Statistical assessment of two rekeying mechanisms applied to the generation of random numbers
During the encryption process of a message
with a mode of operation, the values of the
pseudo-random permutation determined by the
secret key are tours. Then, if the length of the
message exceeds the lifetime of the key, the
encryption process can be seriously compromised
[1]. This determines for each mode of operation
the maximum number of blocks that can be
processed with the same key, and therefore, a
message of length greater than this amount
cannot be encrypted without changing the key
first. Bounds for the life time of a key in some
modes of operation can be seen in [2], [3].
Rekeying mechanisms are used to encrypt a
large amount of data with a specific mode of
operation, with the peculiarity that for every
certain amount of processed blocks, a new key is
generated and used to process the following
blocks of the message used to process the
following blocks of the message. This new
approach, which is well-studied and
recommended in the last few years [4]-[12],
ensures that encryption remains secure even
when the message is very large, by changing the
key periodically. It can be applied on three levels:
on the block cipher level (fresh rekeying), on the
block cipher mode of operation level (internal
rekeying), and on the message processing level
(external rekeying).

Trang 1

Trang 2
Trang 3

Trang 4
Trang 5

Trang 6

Trang 7
Tóm tắt nội dung tài liệu: Statistical assessment of two rekeying mechanisms applied to the generation of random numbers

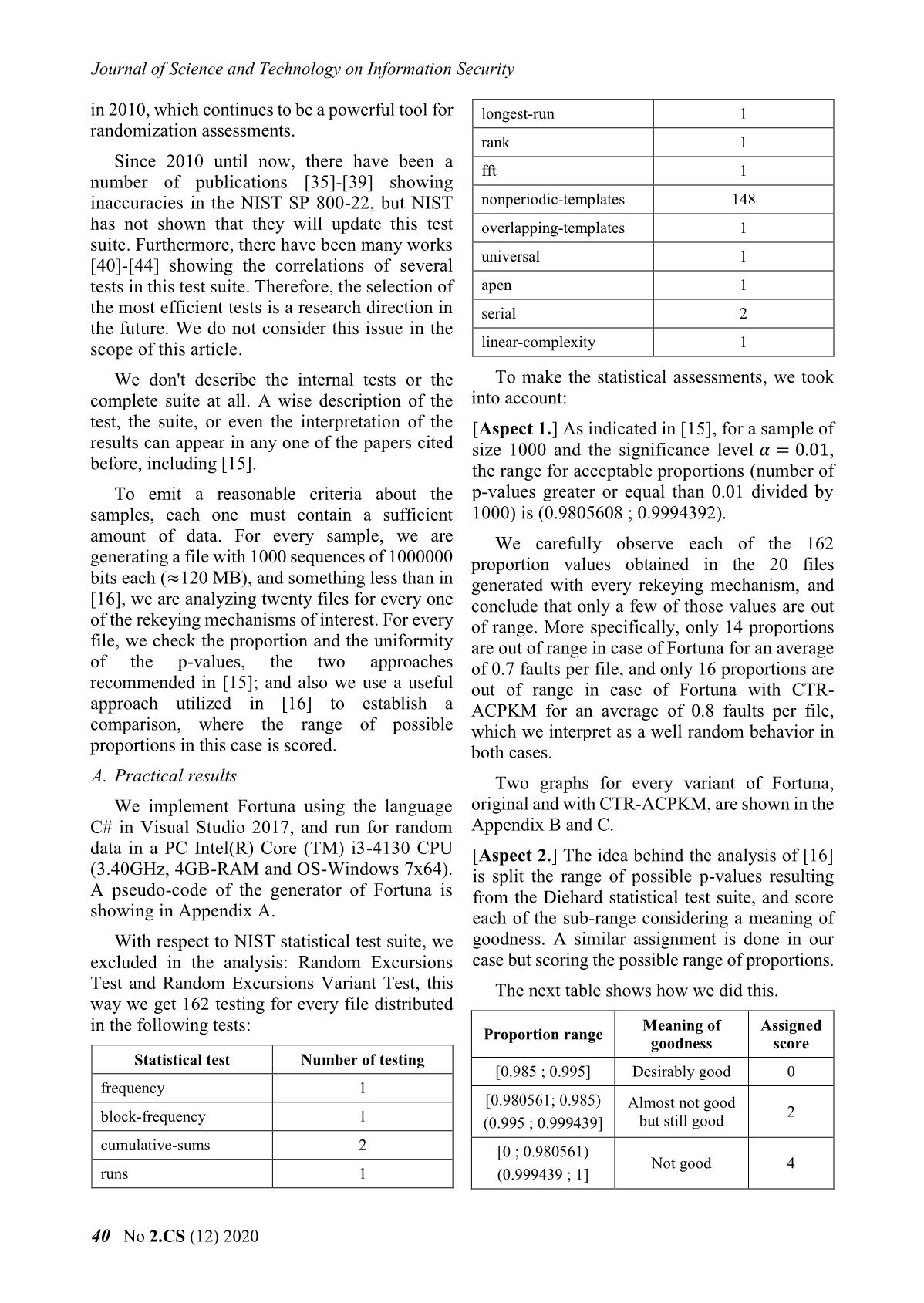
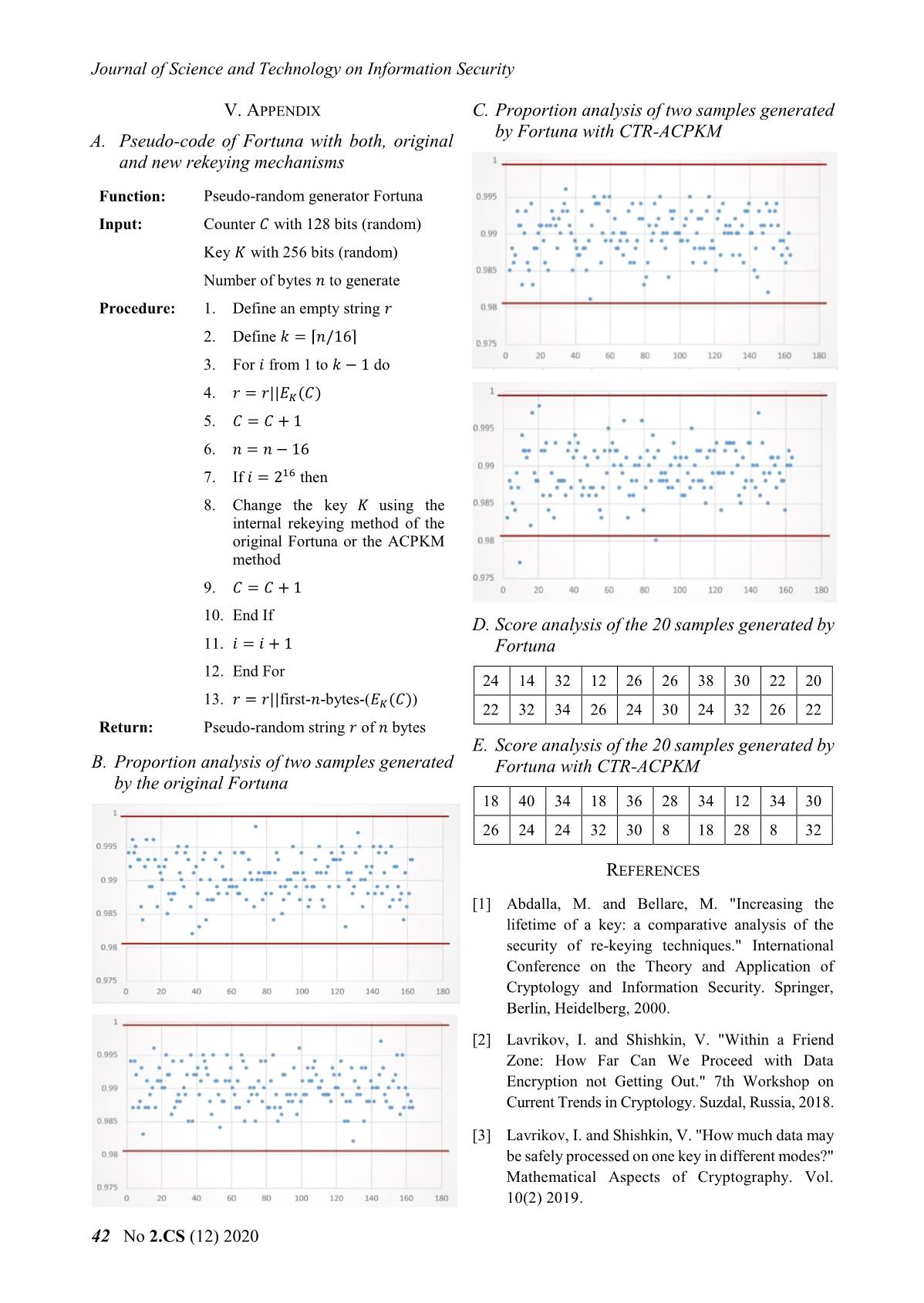
range goodness score Statistical test Number of testing [0.985 ; 0.995] Desirably good 0 frequency 1 [0.980561; 0.985) Almost not good 2 block-frequency 1 (0.995 ; 0.999439] but still good cumulative-sums 2 [0 ; 0.980561) Not good 4 runs 1 (0.999439 ; 1] 40 No 2.CS (12) 2020 Khoa học và Công nghệ trong lĩnh vực An toàn thông tin Only for uniformity at the check of that We recommend the use of Fortuna, and so of criteria, we excluded of the NIST suite: Random Fortuna with CTR-ACPKM, in real and practical Excursions Test and Random Excursions Variant applications. Nevertheless, it should be taken into Test, since both analyze only an arbitrary amount account that each generated sequence must be of sequences which satisfy some conditions. A carefully analyzed for randomness before being similar approach is adopted in [33], [34]. used although similar results are expected. This way, with the remaining tests, we IV. CONCLUSION evaluate 162 proportion values per file, and the Generation of keys, initialization