Solution for cryptographic intervention in pci - express data transmission on FPGA board
Với đường truyền dữ liệu tốc độ cao
như PCI-Express, việc can thiệp mật mã vào trong
đường truyền để không ảnh hưởng đến quá trình
truyền dữ liệu mà vẫn đảm bảo được tốc độ truyền
dữ liệu của giao thức mang lại sẽ là cơ sở để phát
triển các ứng dụng mật mã sử dụng giao thức PCIExpress. Trong bài báo này sẽ trình bày một giải
pháp kỹ thuật bắt gói tin dữ liệu của giao thức
PCI-Express sử dụng công nghệ FPGA. Sử dụng
bộ thư viện chuẩn PCI-Express trên máy tính để
thực hiện kết nối tới bo mạch FPGA, qua đó trên
FPGA thực hiện tổ chức dữ liệu theo chuẩn giao
thức PCI-Express, đồng thời tổ chức can thiệp mật
mã trên đường truyền. Như vậy, dữ liệu rõ sẽ được
truyền từ máy tính xuống bo mạch FPGA thông
qua giao tiếp PCI-Express, sau đó được tổ chức,
can thiệp mật mã và truyền lại cho máy tính.

Trang 1
Trang 2
Trang 3
Trang 4
Trang 5
Trang 6
Trang 7

Trang 8

Trang 9

Trang 10
Tóm tắt nội dung tài liệu: Solution for cryptographic intervention in pci - express data transmission on FPGA board

