔNG DÂY Tóm tắt: Mạng cảm biến không dây (WSN) rất dễ bị lỗi vị trí do các cuộc tấn công độc hại vào các nút cảm biến làm sai lệch vị trí của các nút cảm biến, điều này sẽ dẫn đến lỗi trong quá trình nội địa hóa nút không xác định. Trong bài báo này, chúng tôi đề xuất thuật toán bản địa hóa để chống lại các cuộc tấn công độc lập và các cuộc tấn công thông đồng. Trong thuật toán, đầu tiên chúng tôi chọn ba nút tham chiếu ngẫu nhiên, sau đó sử dụng phương pháp phát hiện ba bên và khoảng tin cậy để loại bỏ các nút độc hại. Sau đó chúng tôi sử dụng thuật toán tối ưu hóa PSO để xác định vị trí nút không xác định, được gọi là (Secure localization algorithm against advanced attacks-SL4A). Thông qua kết quả mô phỏng, chúng tôi chứng minh rằng thuật toán đề xuất của chúng tôi có hiệu suất tốt hơn các thuật toán hiện có, về sự thay đổi của các nút độc hại và nhiễu, lỗi cục bộ hóa trung bình và độ phức tạp tính toán. Từ khóa: Wireless sensor network (WSNs), Secure Location, Independent Attack, Collusion Attack.
File đính kèm:
 secure_localization_against_malicious_attacks_on_wireless_se.pdf
secure_localization_against_malicious_attacks_on_wireless_se.pdf