vectors, accumulated score gives us another idea of seeds, and other kinds of sequences with random goodness. The possible best score is 0 and the behavior play a fundamental role in possible worst score is 648 for every file. cryptography. Thus, a pseudo-random number A comparative analysis between the twenty generator cryptographically strong with proven files generated with Fortuna and the twenty files pseudo-random behavior is a powerful tool in generated with the proposed variant is shown this area. below. All results have been tabulated and are The used simple technique is the shown in the Appendix D, E. These results do not implementation of one block cipher algorithm throw significant differences between both using one mode of operation. This way, good variants, and we appreciate a random behavior random behavior is achieved if the underlying since the final score of every file is very low. encryption method has good diffusion properties. Generator Score The pseudo-random number generator 12 – best score Fortuna is based on this principle, using the Fortuna (original) 38 – worst score standard AES and the mode of operation CTR as underlying primitives, and one internal rekeying 8 – best score Fortuna-CTR-ACPKM mechanism proposed by their own designers. 40 – worst score In this paper, we have analyzed the random [Aspect 3.] The other approach according to [15] behavior of the sequences generated by Fortuna is to examine the distribution of the p-values in as well as a variant that uses another internal the range [0 ; 1], so this interval is divided into rekeying mechanism that included in the ten equal sub-intervals and then the number of p- Russian Standardization System and named values that lie within each sub-interval are CTR-ACPKM. In both cases, twenty files of 120 counted. The optimal case for randomness is that MB were generated, all of them show a good 100 p-values fall in each sub-interval. random behavior. As reference we used the NIST test suite, The NIST test suite returns a p-value of p- although we have removed from it two tests and values in every testing, corresponding to the chi have included an extra analysis technique square test for the same ones. If that p-value is performed previously, but using the Diehard greater than 0.0001, then the sequence can be statistical test suite. In terms of this approach, the considered to be uniformly distributed, in all the sequences generated by Fortuna seem as random checks carried out this was satisfactorily fulfilled. as the sequences generated by the variant of B. Final considerations Fortuna, although the difference observed is really small to make a comparison between the