Security capability analysis of cognitive radio network with secondary user capable of jamming and self-powering
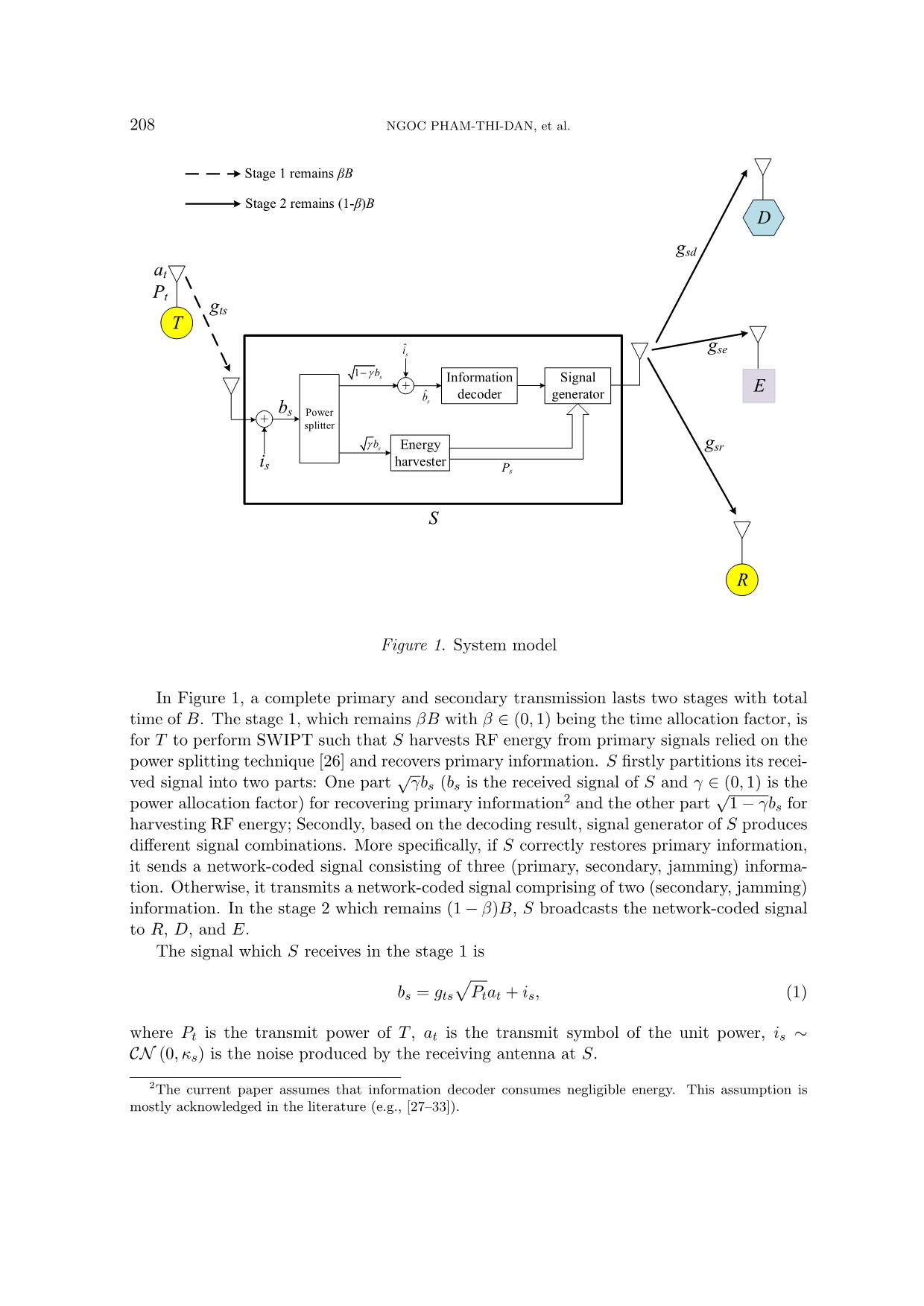
This paper investigates a cognitive radio network where a secondary sender assists a
primary transmitter in relaying primary information to a primary receiver and also transmits its
own information to a secondary recipient. This sender is capable of jamming to protect secondary
and/or primary information against an eavesdropper and self-powering by harvesting radio frequency
energy of primary signals. Security capability of both secondary and primary networks are analyzed
in terms of secrecy outage probability. Numerous results corroborate the proposed analysis which
serves as a design guideline to quickly assess and optimize security performance. More importantly,
security capability trade-off between secondary and primary networks can be totally controlled with
appropriate selection of system parameters.

