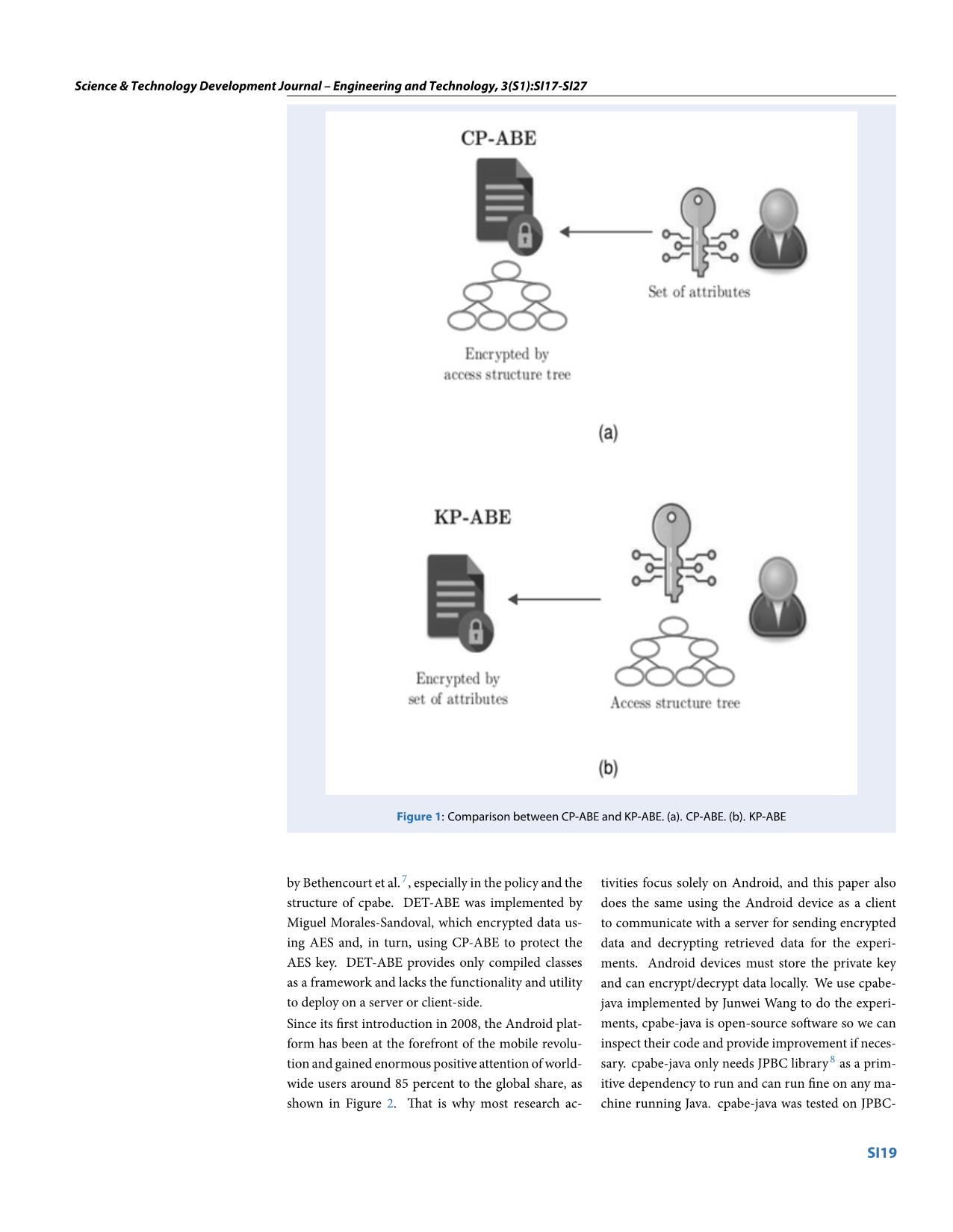
Applying attribute-Based encryption on mobile devices
The 21st century has witnessed the rapid development of small and convenient mobile devices
such as smartphones, tablets, game players, sensor nodes, etc. The rise of such mobile devices
indicates the increase of colossal data transmission through the Internet and online services along
with the challenges of data security. It is common to think of a solution to protect sensitive data
from unauthorized users, and the most popular solution is to use encryption. While many research
activities in functional encryption have widely been applied to network devices, computers, and
applications, mobile devices still attract much attention to security issues due to the limitations of
system resources, connectivity, data transmission and power consumption that malicious users can
exploit to launch attacks. Especially, mobile devices have become a principal tool to share data on
the Internet through online services, such as Facebook, Youtube, DropBox, Amazon, Online Games,
etc. This paper presents a study of the Attribute-Based Encryption (ABE) scheme that exploits user
attributes to build the secret key and the ciphertext. ABE encryption is specified by a set of attributes
or a policy defining attributes that users possess. The paper also describes a few implementations of
ABE applied in the cryptography community and the challenges of integrating ABE into real-world
applications. Finally, the paper proposes an implementation of ABE for Android mobile devices.