Both the original Fortuna and Fortuna with the two kinds of sequences. internal rekeying mechanism CTR-ACPKM, have shown that the generated sequences have a To conclude this paper, we propose the random behavior. The performing tests do not application of the two analyzed pseudo-random offer sufficient reasons to establish a significant number generators, Fortuna and Fortuna with comparison between both types of generated internally rekeying mechanism CTR-ACPKM, in sequence actually, using the criteria established real and practical applications, as long as the in [16] the sequences generated by Fortuna have generated sequences in both cases are previously similar randomness than the other kind of analyzed and show a random behavior similar to generated sequences. the examples shown here. Số 2.CS (12) 2020 41 Journal of Science and Technology on Information Security V. APPENDIX C. Proportion analysis of two samples generated by Fortuna with CTR-ACPKM A. Pseudo-code of Fortuna with both, original and new rekeying mechanisms Function: Pseudo-random generator Fortuna Input: Counter with 128 bits (random) Key 퐾 with 256 bits (random) Number of bytes 푛 to generate Procedure: 1. Define an empty string 2. Define = ⌈푛/16⌉ 3. For 푖 from 1 to − 1 do 4. = || 퐾( ) 5. = + 1 6. 푛 = 푛 − 16 7. If 푖 = 216 then 8. Change the key 퐾 using the internal rekeying method of the original Fortuna or the ACPKM method 9. = + 1 10. End If D. Score analysis of the 20 samples generated by 11. 푖 = 푖 + 1 Fortuna 12. End For 24 14 32 12 26 26 38 30 22 20 13. = ||first-푛-bytes-( ( )) 퐾 22 32 34 26 24 30 24 32 26 22 Return: Pseudo-random string of 푛 bytes E. Score analysis of the 20 samples generated by B. Proportion analysis of two samples generated Fortuna with CTR-ACPKM by the original Fortuna 18 40 34 18 36 28 34 12 34 30 26 24 24 32 30 8 18 28 8 32 REFERENCES [1] Abdalla, M. and Bellare, M. "Increasing the lifetime of a key: a comparative analysis of the security of re-keying techniques." International Conference on the Theory and Application of Cryptology and Information Security. Springer, Berlin, Heidelberg, 2000. [2] Lavrikov, I. and Shishkin, V. "Within a Friend Zone: How Far Can We Proceed with Data Encryption not Getting Out." 7th Workshop on Current Trends in Cryptology. Suzdal, Russia, 2018. [3] Lavrikov, I. and Shishkin, V. "How much data may be safely processed on one key in different modes?" Mathematical Aspects of Cryptography. Vol. 10(2) 2019. 