A watermark algorithm against de - Synchronization attacks
In this paper, a robust method to the ability of the watermark to resist against attacks is proposed for hiding
information into images. The proposed method is blind because the original image is not required at the decoder
to recover the embedded data. The robustness of the watermarking scheme is inspired by using a PJND
(Pyramidal Just Noticeable Difference) model and the message is inserted into these DoG (Difference of
Gaussians) [1, 2]. Our proposal takes into account three main characteristics of Human Visual System, namely:
contrast sensitivity, luminance adaptation and contrast marking. Therefore, it not only provides an invisible and
robust watermarking but also optimizes watermarking capacity. The performance of the proposed technique is
evaluated by a series of experiments with different input images. In terms of transparency, besides using the
subjective experiments, eight objective metrics are calculated in comparison with other methods such as PSNR,
MSSIM, SVDm, etc. Our approach always presents the outperform values. In terms of robustness, many kinds of
attacks from global transformation (rotation, scaling, etc) to local transformation (stirmark, checkmark
benchmarks, de-synchronization attacks) are implemented. Many image processing tools are applied to simulate
the attacks such as Print-Screen, Using Photo editing software, Camcorder, Print-Scan, etc. The experimental
results show an outstanding robustness in resisting these attacks.

Trang 1

Trang 2

Trang 3

Trang 4
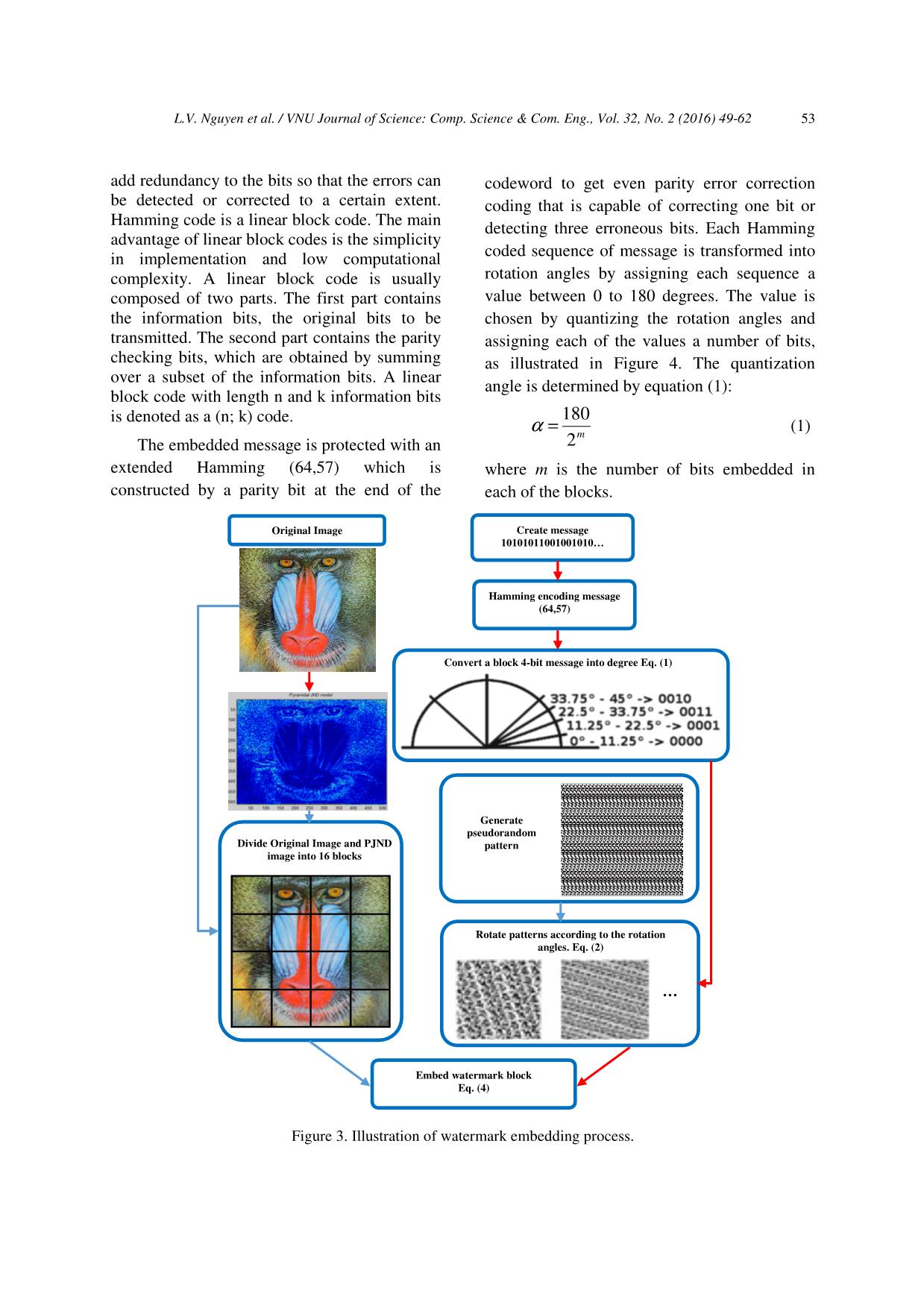
Trang 5

Trang 6
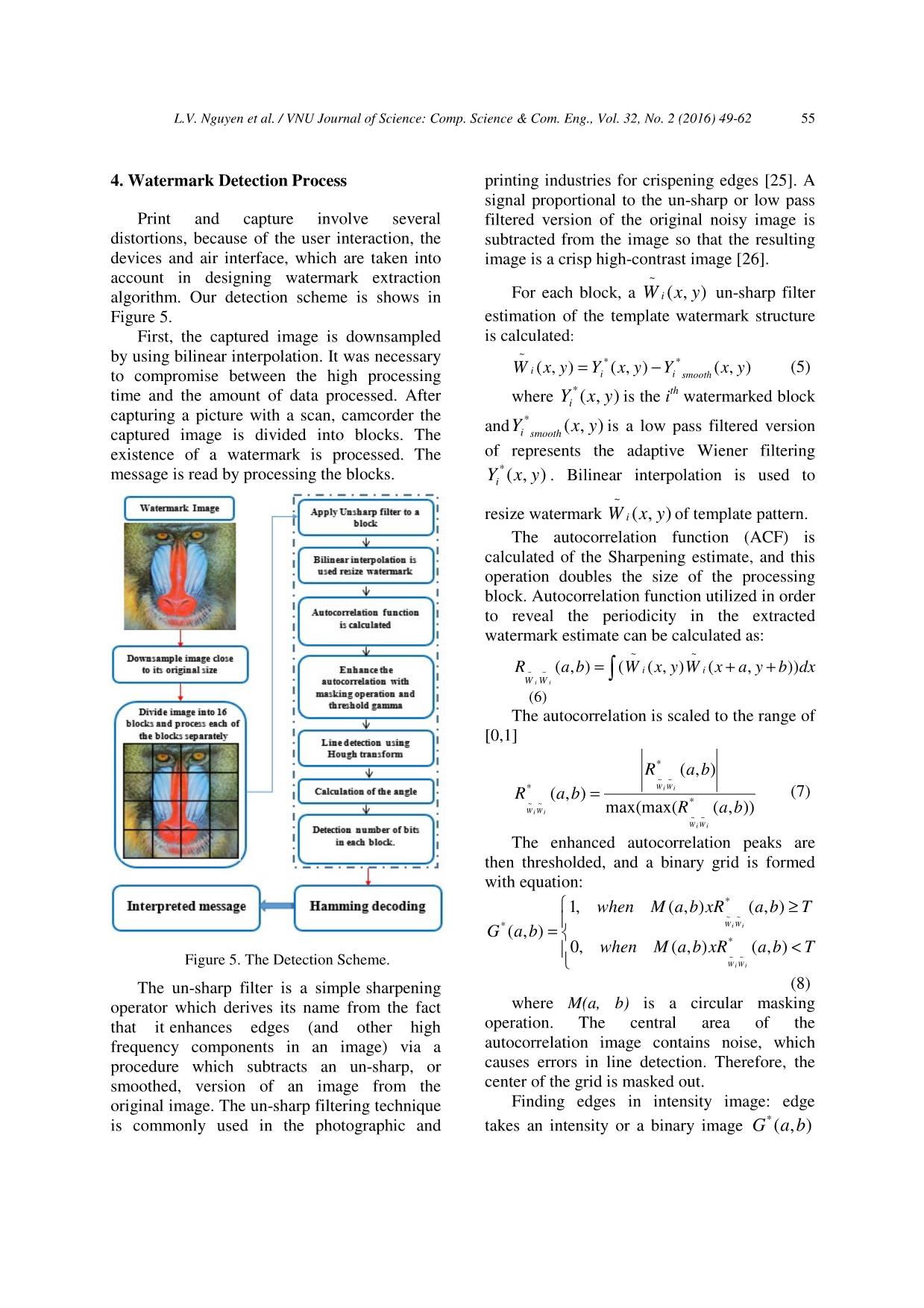
Trang 7

Trang 8
Trang 9

Trang 10
Tải về để xem bản đầy đủ
Tóm tắt nội dung tài liệu: A watermark algorithm against de - Synchronization attacks

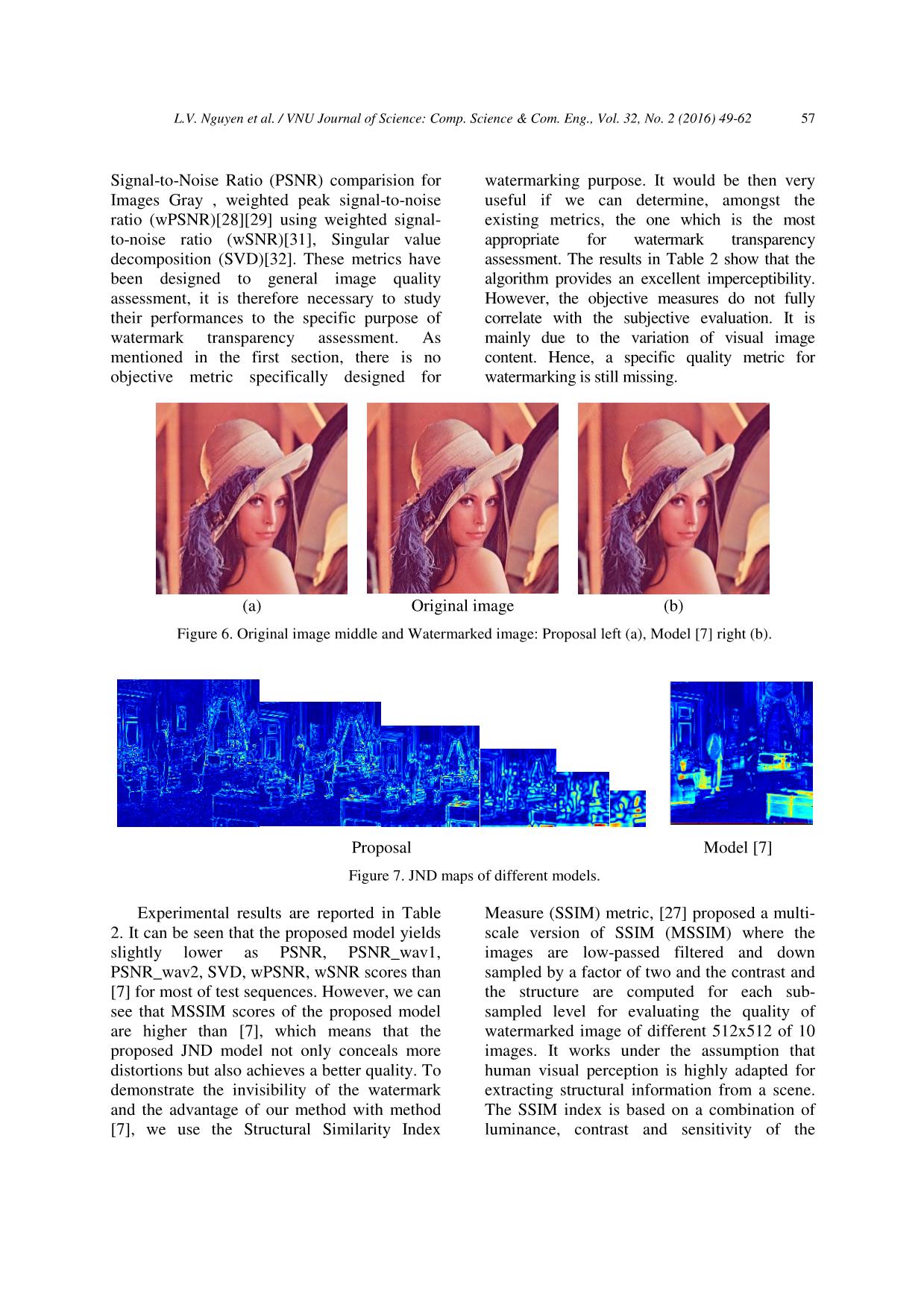
ity assessment and has been extended in various directions. Our results are reported in the following figures and in Table 2. As shows in Figure 6, the watermarked image and the original are visually undistinguishable. As for the watermark invisibility, quality results of watermarked image of different methods for different images are reported in Table 2. We can observe that the quality of the watermarked images of our method is equivalent or even better than that of other method [7]. 