Implementation of black hole attack on AODV routing protocols in manet using NS2
One of the major challenges of Mobile Ad hoc Network (MANETs) is how to implement and avoid of different kind of security attack such as Denial of service (DoS), wormhole, replay, masquerade, black hole etc. MANETs use routing protocol to communicate the data packet from one node to another and each node acts as a host or router, which can choose suitable paths for transmission of packet. AODV is one of the most popular used routing protocols in ad-Hoc networks, but it also has a lot of potential lack of security. The goal of attacks is usually to disrupt the operation of the network or to affect the network performance. In this paper, we implement and analyses performance of multiple black hole attack nodes simultaneously in AODV routing protocol in terms of throughput, energy efficiency and data packet delivery. Our simulation results show that the more attackable nodes in network simultaneously, the lower the energy efficiency and network performance

Trang 1
Trang 2
Trang 3
Trang 4
Trang 5
Trang 6

Trang 7
Tóm tắt nội dung tài liệu: Implementation of black hole attack on AODV routing protocols in manet using NS2

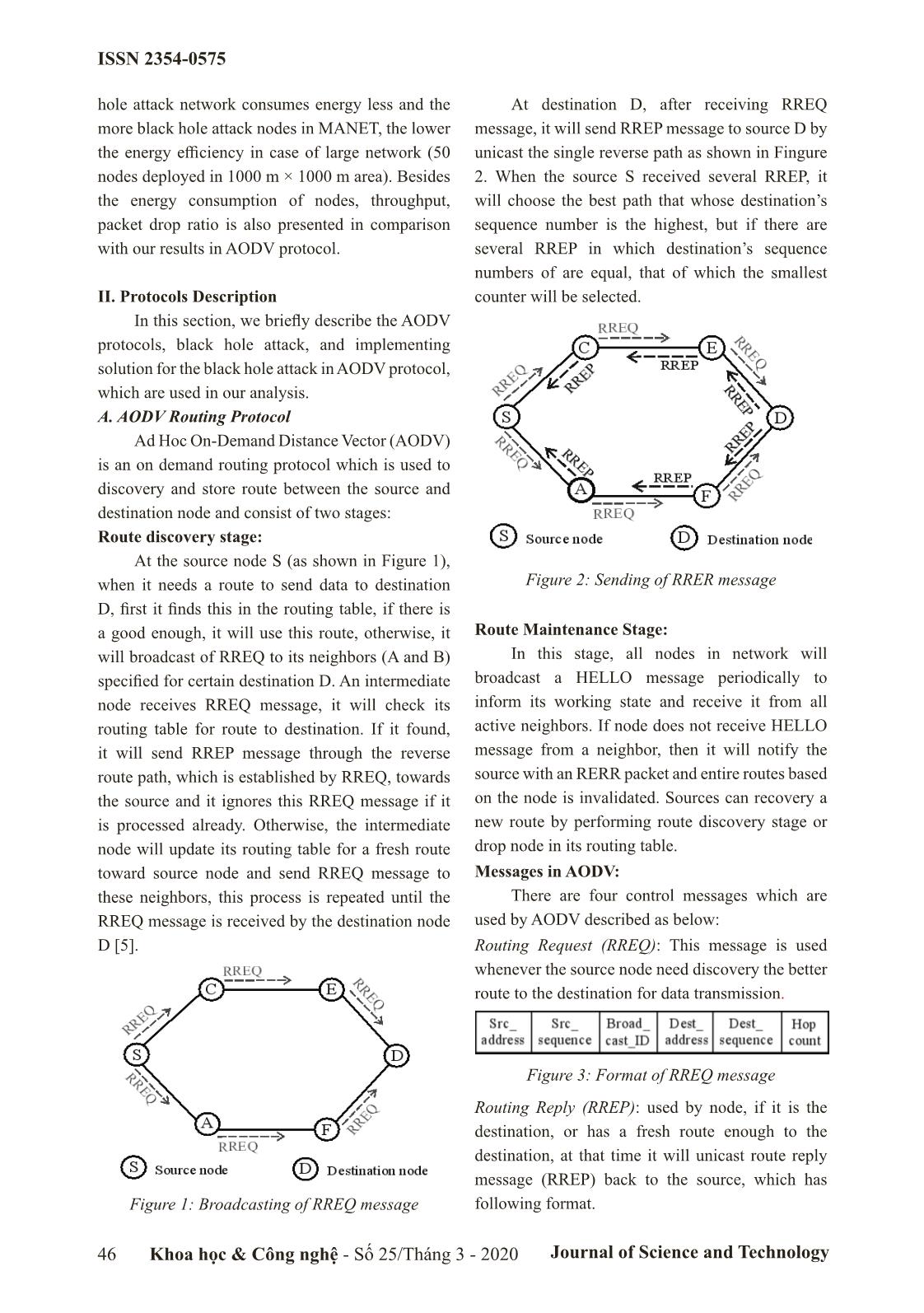
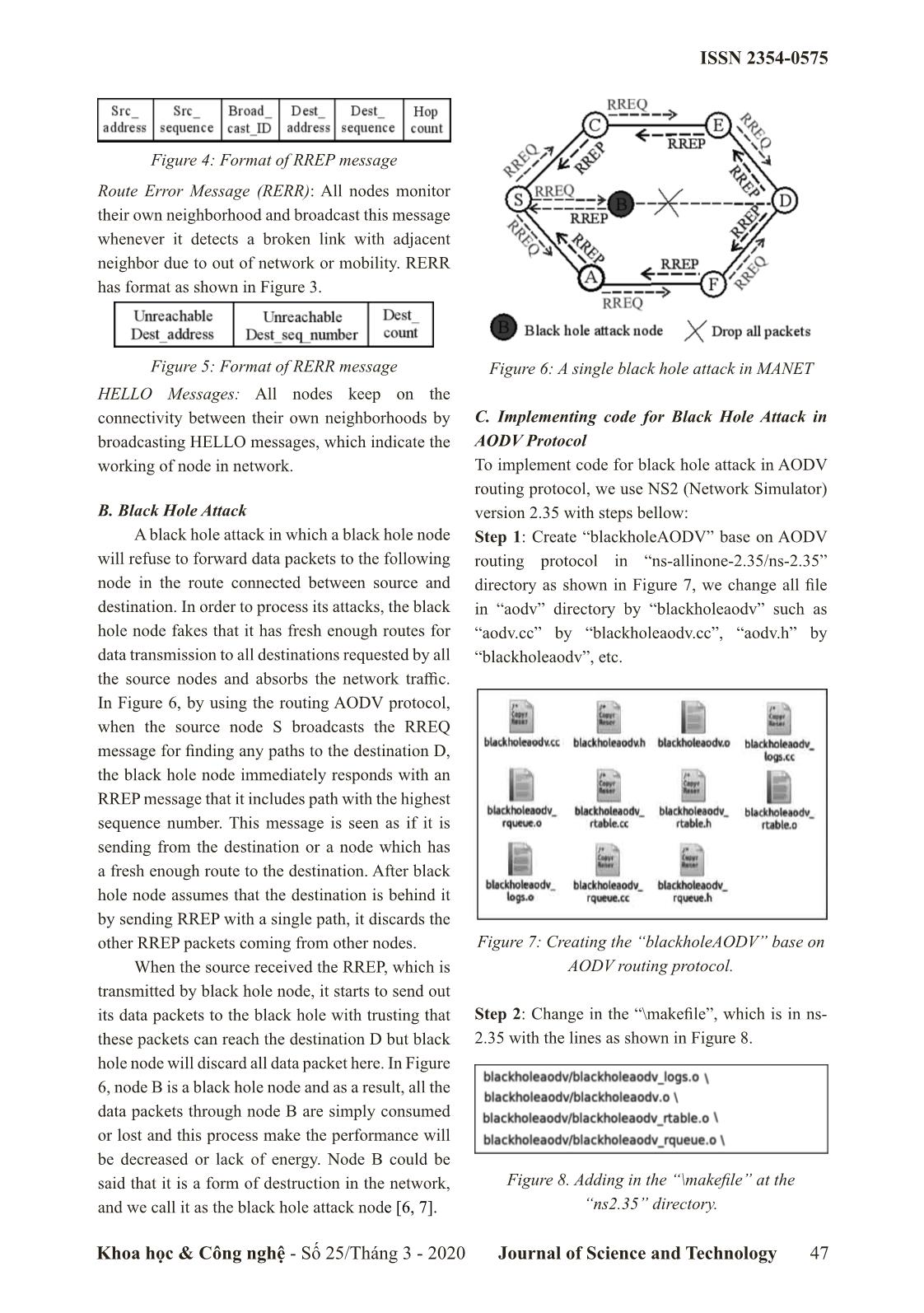
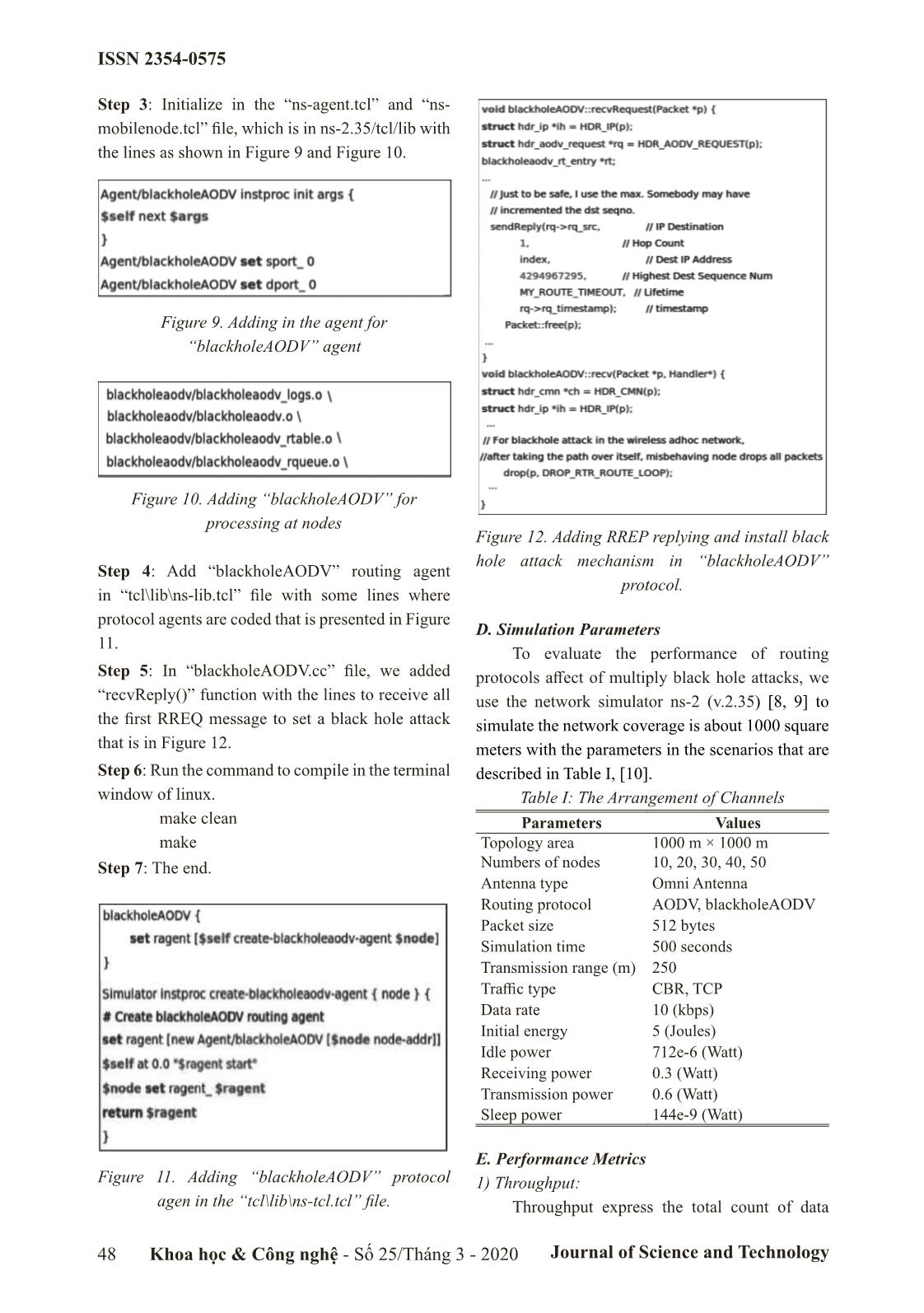
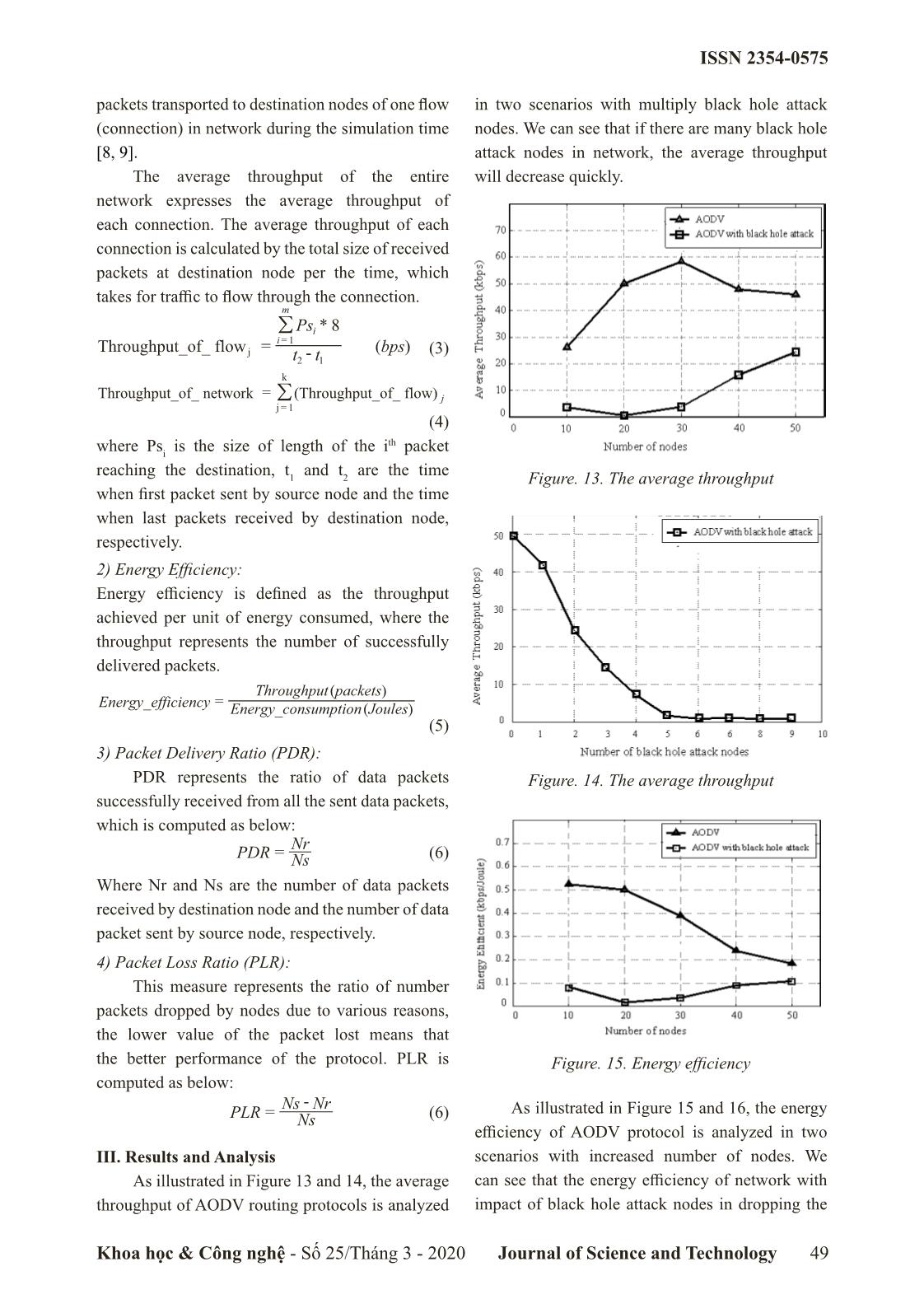
destination’s packet drop ratio is also presented in comparison sequence number is the highest, but if there are with our results in AODV protocol. several RREP in which destination’s sequence numbers of are equal, that of which the smallest II. Protocols Description counter will be selected. In this section, we briefly describe the AODV protocols, black hole attack, and implementing solution for the black hole attack in AODV protocol, which are used in our analysis. A. AODV Routing Protocol Ad Hoc On-Demand Distance Vector (AODV) is an on demand routing protocol which is used to discovery and store route between the source and destination node and consist of two stages: Route discovery stage: At the source node S (as shown in Figure 1), when it needs a route to send data to destination Figure 2: Sending of RRER message D, first it finds this in the routing table, if there is a good enough, it