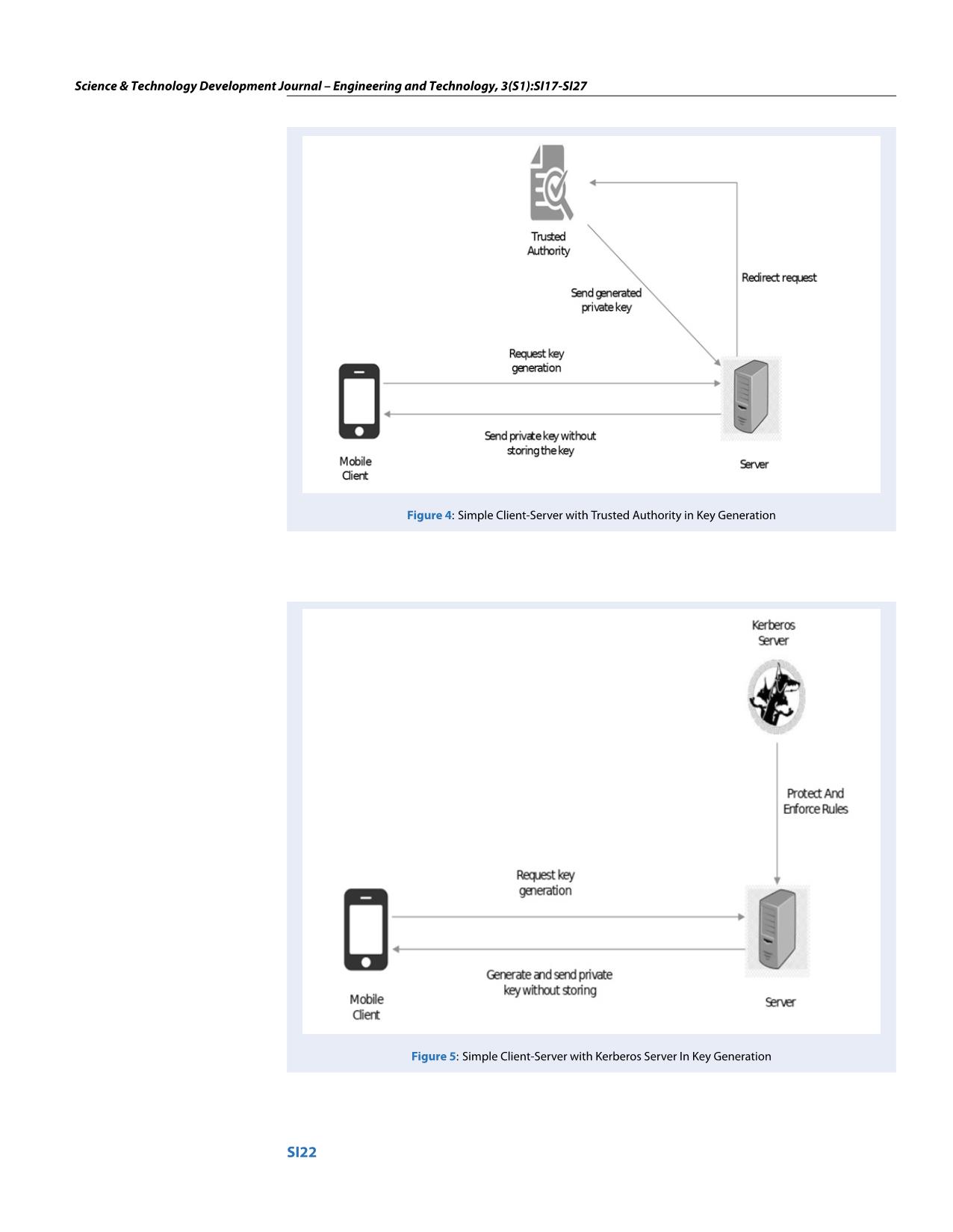
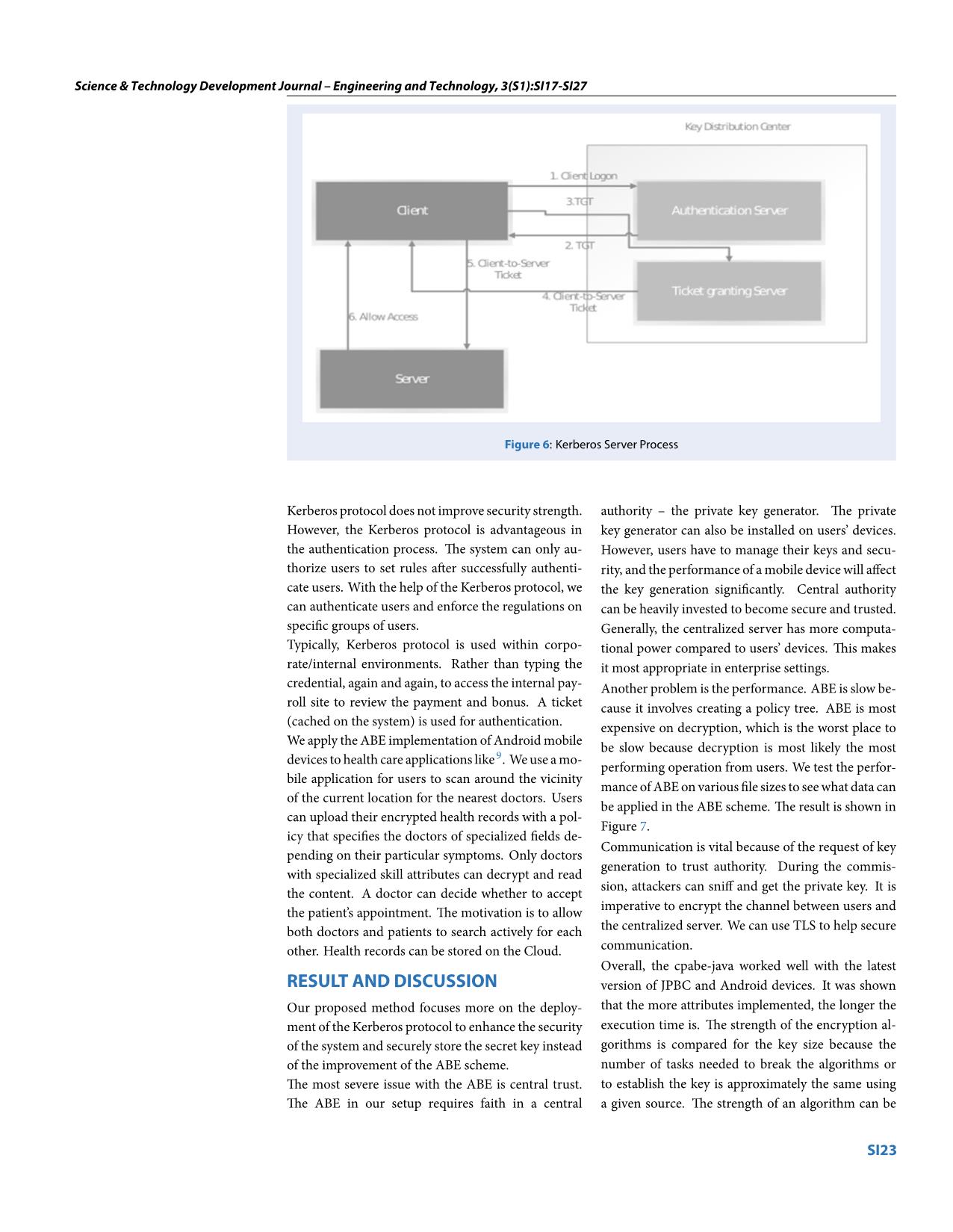
This implementation associated with the Kerberos protocol can be applied to secured data sharing
applications. The Kerberos protocol aims at providing mutual authentication for the client server
model. Experiments have evaluated the proposed ABE implementation on Android mobile devices
along with the Kerberos system. The evaluation also includes ABE performance with discussions
and lessons learned.