5.2. Evaluation of robustness The robustness of our algorithm is tested via a wide range of attacks including “signal processing” and de-synchronization types (DA). Some of them are very severe attacks like Print- Scan, Print Screen, Camcorder attack, Using Photo editing software and new de- synchronization attacks developed in [8] values are shown in Table 3. To facilitate the task, there are various tools that can test and evaluate watermarking algorithms systematically. Among them, the following two tools are most known to Stirmark [33] and Checkmark [34] benchmarks. However, when regarding the results in [7], we can see that the proposed method has a nearly equivalent robustness for geometric attacks values shown in Table 1. Furthermore, it resists other specific attacks (Camcorder, Print Screen, Using Photo editing software, new DAs) that the method [7] cannot. New DAs: these de-synchronization attacks are an extension of classical geometric attacks proposed by [8]. They are proved to be more powerful and less intrusive than the Stirmark attack. We tested three types of these with default parameters as in [8]: the LPCD (Local Permutation with Cancellation and Duplication, C-LPCD (Constraint LPCD), MF (Markov Random field). Watermark detection results are shown in Table 3. Table 1. Robustness Evaluation (Stirmark [33] and Checkmark [34] benchmarks attack) Attack Type Explicit scheme Method [7] Random Cropping 1% 0.8% Jpeg compression QF=3% QF=9% Jpeg 2000 compression 0.08 bpp 0.1 bpp Gaussian Noise σ= 64% σ= 67% Wiener filtering Ok Ok Median filtering 5x5 3x3 Sharpening Ok Failed Blurring Ok Failed Bit plan reduction Ok Failed Histogram Equalization Ok Ok Rescale (45%) Ok Ok Affine Transform Ok Ok Print-scan attack: this attack consists of printing image on a classical laser printer: HP LaserJet 4250 PCL6, EPSON Stylus. Scanning: Epson Perfection 4490. The image is printed in color, grayscale level on an A4 paper at 300 dpi resolution (tests were done on image printed on a white paper) and scanned, witch is shows in Figure 8. Watermark detection results are shown in Table 3. Camcorder attack: we get the picture of image on the computer screen with the Nikon D90 Digital SLR Camera with 18-105mm VR Lens Kit (12.3MP) 3inch LCD. The watermarked test images were captured 