will use this route, otherwise, it Route Maintenance Stage: will broadcast of RREQ to its neighbors (A and B) In this stage, all nodes in network will specified for certain destination D. An intermediate broadcast a HELLO message periodically to node receives RREQ message, it will check its inform its working state and receive it from all routing table for route to destination. If it found, active neighbors. If node does not receive HELLO it will send RREP message through the reverse message from a neighbor, then it will notify the route path, which is established by RREQ, towards source with an RERR packet and entire routes based the source and it ignores this RREQ message if it on the node is invalidated. Sources can recovery a is processed already. Otherwise, the intermediate new route by performing route discovery stage or node will update its routing table for a fresh route drop node in its routing table. toward source node and send RREQ message to Messages in AODV: these neighbors, this process is repeated until the There are four control messages which are RREQ message is received by the destination node used by AODV described as below: D [5]. Routing Request (RREQ): This message is used whenever the source node need discovery the better route to the destination for data transmission. Figure 3: Format of RREQ message Routing Reply (RREP): used by node, if it is the destination, or has a fresh route enough to the destination, at that time it will unicast route reply message (RREP) back to the source, which has Figure 1: Broadcasting of RREQ message following format. 46 Khoa học & Công nghệ - Số 25/Tháng 3 - 2020 Journal of Science and Technology ISSN 2354-0575 Figure 4: Format of RREP message Route Error Message (RERR): All nodes monitor their own neighborhood and broadcast this message whenever it detects a broken link with adjacent neighbor due to out of network or mobility. RERR has format as shown in Figure 3. Figure 5: Format of RERR message Figure 6: A single black hole attack in MANET HELLO Messages: All nodes keep on the connectivity between their own neighborhoods by C. Implementing code for Black Hole Attack in broadcasting HELLO messages, which indicate the AODV Protocol working of node in network. To implement code for black