Trang 1

Trang 2
Trang 3

Trang 4
Trang 5
Trang 6
Trang 7
Trang 8

Trang 9

Trang 10
Tải về để xem bản đầy đủ
Tóm tắt nội dung tài liệu: Applying attribute-Based encryption on mobile devices

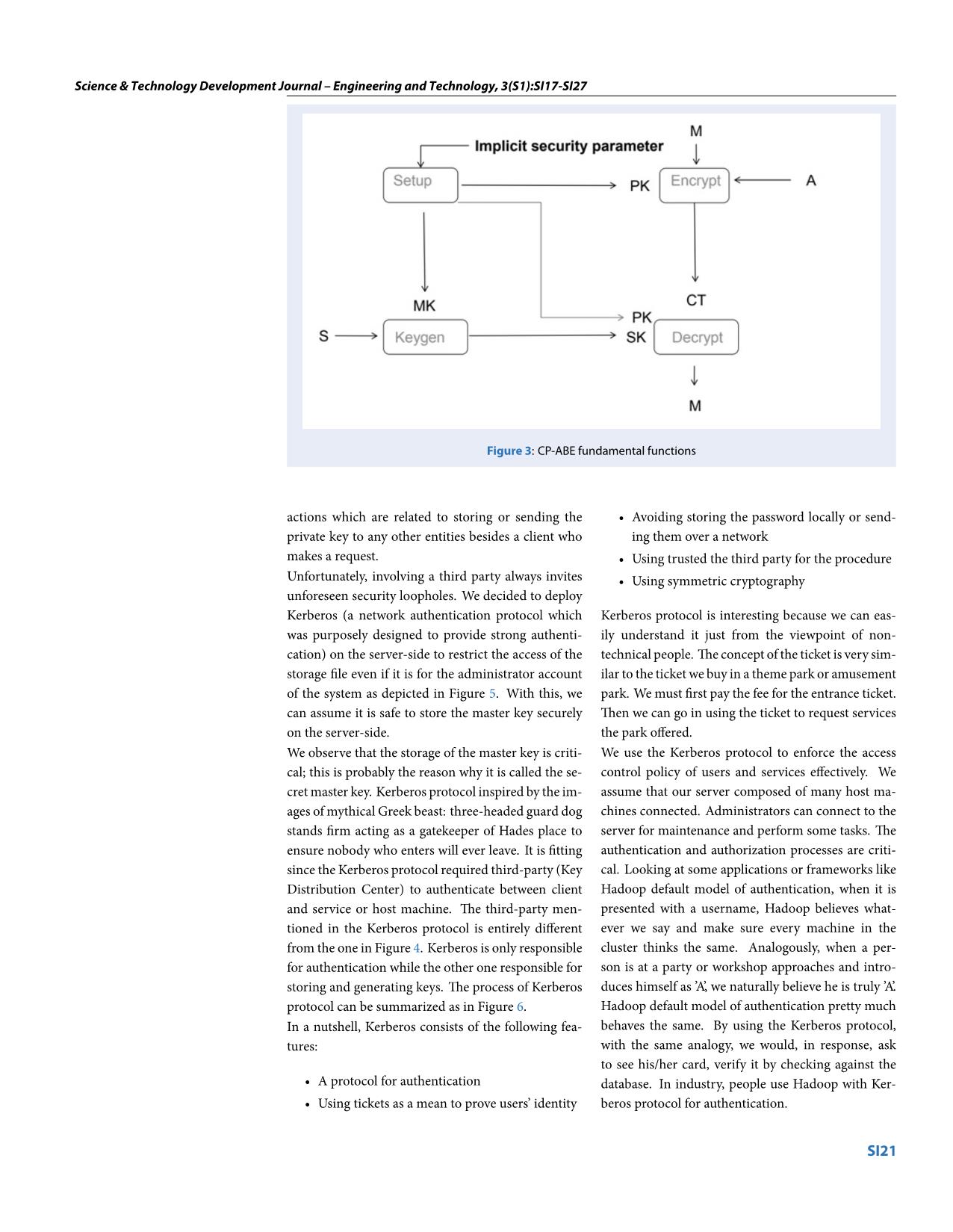
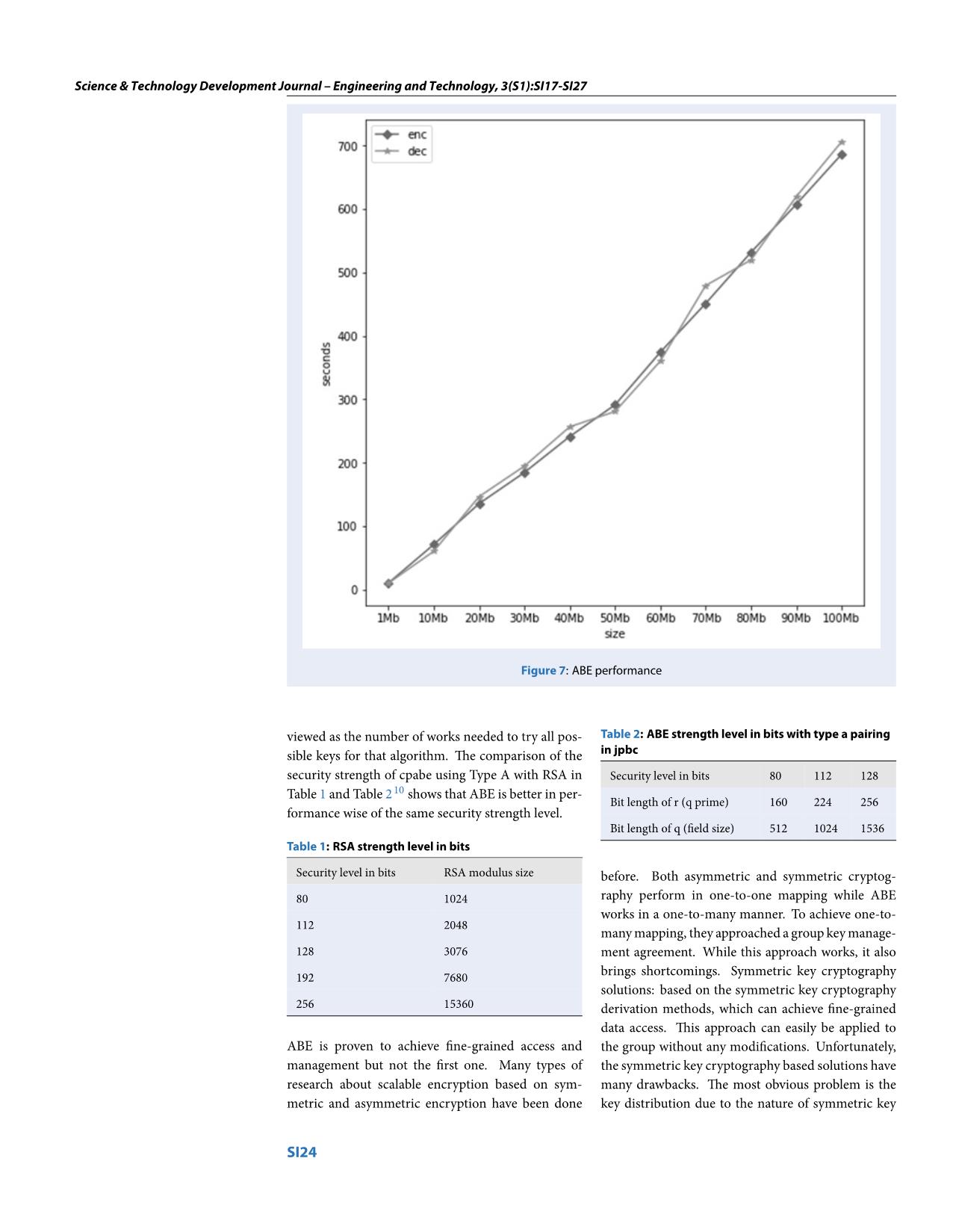
e 9. Weuse a mo- performing operation from users. We test the perfor- bile application for users to scan around the vicinity mance of ABE on various file sizes to see what data can of the current location for the nearest doctors. Users be applied in the ABE scheme. The result is shown in can upload their encrypted health records with a pol- Figure 7. icy that specifies the doctors of specialized fields de- Communication is vital because of the request of key pending on their particular symptoms. Only doctors generation to trust authority. During the commis- with specialized skill attributes can decrypt and read sion, attackers can sniff and get the private key. It is the content. A doctor can decide whether to accept the patient’s appointment. The motivation is to allow imperative to encrypt the channel between users and both doctors and patients to search actively for each the centralized server. We can use TLS to help secure other. Health records can be stored on the Cloud. communication. Overall, the cpabe-java worked well with the latest RESULT AND DISCUSSION version of JPBC and Android devices. It was shown Our proposed method focuses more on the deploy- that the more attributes implemented, the longer the ment of the Kerberos protocol to enhance the security execution time is. The strength of the encryption al- of the system and securely store the secret key instead gorithms is compared for the key size because the of the improvement of the ABE scheme. number of tasks needed to break the algorithms or The most severe issue with the ABE is central trust. to establish the key is approximately the same using The ABE in our setup requires faith in a central a given source. The strength of an algorithm can be SI23 Science & Technology Development Journal – Engineering and Technology, 3(S1):SI17-SI27 Figure 7: ABE performance viewed as the number of works needed to try all pos- Table 2: ABE strength level in bits with type a pairing sible keys for that algorithm. The comparison of the in jpbc security strength of cpabe using Type A with RSA in Security level in bits 80 112 128 Table 1 and Table 2 10 shows that ABE is better in per- Bit length of r (q prime) 160 224 256 formance wise of the same security strength level. Bit length of q (field size) 512 1024 1536 Table 1: RSA strength level in bits Security level in bits RSA modulus size before. Both asymmetric and symmetric cryptog- 80 1024 raphy perform in one-to-one mapping while ABE works in a one-to-many manner. To achieve one-to- 112 2048 many mapping, they approached a group key manage- 128 3076 ment agreement. While this approach works, it also 192 7680 brings shortcomings. Symmetric key cryptography solutions: based on the symmetric key cryptography 256 15360 derivation methods, which can achieve fine-grained data access. This approach can easily be applied to ABE is proven to achieve fine-grained access and the group without any modifications. Unfortunately, management but not the first one. Many types of the symmetric key cryptography based solutions have research about scalable encryption based on sym- many drawbacks. The most obvious problem is the metric and asymmetric encryption have been done key distribution due to the nature of symmetric key SI24 Science & Technology Development Journal – Engineering and Technology, 3(S1):SI17-SI27 cryptography, which employs identical keys for both ABE is best suited in situations where an encrypted encryption and decryption. Users either have to ei- file involved multiple parties, for example, nurses, ther manually meet face-to-face for trustworthy se- doctors, family members can gain access to a patient’s cret sharing of the key or require a secure key agree- health record but with different privilege levels; or ment protocol like 11. The complicated process leads when to broadcast without regards to recipients: mili- to high management overhead and time consuming tary operations, a Facebook personal circle of friends. when there is a large number of users. With this kind Many types of research also apply ABE in IoT 13. of solution, we can see that user revocation of privi- ABE should not be used for any applications that lege level access is not supported since the keys have require identity ensuring, for example, Blockchain. already been known to all. In case the user revoca- However, the ABE scheme can represent any individ- tion is a must, this can be done. However, it is very ual by using many personal attributes of an individual inefficient; upon the dismissal of one user, all the re- that are very difficult to forge: fingerprint, retina, face, maining users are also affected and have to generate a voice, hardware id, etc. Currently, ABE implemen- different set of keys, data also need to be re-encrypted. tations only support string and numerical data types. Public key cryptography based solutions: based on Converting these unique attributes requires in-depth the asymmetric cryptography derivation methods, knowledge, specialized skill, and complicated process. using for group key, also have many drawbacks. The Besides, determining the number of attributes for a key distribution is not a big problem now. Unfor- specific application is another problem that needs to tunately, asymmetric cryptography requires the keys be addressed adequately. must be many times longer than key in symmetric cryptography counterpart to boost the equivalent se- CONCLUSION curity level, which is more computationally costly. We have provided an implementation of the ABE The key management overhead is still potentially high scheme for Android mobile devices with the Kerberos and is vulnerable to a collusion attack. Collusion