Trang 1

Trang 2

Trang 3
Trang 4

Trang 5

Trang 6

Trang 7

Trang 8

Trang 9

Trang 10
Tải về để xem bản đầy đủ
Tóm tắt nội dung tài liệu: Security capability analysis of cognitive radio network with secondary user capable of jamming and self-powering

n!
I (84)
0 ∞ 0
Z n Z −Msex
J−Mse X J e
Kse−V −Msex
= e e dx + 2n n dx ,
(Kse − V ) n! x
I n=1 I
where I is given in (48).
The first integral in (84) is easily solved while the second one is solved by invoking [44, eq.
(2.324.2)]. Inserting closed forms of these two integrals into (84), one reduces (84) to (50),
completing the proof of ∆ for 1 ≤ Kse < V .
Scenario 3. V < 1
This scenario simplifies (71) as
V Uy K K
Z Z Z se Z sr
∆ = fXsr (x) dx fXse (y) dy + fXsr (x) dx fXse (y) dy . (85)
y=U −1 x=1 y=1 x=1
| {z } | {z }
Case 2: U −1≤yV
Since fXse (y) = 0 when y = V < 1, the first term in (85) is zero. Additionally, fXsr (x)
is non-zero for x ∈ [1,Ksr) and fXse (y) is non-zero for y ∈ [1,Kse) and thus, the second
term in (85) is one. Plugging these results into (85), one infers ∆ = 1, which matches (45)
for V < 1. This finishes the proof of ∆ for V < 1.
By combining the three above scenarios, it is seen that ∆ is precisely solved as (45). This
completes the proof of Theorem 1.
APPENDIX B: PROOF OF Ψ2
Bh¯ se
Let Xsd = 1 + Ah¯ sd and X¯se = 1 + where A¯, B¯, and C¯ are given in (60), (61),
Ch¯ se+κe
and (62), correspondingly. Relied on the variable change, the PDF of Xsd is expressed as
x−1
1 − ¯
ϑsdA
fXsd (x) = e , x ≥ 1. (86)
ϑsdA¯
Also, by invoking Lemma 1, the PDF of X¯se can be obtained as
¯ y−1
E ¯
¯ e y−D ¯
fX¯ (y) = G , 1 ≤ y < D, (87)
se �y − D¯2
where D¯, E¯, and G¯ are correspondingly given in (63), (64), and (65).
Invoking (11) and (13) for the case of Γs < Γt, one rewrites Ψ2 in (56) as
µPshsd µPshse
Ψ2 = Pr 1 + < U 1 +
Γs < Γt , (88)
κd (1 − µ) Pshse + κe
SECURITY CAPABILITY ANALYSIS OF COGNITIVE RADIO NETWORK 227
which is also represented in terms of Xsd and X¯se as
¯
Ψ2 = Pr Xsd < UXse
Γs < Γt . (89)
Since Xsd and X¯se are statistically independent, (89) can be rewritten in terms of the
individual PDFs of Xsd and X¯se as
ZZ
Ψ2 = fXsd (x) fX¯se (y) dxdy. (90)
x<Uy
Because fXsd (x) is non-zero for x ≥ 1, two cases on Uy in correlation to 1 are considered
as
D¯ Uy
Z Z Z Z
Ψ = f (x) dx f ¯ (y) dy + f (x) dx f ¯ (y) dy . (91)
2 Xsd Xse Xsd Xse
y<U −1 x<Uy y=1 x=1
| {z } | {z }
Case 1: Uy1
R
The first term in (91) is zero since fXsd (x) dx = 0 due to fXsd (x) = 0 for x = Uy <
x<Uy
1. Accordingly, by substituting (86) into the second term in (91) and after solving the inner
integral in (91), one has
D¯ D¯ D¯
Z Uy−1 Z 1 Z
− ¯ ¯ ¯
ϑsdA ϑsdA −Qy
Ψ2 = 1 − e fX¯se (y) dy = fX¯se (y) −e e fX¯se (y) dy, (92)
1 1 1
| {z } | {z }
1 H
where Q¯ is given in (66).