hole attack in AODV routing protocol, we use NS2 (Network Simulator) B. Black Hole Attack version 2.35 with steps bellow: A black hole attack in which a black hole node Step 1: Create “blackholeAODV” base on AODV will refuse to forward data packets to the following routing protocol in “ns-allinone-2.35/ns-2.35” node in the route connected between source and directory as shown in Figure 7, we change all file destination. In order to process its attacks, the black in “aodv” directory by “blackholeaodv” such as hole node fakes that it has fresh enough routes for “aodv.cc” by “blackholeaodv.cc”, “aodv.h” by data transmission to all destinations requested by all “blackholeaodv”, etc. the source nodes and absorbs the network traffic. In Figure 6, by using the routing AODV protocol, when the source node S broadcasts the RREQ message for finding any paths to the destination D, the black hole node immediately responds with an RREP message that it includes path with the highest sequence number. This message is seen as if it is sending from the destination or a node which has a fresh enough route to the destination. After black hole node assumes that the destination is behind it by sending RREP with a single path, it discards the other RREP packets coming from other nodes. Figure 7: Creating the “blackholeAODV” base on When the source received the RREP, which is AODV routing protocol. transmitted by black hole node, it starts to send out its data packets to the black hole with trusting that Step 2: Change in the “\makefile”, which is in ns- these packets can reach the destination D but black 2.35 with the lines as shown in Figure 8. hole node will discard all data packet here. In Figure 6, node B is a black hole node and as a result, all the data packets through node B are simply consumed or lost and this process make the performance will be decreased or lack of energy. Node B could be said that it is a form of destruction in the network, Figure 8. Adding in the “\makefile” at the and we call it as the black hole attack node [6, 7]. “ns2.35” directory. Khoa học & Công nghệ - Số 25/Tháng 3 - 2020 Journal of Science and Technology 47 ISSN 2354-0575 Step 3: Initialize in the “ns-agent.tcl” and “ns- mobilenode.tcl” file, which is in ns-2.35/tcl/lib with the lines