at- protocol and evaluated several security features for se- tack is the execution of operations to combine many cured data sharing and performance of ABE on vari- parts of the known keys to create a new key capable ous file sizes. With the increasing expansion of cloud of decrypting the file. Jikai Teng and Chuanku Wu computing, IoT, mobile devices, this study can be ap- researched the collusion attack on asymmetric group plied for data security and privacy protection. ABE key 12. has proved its advantages in many practical applica- In conclusion, both asymmetric and symmetric have tions. ABE can also be applied to mobile devices, but high overhead key management as the complexities soon becomes more and more popular in mobile com- of key creation, and user revocation to the number of puting applications. Libraries and frameworks are im- users is a positive correlation (the higher number of plemented to help visualize this scheme. Future work users is, the more complexity in key generation and focuses on selecting several appropriate attributes for user revocation). ABE is proven to overcome this ad- the ABE scheme. versity. Questions raised ABE is susceptible to collu- sion attack by multiple users collect sufficient infor- ACKNOWLEDGEMENT mation and combined many private keys to decrypt This research activity is funded by Vietnam National data. Fortunately, ABE is resistant to this attack, as described in 7. We observe that in the key generation University in Ho Chi Minh City (VNU-HCM) under process, each user is assigned a random parameter the grant number C2019-28-06. value, which is then embedded in the private key. So, ABBREVIATION using different private keys means different parameter values in the decryption process, thus yields in failure. ABE Attribute-Based Encryption ABE also has a fair share of doubt about susceptible to AES AES Encryption Algorithm insider attack by investigating required attributes then CP-ABE Ciphertext-Policy ABE create a new key. Creating a new key from scratch DET-ABE Digital Envelop Technique ABE with knowledge of exact attributes also yields in fail- IoT Internet of Things ure as the associated master key is needed to generate KP-ABE Key-Policy ABE a private key. A server or Trusted Authority depended LSSS Linear Secret Sharing Scheme on the paradigm securely stores the master key. Typi- RSA RSA Encryption Algorithm cally, users do not have any means to grasp the master TA Trusted Authority key to generate a new private key. TLS Transported Layer Security SI25 Science & Technology Development Journal – Engineering and Technology, 3(S1):SI17-SI27 CONFLICT OF INTEREST based encryption. In Naeem Raja Akram and Sushil Jajodia, editors, Infor- mation Security Theory and Practice: 9th IFIP The authors declare that there is no conflict of interest WG 11.2 International Conference, WISTP 2015, pages 104- 119, Heraklion, Crete, Greece, 2015. Springer International Publishing;Available from: https://doi.org/10.1007/978-3-319- AUTHORS’ CONTRIBUTIONS 24018-3_7. 