10 times with each of the camera setting and each image contained 57 bits and error coding when images were captured by tilting the camera randomly is shows in Figure 9 and values are shown in Table 3. Using Photo editing software: Do you still use Microsoft Paint, or some other under- powered paint packages that allow you to rotate an image by an arbitrary angle (Figure 9). L.V. Nguyen et al. / VNU Journal of Science: Comp. Science & Com. Eng., Vol. 32, No. 2 (2016) 49-62 59 Table 2. Imperceptibility Evaluation Image Objective Method Baboon Barbara Boat Car Clown Fruit Isabe Lena Peppers Plane AVG Keskinarkaus 25,79 28,41 33,01 32,80 33,66 36,68 36,18 35,45 35,51 35,82 33,33 PSNR Proposed 26,10 27,88 32,46 31,98 32,98 34,84 35,25 34,47 34,35 33,61 32,39 Keskinarkaus 9,36 11,64 15,96 16,93 17,13 19,25 16,78 17,72 19,16 19,65 16,36 PSNR wav1 Proposed 9,31 10,48 14,66 15,35 15,54 17,02 15,15 15,92 16,97 16,69 14,71 Keskinarkaus 10,08 12,43 16,33 17,69 18,13 19,68 18,56 19,11 19,99 20,03 17,20 PSNR wav2 Proposed 9,88 10,87 14,87 15,95 16,45 17,53 16,90 17,14 17,75 17,08 15,44 Keskinarkaus 37,82 34,82 16,47 17,35 12,51 9,74 9,28 10,70 8,07 11,10 16,79 SVDm Proposed 33,36 29,64 13,94 15,20 11,18 9,65 8,27 9,88 7,87 10,82 14,98 Keskinarkaus 0,19 0,10 0,08 0,08 0,08 0,07 0,07 0,07 0,07 0,06 0,09 TPE Proposed 0,19 0,13 0,08 0,09 0,10 0,08 0,07 0,07 0,08 0,07 0,10 Keskinarkaus 0,82 0,88 0,93 0,94 0,93 0,97 0,94 0,94 0,91 0,96 0,92 mssim Proposed 0,85 0,89 0,94 0,94 0,94 0,97 0,95 0,94 0,93 0,96 0,93 Keskinarkaus 35,56 37,28 39,25 38,34 38,62 40,46 39,98 39,76 38,95 40,93 38,91 wPSNR Proposed 35,99 36,93 38,97 37,80 37,90 39,60 39,24 39,31 38,80 39,46 38,40 Keskinarkaus 33,18 34,85 39,28 38,09 34,50 37,17 40,58 38,69 39,77 41,39 37,75 wsnr Proposed 32,16 32,08 37,92 36,41 33,71 35,39 38,82 37,05 37,17 38,08 35,88 Table 3. Robustness Evaluation. For some type of attacks, the results showed: X/Y (bit error/bit encoded message) the parameters demonstrate the break-down limit of the method (the strongest attack to which the watermark still survives) Attack Method Baboon Fruit Isabe Lena Peppers Ours Ok Ok 2/64 1/64 3/64 Camcorder attack Keskinarkaus - - - - - Ours Ok 3/64 Ok 2/64 Ok Print scan Attack Keskinarkaus Ok 2/48 3/48 Ok Ok Ours Ok Ok 2/64 3/64 Ok Photo editing software Keskinarkaus - - - - - Ours Ok Ok Ok Ok Ok Print screen Attack Keskinarkaus - - - - - Ours Ok Ok Ok Ok Ok DA New Keskinarkaus - - - - - L.V. Nguyen et al. / VNU Journal of Science: Comp. Science & Com. Eng., Vol. 32, No. 2 (2016) 49-62 60 f Watermark Image Insert Document and Print Scanner at 300dpi resolution Figure 8. The watermark image is printed and scanned. Watermark Image screen with the Nikon Crop image and Detection Figure 9. The watermark screen with the Nikon. We user vertical shear and skew the image a negative number of degrees (1-6 degrees) in the vertical plane which is shows in Figure 10 and values are shown in Table 3. Vertical shear 5 degrees Vertical shear 6 degrees Figure 10. The watermark attack Using Photo editing software. Print screen Keyboard: When you press it, an image of your screen is copied to the Clipboard. This is called a screen capture or screen shot. You will then need to further edit using some image editing programs values shown in Table 3. Table 3 shows the average robustness tested for five images (Baboon, Fruit, Isabe, Lena and Peppers). These values denote the breakdown limit of the tested methods, i.e. the strongest level of attacks to which the watermark still survives. Table 1 shows that the watermark survives many severe attacks in both schemes but there are no significant differences in robustness between these two schemes (except for Jpeg compression). Furthermore, robustness against some attacks "like Jpeg" (Jpeg2000) is even slightly improved. Watermark detection results are shown in Table 1 and Table 3; our method outperformed the method [7] for most attacks. Furthermore, the message protected with Hamming (64, 57) error correction coding that is capable of correcting three bits ensures that the message can be decoded correctly. Especially, in contrast to [7], it survives many severe attacks such as "camcorder", "print-scan" and Stirmark, Checkmark and new DA. However, our method as well as the method [7] are not very robust to "signal processing" attacks such as noise, jpeg compression, etc. Throughout these results, it is clear that using perceptual models helps improve not only transparency but also robustness of a watermarking system. The explicit scheme, once again provides the best robustness amongst the compared methods. The detector outputs for some severe attacks are also displayed in Figure 8, 9 and 11. 