as shown in Figure 9 and Figure 10. Figure 9. Adding in the agent for “blackholeAODV” agent Figure 10. Adding “blackholeAODV” for processing at nodes Figure 12. Adding RREP replying and install black hole attack mechanism in “blackholeAODV” Step 4: Add “blackholeAODV” routing agent protocol. in “tcl\lib\ns-lib.tcl” file with some lines where protocol agents are coded that is presented in Figure D. Simulation Parameters 11. To evaluate the performance of routing Step 5: In “blackholeAODV.cc” file, we added protocols affect of multiply black hole attacks, we “recvReply()” function with the lines to receive all use the network simulator ns-2 (v.2.35) [8, 9] to the first RREQ message to set a black hole attack simulate the network coverage is about 1000 square that is in Figure 12. meters with the parameters in the scenarios that are Step 6: Run the command to compile in the terminal described in Table I, [10]. window of linux. Table I: The Arrangement of Channels make clean Parameters Values make Topology area 1000 m × 1000 m Step 7: The end. Numbers of nodes 10, 20, 30, 40, 50 Antenna type Omni Antenna Routing protocol AODV, blackholeAODV Packet size 512 bytes Simulation time 500 seconds Transmission range (m) 250 Traffic type CBR, TCP Data rate 10 (kbps) Initial energy 5 (Joules) Idle power 712e-6 (Watt) Receiving power 0.3 (Watt) Transmission power 0.6 (Watt) Sleep power 144e-9 (Watt) E. Performance Metrics Figure 11. Adding “blackholeAODV” protocol 1) Throughput: agen in the “tcl\lib\ns-tcl.tcl” file. Throughput express the total count of data 48 Khoa học & Công nghệ - Số 25/Tháng 3 - 2020 Journal of Science and Technology ISSN 2354-0575 packets transported to destination nodes of one flow in two scenarios with multiply black hole attack (connection) in network during the simulation time nodes. We can see that if there are many black hole [8, 9]. attack nodes in network, the average throughput The average throughput of the entire will decrease quickly. network expresses the average throughput of each connection. The average throughput of each connection is calculated by the total size of received packets at destination node per the time, which takes for traffic to flow through the connection. m / Psi *8 i = 1 Throughput_of_ flowj = ()bps (3) tt21- k Throughput_of_ network = / (Throughput_of_ flow) j j1= (4) th where Psi is the size of length of the i packet reaching the destination, t and t are the time 1 2 Figure. 