6. Wang J. Java realization for ciphertext-policy attribute-based N. T. Dang wrote the manuscript and provided data encryp- tion. 2012;. for Tables I and II. H. D. Le checked the ABE algo- 7. Bethencourt J, Sahai A, Waters B. Ciphertext-policy attribute- based encryption. 2007 IEEE Symposium on Security and Pri- rithm with the Kerberos protocol. S. T. Le conducted vacy (SP ’07). 2007;p. 321–334. Available from: https://doi.org/ ABE implementation on Android mobile devices. H. 10.1109/SP.2007.11. M. Tran conducted secured data sharing scenarios for 8. Caro AD, Iovino V. jpbc: Java pairing based cryptography. In Proceedings of the 16th IEEE Symposium on Computers and the ABE scheme and provided evaluation analysis. All Commu- nications, ISCC 2011, pages 850-855, Kerkyra, Corfu, authors reviewed the final manuscript. Greece, June 28-July 1, 2011. IEEE;Available from: https://doi. org/10.1109/ISCC.2011.5983948. REFERENCES 9. Balapure SR, Khodke PA. Privacy preservation of e-health care system in cloud. 2017;. 1. Boneh D, Sahai A, Waters B. Functional encryption: a new vi- 10. Hemalatha SB, Manickachezian R. Security strength of rsa and sion for public-key cryptography. Commun ACM. 2012;55:56– attribute-based encryption for data security in cloud comput- 64. Available from: https://doi.org/10.1145/2366316.2366333. ing. 2014;. 2. Sahai A, Waters B. Fuzzy identity based encryption. In IACR 11. Teng J, Wu C. A collusion attack on asymmetric group Cryptology ePrint Archive. 2004;Available from: https://doi. key exchange. Security and Communication Networks. org/10.1007/11426639_27. 2015;8:2189–2193. Available from: https://doi.org/10.1002/ 3. Goyal VK, Pandey O, Sahai A, Waters B. Attribute-based en- sec.1163. cryption for fine-grained access control of encrypted data. 12. Teng J, Wu C. A collusion attack on asymmetric group IACR Cryptology ePrint Archive. 2006;309:2006. Available key exchange. Security and Communication Networks. from: https://doi.org/10.1145/1180405.1180418. 2015;8:2189–2193. Available from: https://doi.org/10.1002/ 4. Ambrosin M, Conti M, Dargahi T. On the feasibility of sec.1163. attribute- based encryption on smartphone devices. In IoT- 13. Ambrosin M, Anzanpour A, Conti M, Dargahi T, Moosavi SR, Sys@MobiSys. 2015;Available from: https://doi.org/10.1145/ Rahmani A, et al. On the feasibility of attribute-based encryp- 2753476.2753482. tion on internet of things devices. IEEE Micro. 2016;36:25–35. 5. Morales-Sandoval M, Diaz-Perez A. Det-abe: A java api for data Available from: https://doi.org/10.1109/MM.2016.101. confidentiality and fine-grained access control from attribute SI26 Tạp chí Phát triển Khoa học và Công nghệ – Kĩ thuật và Công nghệ, 3(S1):SI17-SI27 Open Access Full Text Article Bài Nghiên cứu Ứng dụng mã hóa dựa trên thuộc tính cho các thiết bị di động Đặng Tâm Nhân1, Lê Hải Dương2, Lê Thanh Sơn1, Trần Mạnh Hà2,* TÓM TẮT Thế kỷ 21 chứng kiến sự phát triển nhanh chóng