6. Conclusion In this paper, we have presented a novel content based image watermarking operating in the DoG scale space with enhancing robustness against de-synchronization attacks. Such watermarking methods present additional advantages over the published watermarking schemes in terms of detection and recovery from geometric attacks, and with better security characteristics. The experimental results show that the proposed method has a good performance in terms of robustness and imperceptibility. In the future, this method digital watermarking will be extenđe to used on mobile phones. L.V. Nguyen et al. / VNU Journal of Science: Comp. Science & Com. Eng., Vol. 32, No. 2 (2016) 49-62 61 References [1] Luong Viet Nguyen, Trinh Nhat Tien, Ho Van Canh. “Pyramidal JND Model for Grayscale Image and its Application to Watermarking”. Proceedings of IEEE International Conference on Computer Science and Automation Engineering Vol.01[C], 2013. [2] Luong Viet Nguyen, Trinh Nhat Tien, and Ho Van Canh. “A watermarking method robust for copyright protection of images against Print- scan.” Information Science and Control Engineering (ICISCE), IET International Conference on. IET, 2012. [3] Ensaf Hussein, Mohamed A. Belal, “Digital Watermarking Techniques, Applications and Attacks Applied to Digital Media: A Survey,” IJERT, ISSN: 2278-0118, Vol. 1 Issue 7, 2012. [4] S. Voloshynovskiy, A. Herrigel, N. Baumgartner, and T. Pun, “A stochastic approach to content adaptive digital image watermarking,” in Proc. of the 3rd International Workshop on Information Hiding, 1999. [5] Mundher, Myasar, et al. “Digital watermarking for images security using discrete slantlet transform.” Applied Mathematics and Information Sciences 8.6: 2823-2830, 2014. [6] Kekre, H. B., Tanuja Sarode, and Shachi Natu. “Performance of watermarking system using wavelet column transform under various attacks.” International Journal of Computer Science and Information Security 12.2 (2014). [7] A. Keskinarkaus, A. Pramila, T. Seppänen, “Image watermarking with a directed periodic pattern to embed multibit messages resilient to print scan and compound attacks.” the Journal of Systems and Software v. 83 (2010) 1715. [8] Barni, Mauro, Angela D'Angelo, and Neri Merhav. “Expanding the