13. The average throughput when first packet sent by source node and the time when last packets received by destination node, respectively. 2) Energy Efficiency: Energy efficiency is defined as the throughput achieved per unit of energy consumed, where the throughput represents the number of successfully delivered packets. Throughput()packets _ = Energy efficiency Energy_(consumptionJoules) (5) 3) Packet Delivery Ratio (PDR): PDR represents the ratio of data packets Figure. 14. The average throughput successfully received from all the sent data packets, which is computed as below: Nr PDR = Ns (6) Where Nr and Ns are the number of data packets received by destination node and the number of data packet sent by source node, respectively. 4) Packet Loss Ratio (PLR): This measure represents the ratio of number packets dropped by nodes due to various reasons, the lower value of the packet lost means that the better performance of the protocol. PLR is Figure. 15. Energy efficiency computed as below: - = Ns Nr As illustrated in Figure 15 and 16, the energy PLR Ns (6) efficiency of AODV protocol is analyzed intwo III. Results and Analysis scenarios with increased number of nodes. We As illustrated in Figure 13 and 14, the average can see that the energy efficiency of network with throughput of AODV routing protocols is analyzed impact of black hole attack nodes in dropping the Khoa học & Công nghệ - Số 25/Tháng 3 - 2020 Journal of Science and Technology 49 ISSN 2354-0575 packets to reduce the received packets is obvious. The percentage of packet loss in different two In addition, in network with the more black hole scenarios are illustrated in Figures 19 and 20 in attack nodes, the worse energy efficiency achieve. which in network with black hole attack nodes have In Figure 17 and 18, we illustrate the packet packet loss ratio more than original AODV protocol delivery ratio for AODV routing protocols in the and the more black hole attack nodes, the more number of black hole attack nodes. Based on results packet loss ratio in the same protocol. shown in Figure 17 and 18, we can obviously observe that if there is not black hole attack in the network, the packet delivery ratio is higher than about 40% compared to the same protocols. Figure. 