42 No 2.CS (12) 2020 Khoa học và Công nghệ trong lĩnh vực An toàn thông tin [4] Medwed, M., Standaert, F., Großschädl, J. and Pseudorandom Number Generators for Regazzoni, F. "Fresh re-keying: Security against Cryptographic Applications.” NIST Special side-channel and fault attacks for low-cost Publication 800-22, 2010. devices." International Conference on Cryptology [16] McEvoy, R., Curran, J., Cotter, P. and Murphy, C. in Africa. Springer, Berlin, Heidelberg, 2010. "Fortuna: cryptographically secure pseudo-random [5] Abdalla, M., Belaïd, S. and Fouque, P. "Leakage- number generation in software and hardware." 2006. resilient symmetric encryption via re-keying." [17] Akbar, M. and Zulkifl, M. "Fuzzy-Fortuna: A International Workshop on Cryptographic fuzzified approach to generation of Hardware and Embedded Systems. Springer, cryptographically secure pseudo-random Berlin, Heidelberg, 2013. numbers." IEEE International Multitopic [6] Dobraunig, C., et al. "Towards fresh and hybrid Conference. IEEE, 2008. re-keying schemes with beyond birthday [18] Yevgeniy, D., Shamir, A., Stephens-Davidowitz, security." International Conference on Smart N. and Wichs, D. "How to eat your entropy and Card Research and Advanced Applications. have it too: Optimal recovery strategies for Springer, 2015. compromised RNGs." Algorithmica, 79 (4), 2017. [7] Gueron, S. and Yehuda L. "Better bounds for block [19] Marsaglia, G. "Diehard Battery of Tests of cipher modes of operation via nonce-based key Randomness." 1985. derivation." Proceedings of the 2017 Conference [20] Soto, J. "Randomness testing of the advanced on Computer and Communications Security. encryption standard candidate algorithms." National ACM, 2017. Institute of Standards and Technology, 1999. [8] Ahmetzyanova, R., et al. "Increasing the Lifetime [21] El-Fotouh, M. and Diepold, K. "Statistical Testing of Symmetric Keys for the GCM Mode by Internal for Disk Encryption Modes of Operations." IACR Re-keying." IACR Cryptology ePrint Archive, Cryptology ePrint Archive, 362, 2007. 697, 2017. [22] Santoro, R., Sentieys, O. and Roy, S. "On-the-fly [9] Goncharenko, K., Alekseev, E. and Marshalko, G. evaluation of FPGA-based true random number “Provably secure counter mode with related key- generator." IEEE, 2009. based internal rekeying." 7th Workshop on Current Trends in Cryptology. Suzdal, Russia, 2018. [23] Doganaksoy, A. et al. "Cryptographic Randomness Testing of Block Ciphers and Hash [10] Akhmetzyanova, L., Alekseev, K. and Smyshlyaev, Functions." IACR Cryptology ePrint Archive, V. "Security bound for СTR-ACPKM internally re- 564, 2010. keyed encryption mode." 2018. [24] Chen, X., et al. "Evaluation of ECG random [11] Akhmetzyanova, L., et al. "Security bounds for number generator for wireless body sensor standardized internally re-keyed block cipher networks security." 