class of watermark de- synchronization attacks.” Proceedings of the 9th workshop on Multimedia & security, ACM, 2007. [9] Wang, Xiang-Yang, and Chang-Ying Cui. “A novel image watermarking scheme against desynchronization attacks by SVR revision.” Journal of Visual Communication and Image Representation 19.5(2008) 334. [10] Schmitz, Roland, et al. “Towards Robust Invariant Commutative Watermarking- Encryption Based on Image Histograms.” International Journal of Multimedia Data Engineering and Management 5.4 (2014) 36. [11] P. Dong, J. G. Brankov, N. P. Galatsanos, Y. Yang, and F. Davoine, “Digital watermarking robust to geometric distortions,” IEEE Trans. on Image Processing, vol. 14 (2003) 2140. [12] M. Alghoniemy and A. H. Tewfik, “Geometric invariance in image watermarking,” IEEE Trans. on Image Processing, vol. 13, no. 2 (2004) 145. [13] Zhao, Yao, RongRong Ni, and ZhenFeng Zhu. “RST transforms resistant image watermarking based on centroid and sector-shaped partition.” Science China Information Sciences 55.3, 650-662, 2012. [14] Wang, Caiyin, and Chao Li. “A Steganography Approach for Printed Image Based on Image Complexity and Template Matching.” Open Automation and Control Systems Journal 6 (2014) 84. [15] Schlauweg, Mathias, et al. “Self-synchronizing robust Texel watermarking in Gaussian scale- space.” Proceedings of the 10th ACM workshop on Multimedia and security. ACM, 2008. [16] Joseph J. K., O’ Ruanaidh, J. J. K. et Pun, T. “Rotation, Scale and Translation Invariant Digital Image Watermarking”, Image Processing. International Conference, Issue, 26- 29 (1997) 536. [17] Wang, Xiang-Yang, et al. “A new robust digital watermarking based on exponent moments invariants in nonsubsampled contourlet transform domain.” Computers & Electrical Engineering 40.3 (2014) 942. [18] M. Mitrea, F. Preteux, M. Petrescu, and A. Vlad, “The Stirmark watermarking attack in the dwt domain,” in Proceedings of the 12th IEEE International Conference on Systems, Signals and Image Processing (IWSSIP’05), Halkida, Greece, pp. 5–9, 2005. [19] Wang, Xiang-yang, et al. “Robust image watermarking approach using polar harmonic transforms based geometric correction.” Neurocomputing, 2015. [20] N. Merhav, “An information-theoretic view of watermark embedding-detection and geometric attacks,” in Proceedings of