19. Energy consumption in several states with IEEE 802.11 MAC Figure. 16. Energy efficiency Figure. 20. Energy consumption in several states Figure. 17. Packet delivery ratio with S-MAC IV. Conclusion In this paper, we analyzed the energy consumption of nodes in MANET with implementing black hole attack with AODV routing protocols. Our goal is to implement and evaluate impact of black hole attack to performance in AODV routing protocol, which helps the development of security schemes in MANET. Our simulation results show that the more black hole attack nodes in network, the lower performance in case of large network (50 Figure. 18. Packet delivery ratio nodes deployed in 1000 m × 1000 m area). 50 Khoa học & Công nghệ - Số 25/Tháng 3 - 2020 Journal of Science and Technology ISSN 2354-0575 References [1]. Fan-Hsun Tseng, Li-Der Chou and Han-Chieh Chao, “A survey of black hole attacks in wireless mobile ad hoc networks”, Human-centric Computing and Information Sciences, vol 1, pp. 1-16, 2011. [2]. Garima Neekhra, Sharda Patel, Ashok Verma, Ashish Chaurasia, “Effect Of Grayhole Attack With Ids Technique For Aodv Routing Protocol Using Network Simulator”, International Journal of Advanced Research in Computer Engineering & Technology (IJARCET), vol 3, pp. 4184- 4190, December 2014. [3]. K.Madhuri, N.Kasi Viswanath, P.Usha Gayatri, “Performance Evaluation of AODV under Black Hole Attack in MANET using NS2”, International Conference on ICT in Business Industry Government (ICTBIG), pp. 1-3, November 2016. [4]. Kriti Chadha and Sushma Jain, “Impact Of Black Hole And Gray Hole Attack In AODV Protocol”, IEEE International Conference on Recent Advances and Innovations in Engineering (ICRAIE), pp. 1-7, May 2014. [5]. Mehdi Medadian, M.H. Yektaie, A.M Rahmani, “Combat with Black Hole Attack in AODV routing protocol in MANET”, First Asian Himalayas International Conference on Internet, pp. 1-5, November 2009. [6]. Padmalaya Nayak, V. Bhavani and B. Lavanya, “Impact of Black Hole and Sink Hole Attacks on Routing Protocols for WSN”, International Journal of Computer Applications, vol 116, pp. 42-46, April 