The first integral in the last equality of (92) is one due to the property of the PDF while
the second integral can be rewritten after invoking fX¯se (y) in (87) as
D¯ ¯ y−1
E ¯
Z ¯ e y−D
H = e−QyG¯ dy
�y − D¯2
1
−∞
1
x= Z ¯
y−D¯ E¯−Q¯D¯ Gx¯ − Q
= −Ge¯ e x dx (93)
1/(1−D¯)
∞
Z ¯
y=−x ¯ ¯ ¯ −Gy¯ + Q
= Ge¯ E−QD e y dy.
1/(D¯−1)
228 NGOC PHAM-THI-DAN, et al.
¯
∞ n Q
x P x y
Executing the series expansion e = n! for the term e in (93), one obtains
n=0
∞ ∞ n!
¯ ¯ ¯ Z ¯ X 1 Q¯
H = Ge¯ E−QD e−Gy dy
n! y
n=0
1/(D¯−1)
∞
∞ � ¯ ¯n −x
x=Gy¯ ¯ ¯ ¯ X QG Z e
= eE−QD dx. (94)
n! xn
n=0
E¯
The last integral in (94) is solved by invoking [44, eq. (3.381.6)], which reduces (94) to
∞ �Q¯G¯n
E¯−Q¯D¯ X ¯−n/2 −E/¯ 2 � ¯
H = e E e W− n , 1−n E . (95)
n! 2 2
n=0
Substituting (95) into (92), one reduces (92) to (59), finishing the proof.
REFERENCES
[1] S. K. Sharma, I. Woungang, A. Anpalagan, and S. Chatzinotas, “Towards tactile internet in
beyond 5g era: Recent advances, current issues and future directions,” IEEE Access, vol. 8, pp.
56948–56991, 2020.
[2] M. Tavana, A. Rahmati, V. Shah-Mansouri, and B. Maham, “Cooperative sensing with joint
energy and correlation detection in cognitive radio networks,” IEEE Communications Letters,
vol. 21, pp. 132–135, 2017.
[3] D. Feng, C. Jiang, G. Lim, L. J. Cimini, Jr., G. Feng, and G. Y. Li, “A survey of energy-efficient
wireless communications ,” IEEE Communications Surveys & Tutorials, vol. 15, pp. 167-178,
2013.
[4] A. Celik, A. Alsharoa, and A. E. Kamal, “Hybrid energy harvesting cooperative spectrum sensing
in heterogeneous CRNs,” in 2016 IEEE Globecom Workshops (GC Wkshps), Washington,
DC, 2016, pp. 1-6. Doi: 10.1109/GLOCOMW.2016.7848925
[5] S. Buzzi, C.-L. I, T. E. Klein, H. V. Poor, C. Yang, and A. Zappone, “A survey of energy-
efficient techniques for 5G networks and challenges ahead,” IEEE Journal on Selected Areas
in Communications, vol. 34, pp. 697–709, 2016.
[6] F. Zhou, Z. Li, J. Cheng, Q. Li, and J. Si, “Robust AN-aided beamforming and power split-
ting design for secure MISO cognitive radio with SWIPT,” IEEE Transactions on Wireless
Communications, vol. 16, pp. 2450–2464, 2017.
[7] G. Pan, H. Lei, Y. Yuan, and Z. Ding, “Performance analysis and optimization for SWIPT
wireless sensor networks,” IEEE Transactions on Communications, vol. 65, no. 5, pp. 2291–
2302, May 2017. Doi: 10.1109/TCOMM.2017.2676815
[8] T. Liu, X. Wang, and L. Zheng, “A cooperative SWIPT scheme for wirelessly powered sensor
networks,” IEEE Transactions on Communications, vol. 65, no. 6, pp. 2740–2752, June 2017.