WaCha’05, Barcelona, Spain, 2005. [21] D. Zheng, J. Zhao, and A. Saddik, “Rst invariant digital imagewatermarking based on log-polar mapping and phase correlation,” IEEE Trans. Circ. Syst. Video Tech., vol. 13 (2003) 753. [22] S. Pereira and T. Pun, “Robust template matching for affine resistant image watermarks,” IEEE Transaction on Image Processing, vol. 9, no. 6, June (2000) 1123. [23] W. Peterson., “Error-correcting codes,” 2nd ed., Cambridge: The MIT Press, 1980. 560p. L.V. Nguyen et al. / VNU Journal of Science: Comp. Science & Com. Eng., Vol. 32, No. 2 (2016) 49-62 62 [24] Toffoli, Tommaso, and Jason Quick. “Three- dimensional rotations by three shears.” Graphical Models and Image Processing 59.2, 89-95, 1997. [25] Jain A., “Fundamentals of Digital Image Processing,” Prentice-Hall, France, 1989. [26] Amirgholipour S. and Naghsh-Nilchi A., “A New Robust Digital Image Watermarking Technique Based on Joint DWT-DCT Transformation,” in Proceedings of the 3rd International Conference on Convergence and Hybrid Information Technology, Busan, vol. 2 (2008) 539. [27] Wang, Z., Bovik, A. C., Sheikh H. R., Simoncelli, P. E.: “Image quality assessment: from error visibility to structural similarity.” IEEE Transactions on Image Processing, 13(4), pp. 600-612, 2004. [28] Pereira, S., Voloshynovskiy, S., Madueño, M., Marchand-Maillet, S., Pun, T.: “Second generation benchmarking and application oriented evaluation.” In Procs of 3rd Int. Workshop on Information Hiding, pp. 219-239, Pittsburgh, PA, USA, 2001. [29] Pereira, S.: “Robust digital image watermarking”, PhD thesis, Genève, Swiss, 2000. [30] Beghdadi, A. and Pesquet-Popescu, B.: “A New Image Distortion Measure Based on Wavelet Decomposition.” In Proc. of 7th IEEE ISSPA, vol. 2, pp. 485-488, Paris, France 2003. [31] Niranjan, D. V., Thomas, D. K., Wilson, S. G., Brian, L. E., Bovik, A. C.: “Image quality assessment based on a degradation model”, In IEEE Trans Image Processing, 9(4) (2000) 636. [32] Shnayderman, R., Gusev, E., Eskicioglu, A. M.: “An SVD-based gray-scale image quality measure for local and global assessment.” In IEEE Transactions on Image Processing, 15(2) (2006) 422. [33] tirmark/ [34] html
File đính kèm:
 a_watermark_algorithm_against_de_synchronization_attacks.pdf
a_watermark_algorithm_against_de_synchronization_attacks.pdf