2015. [7]. Semih Dokurer, Y. M. Erten and Can Erkin Acar, “Performance analysis of ad-hoc networks under black hole attacks”, IEEE SoutheastCon Proceedings, pp. 148-153, March, 2007. [8]. T.Sairam Vamsi, E.R. Praveen Kumar, T.Sruthi, “Performance Analysis of Aodv Routing Protocol in Manet under Blackhole Attack”, International Journal of Engineering Research and Applications, vol. 9, pp. 58-63, May 2019. [9]. Yatin Chauhan, Jaikaran Singh, Mukesh Tiwari, Anubhuti Khare, “Performance Evaluation of AODV based on black hole attack in ad hoc network”, Global Journal of researches in engineering Electrical and electronics engineering, Vol. 12, pp. 43-47, February 2012. [10]. VINT Project, “The network simulator - NS2,” (accessed: Sep 5, 2019), 1997. TRIỂN KHAI TẤN CÔNG HỐ ĐEN TRÊN GIAO THỨC ĐỊNH TUYẾN AODV TRONG MẠNG MANET SỬ DỤNG NS2 Tóm tắt: Một trong những thách thức lớn của mạng di động tùy biến (MANETs) là làm sao triển khai hệ thống an ninh tránh các loại tấn công khác nhau như tấn công từ chối dịch vụ, tấn công lỗ sâu, phát lại, tấn công lỗ xám, lỗ đen, v.v ... Mạng MANET sử dụng giao thức định tuyến để truyền thông gói dữ liệu từ nút nguồn đến nút đích và mỗi nút đóng vai trò như là máy chủ hoặc bộ định tuyến, chúng có thể chọn các tuyến đường phù hợp để truyền gói tin đến đích. AODV là một trong các giao thức định tuyến được sử dụng phổ biến nhất trong các mạng di động tùy biến, nhưng nó cũng tiềm ẩn nhiều cuộc tấn công mạng. Mục tiêu của cuộc tấn công mạng thường làm gián đoạn hoạt động của mạng hoặc ảnh hưởng đến hiệu suất mạng. Trong bài báo này, chúng tôi thực hiện triển khai và phân tích hiệu suất của nhiều nút tấn công lỗ đen đồng thời trong giao thức định tuyến AODV. Các tham số như thông lượng, hiệu quả sử dụng năng lượng và hiệu suất phân phối gói dữ liệu được phân tích và so sánh. Kết quả mô phỏng của chúng tôi cho thấy trong mạng có càng nhiều nút tấn công đồng thời, hiệu suất mạng và hiệu quả năng lượng càng thấp. Từ khóa: Security threats, Routing Protocols, AODV, MANET, Black hole attack, Network Simulator. Khoa học & Công nghệ - Số 25/Tháng 3 - 2020 Journal of Science and Technology 51
File đính kèm:
 implementation_of_black_hole_attack_on_aodv_routing_protocol.pdf
implementation_of_black_hole_attack_on_aodv_routing_protocol.pdf