Doi: 10.1109/TCOMM.2017.2685580
SECURITY CAPABILITY ANALYSIS OF COGNITIVE RADIO NETWORK 229
[9] H. Ding, D. B. da Costa, H. A. Suraweera, and J. Ge, “Role selection cooperative systems with
energy harvesting relays,” IEEE Transactions on Wireless Communications, vol. 15, no. 6,
pp. 4218–4233, June 2016. Doi: 10.1109/TWC.2016.2536732
[10] Y. Gu and S. Aissa, “RF-based energy harvesting in decode-and-forward relaying systems: Er-
godic and outage capacities,” IEEE Transactions on Wireless Communications, vol. 14, no.
11, pp. 6425–6434, Nov. 2015. Doi: 10.1109/TWC.2015.2453418
[11] A. Rajaram, D. N. K. Jayakody, K. Srinivasan, B. Chen, and V. Sharma, “Opportunistic-
Harvesting: RF wireless power transfer scheme for multiple access relays system,” IEEE Access,
vol. 5, pp. 16084–16099, 2017. Doi: 10.1109/ACCESS.2017.2734852
[12] J. Miao and Z. Zheng, “Cooperative Jamming for Secure UAV-Enabled Mobile Relay System,”
IEEE Access, vol. 8, pp. 48943–48957, 2020. Doi: 10.1109/ACCESS.2020.2980242
[13] F. Zhu and M. Yao, “Improving physical layer security for CRNs using SINR-based cooperative
beamforming,” IEEE Transactions on Vehicular Technology, vol. 65, no. 3, pp. 1835–1841,
March 2016. Doi: 10.1109/TVT.2015.2412152
[14] B. He and X. Zhou, “Secure on-off transmission design with channel estimation errors,” IEEE
Transactions on Information Forensics and Security, vol. 8, no. 12, pp. 1923–1936, Dec.
2013. Doi: 10.1109/TIFS.2013.2284754
[15] I. Krikidis, J. S. Thompson, and S. McLaughlin, “Relay selection for secure cooperative networks
with jamming,” IEEE Transactions on Wireless Communications, vol. 8, no. 10, pp. 5003–
5011, October 2009. Doi: 10.1109/TWC.2009.090323
[16] S. Yan, N. Yang, R. Malaney, and J. Yuan, “Transmit antenna selection with Alamouti coding
and power allocation in MIMO wiretap channels,” IEEE Transactions on Wireless Commu-
nications, vol. 13, no. 3, pp. 1656–1667, March 2014. Doi: 10.1109/TWC.2013.013014.131248
[17] I. Krikidis and B. Ottersten, “Secrecy sum-rate for orthogonal random beamforming with oppor-
tunistic scheduling,” IEEE Signal Processing Letters, vol. 20, no. 2, pp. 141–144, Feb. 2013.
Doi: 10.1109/LSP.2012.2234109
[18] L. Jong-Ho, “Full-duplex relay for enhancing physical layer security in multi-hop relaying
systems,” IEEE Communications Letters, vol. 19, no. 4, pp. 525–528, April 2015. Doi:
10.1109/LCOMM.2015.2401551
[19] K. Cao, B. Wang, H. Ding, T. Li, J. Tian, and F. Gong, “Secure transmission designs for noma
systems against internal and external eavesdropping,” IEEE Transactions on Information
Forensics and Security, vol. 15, pp. 2930–2943, 2020. Doi: 10.1109/TIFS.2020.2980202
[20] R. Su, Y. Wang, and R. Sun, “Secure cooperative transmission in cognitive AF relay systems with
destination-aided jamming and energy harvesting,” in 2019 IEEE 30th Annual International
Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Istanbul,
Turkey, 2019, pp. 1–5. Doi: 10.1109/PIMRC.2019.8904314
[21] R. Su, Y. Wang, and R. Sun, “Destination-assisted jamming for physical-layer security in SWIPT
cognitive radio systems,” in 2018 IEEE Wireless Communications and Networking Confe-
rence (WCNC), Barcelona, 2018, pp. 1–6. Doi: 10.1109/WCNC.2018.8377306
[22] D. Wang, F. Zhou, and V. C. M. Leung, “Primary privacy preserving with joint wire-
less power and information transfer for cognitive radio networks,” IEEE Transactions on