5th International Conference modes and their practical significance." 7th on BioMedical Engineering and Informatics. Workshop on Current Trends in Cryptology. IEEE, 2012. Suzdal, Russia, 2018. [25] Zubkov, A. and Serov, A. "Testing the NIST [12] Akhmetzyanova, L., et al. "Practical significance of Statistical Test Suite on artificial pseudorandom security bounds for standardized internally re- sequences." Mathematical Aspect of keyed block cipher modes" Mathematical Aspects Cryptography, 10(2), 2019. of Cryptography. Vol. 10(2) 2019. [26] Kim, S., Ken U. and Hasegawa, A. "Corrections of [13] Ferguson, N., Schneier, B. and Kohno, T. the NIST statistical test suite for "Cryptography Engineering. Design, Principles and randomness." 2004. Practical Applications." Wiley Publishing Inc., [27] Suciu, A., et al. "Parallel implementation of the 2010. Chapter 9. (Second version of "Practical NIST statistical test suite." Proceedings of the Cryptography." Wiley Publishing Inc., 2003.) 2010 IEEE 6th International Conference on [14] CryptoPro. "Re-keying Mechanisms for Intelligent Computer Communication and Symmetric Keys draft-irtf-cfrg-re-keying-00." Processing. IEEE, 2010. Internet-Draft, 2017. [28] Zhu, S., et al. "More powerful and reliable second- [15] National Institute of Standards and Technology. "A level statistical randomness tests for NIST SP 800- Statistical Test Suite for Random and 22." International Conference on the Theory and Số 2.CS (12) 2020 43 Journal of Science and Technology on Information Security Application of Cryptology and Information Engineering & Computer Sciences 25.2 (2017): Security. Springer, Berlin, Heidelberg, 2016. 655-665. [29] Chugunkov, I., Prokofiev, A. and Strelchenko, P. [41] Doğnaksoy, A., Barış Ege, and Köksal Muş. "The optimization of statistical tests for "Extended results for independence and sensitivity pseudorandom number generators." IEEE, 2016. of NIST randomness tests." Information Security [30] Simion, Emil, and Paul Burciu. "A Note On the and Cryptography Conference, ISC Turkey. 2008. Correlations Between NIST Cryptographic [42] Jorge Augusto Karell-Albo, Carlos Miguel Legón- Statistical Tests Suite." 2019. Pérez, Evaristo José Madarro-Capó, Omar Rojas, [31] Burciu, P. and Simion, E. "A Systematic Approach and Guillermo Sosa-Gómez. Measuring of NIST Statistical Tests Dependencies." Journal of independence between statistical randomness tests Electrical Engineering, Electronics, Control and by mutual information. Entropy, 22(7):741, 2020. Computer Science. 5(1), 2019. [43] Koçak, Onur. "A unified evaluation of statistical [32] Mishra, P., Nandan, B. and Gaba, N. "An Efficient randomness tests and experimental analysis of their and Compact Reformulation of NIST Collision relations." 