của các thiết bị di động nhỏ và tiện lợi như điện thoại thông minh, máy tính bảng, máy chơi điện tử, nốt cảm biến, v.v. Sự gia tăng của các thiết Use your smartphone to scan this bị di động như vậy dẫn đến sự bùng nổviệc truyền tải dữ liệu khổng lồ thông qua Internet và các QR code and download this article dịch vụ trực tuyến cùng với những thách thức về an toàn dữ liệu. Người ta luôn suy nghĩ đến một giải pháp để bảo vệ dữ liệu nhạy cảm khỏi người dùng trái phép và giải pháp phổ biến nhất là sử dụng mã hóa. Trong khi nhiều hoạt động nghiên cứu về mã hóa chức năng đã được áp dụng rộng rãi cho các thiết bị mạng, máy tính và ứng dụng, thiết bị di động vẫn thu hút nhiều sự chú ý về các vấn đề bảo mật do một số hạn chế về tài nguyên hệ thống, tín hiệu kết nối, tiêu thụ điện năng mà người dùng trái phép có thể khai thác để thực hiện các tấn công. Đặc biệt, thiết bị di động trở thành công cụ chính để chia sẻ dữ liệu trên Internet thông qua các dịch vụ trực tuyến, chẳng hạn như các dịch vụ lưu trữ và chia sẽ thông tin được cung cấp bởi Facebook, Youtube, Amazon, DropBox, Online Games, v.v. Bài viết này trình bày một nghiên cứu về lược đồ mã hóa dựa trên thuộc tính (ABE) khai thác các thuộc tính người dùng để xây dựng khóa bí mật và dữ liệu mã hóa. Mã hóa ABE được chỉ định bởi một tập hợp các thuộc tính hoặc một chính sách xác định các thuộc tính mà người dùng sở hữu. Bài viết cũng mô tả một vài ứng dụng triển khai ABE được áp dụng trong cộng đồng mật mã và những thách thức của việc tích hợp ABE vào các ứng dụng thực tiễn. Cuối cùng, bài viết đề xuất ứng dụng triển khai ABE cho thiết bị di động Android. Ứng dụng này kết hợp với giao thức Kerberos có thể áp dụng cho nhiều ứng dụng chia sẻ dữ liệu an toàn. Giao thức Kerberos nhắm đến việc cung cấp xác thực qua lại cho mô hình máy chủ và máy người dùng. Các thực nghiệm đánh giá ứng dụng ABE đề xuất trên thiết bị di động Android cùng với hệ thống Kerberos. Phần đánh giá cũng bao gồm hiệu suất của ABE với một số thảo luận và rút ra bài học kinh nghiệm. Từ khoá: Mật mã học ứng dụng, Mã hóa dựa trên thuộc tính, Chia sẻ dữ liệu an toàn, Thiết bị di 1Trường Đại học Quốc tế, Đại học Quốc động, Điện toán di động gia Thành Phố Hồ Chí Minh, Thành Phố Hồ Chí Minh, Việt Nam 2Trường Đại học Quốc tế Hồng Bàng, Thành Phố Hồ Chí Minh, Việt Nam Liên hệ Trần Mạnh Hà, Trường Đại học Quốc tế Hồng Bàng, Thành Phố Hồ Chí Minh, Việt Nam Email: hatm@hiu.vn Lịch sử • Ngày nhận: 30-7-2019 • Ngày chấp nhận: 26-8-2019 • Ngày đăng: 17-10-2020 DOI :10.32508/stdjet.v3iSI1.518 Bản quyền © ĐHQG Tp.HCM. Đây là bài báo công bố mở được phát hành theo các điều khoản của the Creative Commons Attribution 4.0 International license. Trích dẫn bài báo này: Nhân D T, Dương L H, Sơn L T, Hà T M. Ứng dụng mã hóa dựa trên thuộc tính cho các thiết bị di động. Sci. Tech. Dev. J. - Eng. Tech.; 3(S1):SI17-SI27. SI27
File đính kèm:
 applying_attribute_based_encryption_on_mobile_devices.pdf
applying_attribute_based_encryption_on_mobile_devices.pdf