230 NGOC PHAM-THI-DAN, et al.
Cognitive Communications and Networking, vol. 6, no. 2, pp. 683–693, June 2020. Doi:
10.1109/TCCN.2019.2952885
[23] M. Xu, T. Jing, X. Fan, Y. Wen, and Y. Huo, “Secure transmission solutions in energy
harvesting enabled cooperative cognitive radio networks,” in 2018 IEEE Wireless Com-
munications and Networking Conference (WCNC), Barcelona, 2018, pp. 1–6. Doi:
10.1109/WCNC.2018.8377071
[24] M. Li, H. Yin, Y. Huang, Y. Wang, and R. Yu, “Physical layer security in overlay cognitive radio
networks with energy harvesting,” IEEE Transactions on Vehicular Technology, vol. 67, no.
11, pp. 11274–11279, Nov. 2018. Doi: 10.1109/TVT.2018.2868902
[25] L. Chen, L. Huang, H. Xu, C. Yang, Z. Sun, and X. Wang, “Primary secrecy Is achievable:
optimal secrecy rate in overlay CRNs with an energy harvesting secondary transmitter,” in 2015
24th International Conference on Computer Communication and Networks (ICCCN), Las
Vegas, NV, 2015, pp. 1–6. Doi: 10.1109/ICCCN.2015.7288450
[26] X. Zhou, R. Zhang, and C. K. Ho, “Wireless information and power transfer: Architecture
design and rate-energy tradeoff,” IEEE Transactions on Communications, vol. 61, no. 11,
pp. 4754–4767, November 2013. Doi: 10.1109/TCOMM.2013.13.120855
[27] P. M. Quang, T. T. Duy, and V. N. Q. Bao, “Performance evaluation of underlay cognitive radio
networks over Nakagami-m fading channels with energy harvesting,” in 2016 International
Conference on Advanced Technologies for Communications (ATC), Hanoi, 2016, pp. 108–
113. Doi: 10.1109/ATC.2016.7764755
[28] J. Zhang, G. Pan, and H.M. Wang, “On physical-layer security in underlay cognitive radio
networks with full-duplex wireless-powered secondary system,” IEEE Access, vol. 4, pp. 3887–
3893, 2016. Doi: 10.1109/ACCESS.2016.2591782
[29] W. Mou, W. Yang, X. Xu, X. Li, and Y. Cai, “Secure transmission in spectrum-sharing
cognitive networks with wireless power transfer,” in 2016 8th International Conference on
Wireless Communications & Signal Processing (WCSP), Yangzhou, 2016, pp. 1–5. Doi:
10.1109/WCSP.2016.7752665
[30] H. Lei, M. Xu, H. Zhang, G. Pan, I. S. Ansari, and K. A. Qaraqe, “Secrecy outage performance for
underlay MIMO CRNs with energy harvesting and transmit antenna selection,” in 2016 IEEE
Globecom Workshops (GC Wkshps), Washington, DC, 2016, pp. 1–6. Doi: 10.1109/GLO-
COMW.2016.7849037
[31] A. Singh, M. R. Bhatnagar, and R. K. Mallik, “Secrecy outage of a simultaneous wireless infor-
mation and power transfer cognitive radio system,” IEEE Wireless Communications Letters,
vol. 5, no. 3, pp. 288–291, June 2016. Doi: 10.1109/LWC.2016.2544828
[32] Y. Liu, L. Wang, S. A. R. Zaidi, M. Elkashlan, and T. Q. Duong, “Secure D2D communication in
large-scale cognitive cellular networks: A wireless power transfer model,” IEEE Transactions on
Communications, vol. 64, no. 1, pp. 329–342, Jan. 2016. Doi: 10.1109/TCOMM.2015.2498171
[33] S. Raghuwanshi, P. Maji, S. D. Roy, and S. Kundu, “Secrecy performance of a dual hop cognitive
relay network with an energy harvesting relay,” in 2016 International Conference on Advances
in Computing, Communications and Informatics (ICACCI), Jaipur, 2016, pp. 1622–1627.