2016. Estimate Test." IACR Cryptology ePrint Archive, [44] Sulak, Fatih, et al. "On the independence of 481, 2019. statistical randomness tests included in the NIST [33] Okutomi, H., Nakamura, K., and Aihara, K. "A test suite." Turkish Journal of Electrical study on rational judgment method of randomness Engineering & Computer Sciences 25.5. 2017. pp. property using NIST randomness test (NIST SP. 3673-3683. 800-22)." IEICE Trans. A, 93 (1), 2010, pp. 11-22. [34] Iwasaki, A. "Analysis of NIST SP800-22 focusing ABOUT THE AUTHOR on randomness of each sequence." JSIAM Letters, Vol. 10, pp. 1-4, 2018. Adrián Alfonso Peñate [35] T. Yuichi, H.M., K. Toshinari, W. Norio, S. Workplace: Institute of Takakazu, The Suggestion of Corrected Non- Cryptography. University of Havana. overlapping Template Matching Test [in Japanese]. Education: Graduated of Technical report of IEICE., 2010. Mathematics in 2014; received his Master's degree in 2018. [36] Pareschi, F., R. Rovatti, and G. Setti, On statistical Current research direction: design tests for randomness included in the NIST SP800- and analysis of block ciphers. 22 test suite and based on the binomial distribution. IEEE Transactions on Information Forensics and Security, 2012. 7(2): pp. 491-505. Daymé Almeida Echevarria Workplace: Institute of [37] Takeda, Y., et al., Modified Non-overlapping Cryptography. University of Havana. template matching test and proposal on setting Education: Graduated of template. 2014. 27(1): pp. 49-60. Mathematics in 2013; currently [38] Okada, H. and K. Umeno, Randomness evaluation aspires to pursue her Master's degree. with the discrete Fourier transform test based on Current research direction: design and analysis of exact analysis of the reference distribution. IEEE rekeying mechanisms for block ciphers modes of Transactions on Information Forensics Security, operation. 2017. 12(5): pp. 1218-1226. Laura Castro Argudín [39] Iwasaki, A. and K. Umeno, A new randomness test solving problems of Discrete Fourier Transform Workplace: Institute of Test. arXiv preprint arXiv:.08218, 2017. Cryptography. University of Havana. The education process: Graduated of [40] DOĞANAKSOY, ALİ, et al. "Mutual correlation Cryptology in 2019. of NIST statistical randomness tests and Current research direction: design comparison of their sensitivities on transformed and analysis of pseudo-random sequences." Turkish Journal of Electrical number generators. 44 No 2.CS (12) 2020
File đính kèm:
 statistical_assessment_of_two_rekeying_mechanisms_applied_to.pdf
statistical_assessment_of_two_rekeying_mechanisms_applied_to.pdf