Doi: 10.1109/ICACCI.2016.7732280
[34] S. Zhihui, Q. Yi, and C. Song, “On physical layer security for cognitive radio networks,” IEEE
Network, vol. 27, no. 3, pp. 28–33, May-June 2013. Doi: 10.1109/MNET.2013.6523805
SECURITY CAPABILITY ANALYSIS OF COGNITIVE RADIO NETWORK 231
[35] R. Sharma and D. Rawat, “Advances on security threats and countermeasures for cognitive
radio networks: A Survey,” IEEE Communications Surveys & Tutorials, vol. 17, no. 2, pp.
1023–1043, Secondquarter 2015. Doi: 10.1109/COMST.2014.2380998
[36] V. D. Nguyen, T. Q. Duong, O. A. Dobre, and O. S. Shin, “Joint information and jamming
beamforming for secrecy rate maximization in cognitive radio networks,” IEEE Transacti-
ons on Information Forensics and Security, vol. 11, no. 11, pp. 2609–2623, Nov. 2016. Doi:
10.1109/TIFS.2016.2594131
[37] B. Fang, Z. Qian, W. Shao, and W. Zhong, “Precoding and artificial noise design for cognitive
MIMOME wiretap channels,” IEEE Transactions on Vehicular Technology, vol. 65, no. 8,
pp. 6753–6758, Aug. 2016. Doi: 10.1109/TVT.2015.2477305
[38] Y. Wu, X. Chen, and X. Chen, “Secure beamforming for cognitive radio networks with artificial
noise,” in 2015 International Conference on Wireless Communications & Signal Processing
(WCSP), Nanjing, 2015, pp. 1–5. Doi: 10.1109/WCSP.2015.7341139
[39] X. Hu, X. Zhang, H. Huang, and Y. Li, “Secure transmission via jamming in cognitive radio
networks with possion spatially distributed eavesdroppers,” in 2016 IEEE 27th Annual Inter-
national Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC),
Valencia, 2016, pp. 1–6. Doi: 10.1109/PIMRC.2016.7794918
[40] Z. Li, T. Jing, X. Cheng, Y. Huo, W. Zhou, and D. Chen, “Cooperative jamming for se-
cure communications in MIMO cooperative cognitive radio networks,” in 2015 IEEE In-
ternational Conference on Communications (ICC), London, 2015, pp. 7609–7614. Doi:
10.1109/ICC.2015.7249543
[41] Y. Zou, “Physical-layer security for spectrum sharing systems,” IEEE Transacti-
ons on Wireless Communications, vol. 16, no. 2, pp. 1319–1329, Feb. 2017. Doi:
10.1109/TWC.2016.2645200
[42] Y. Liu, L. Wang, T. T. Duy, M. Elkashlan, and T. Q. Duong, “Relay selection for security
enhancement in cognitive relay networks,” IEEE Wireless Communications Letters, vol. 4,
no. 1, pp. 46–49, Feb. 2015. Doi: 10.1109/LWC.2014.2365808
[43] P. Chakraborty and S. Prakriya, “Secrecy performance of an idle receiver assisted underlay
secondary network,” IEEE Transactions on Vehicular Technology, vol. 66, no. 10, pp. 9555–
9560, Oct. 2017. Doi: 10.1109/TVT.2017.2698162
[44] I. S. Gradshteyn and I. M. Ryzhik, Table of Integrals, Series and Products, 6th ed. San Diego,
CA: Academic, 2000.
Received on April 16, 2020
Revised on June 22, 2020File đính kèm:
 security_capability_analysis_of_cognitive_radio_network_with.pdf
security_capability_analysis_of_cognitive_radio_network_with.pdf