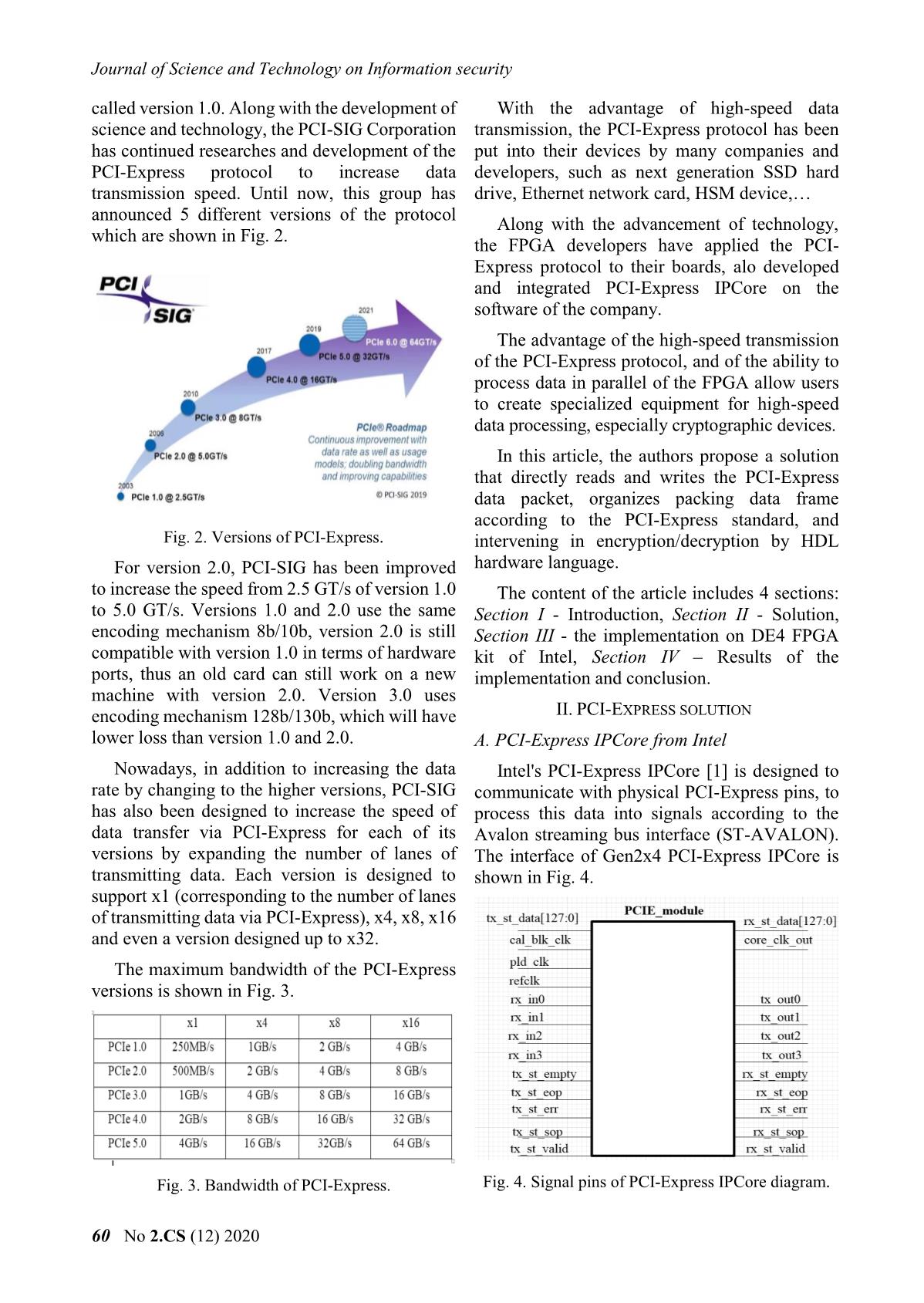
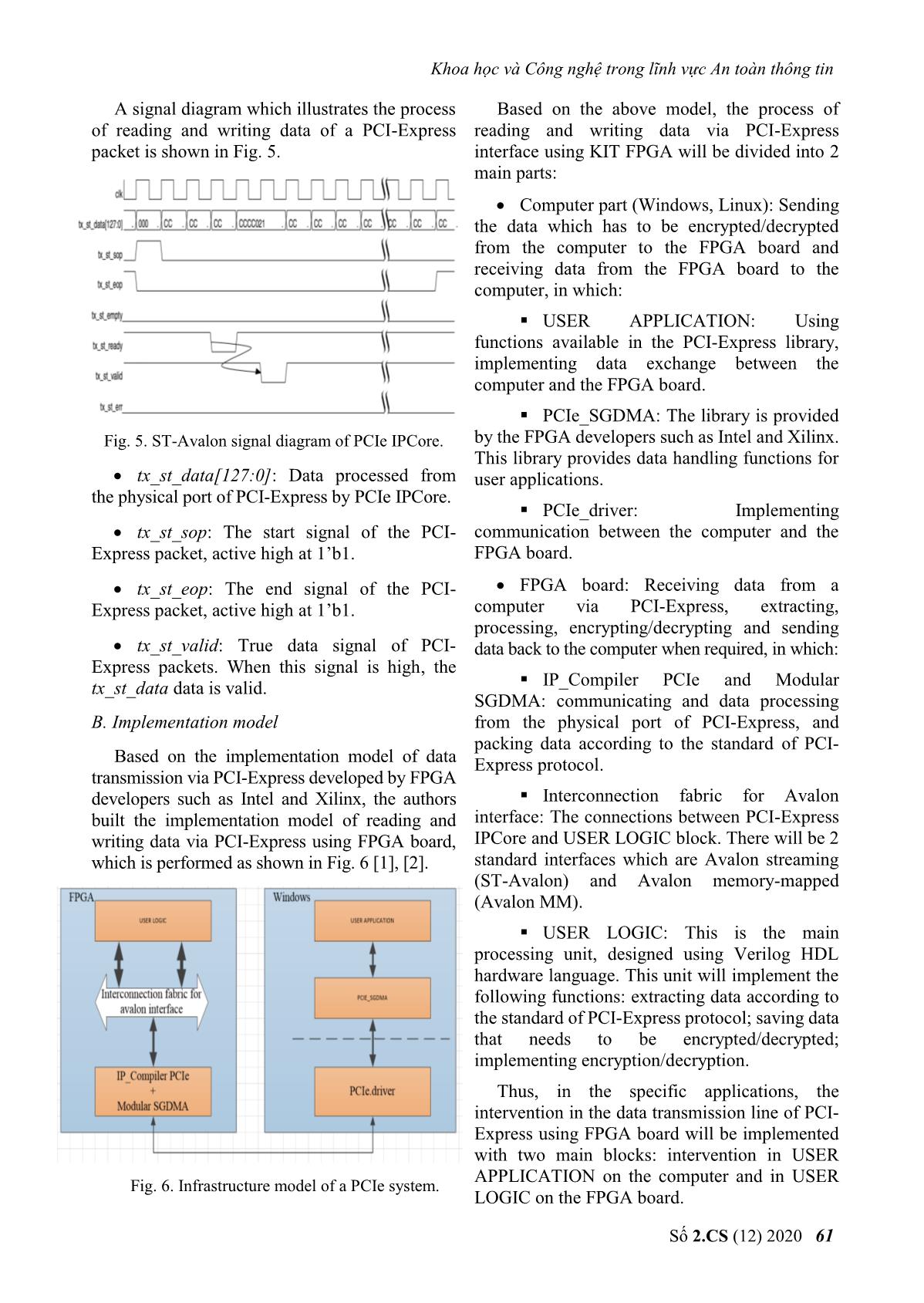
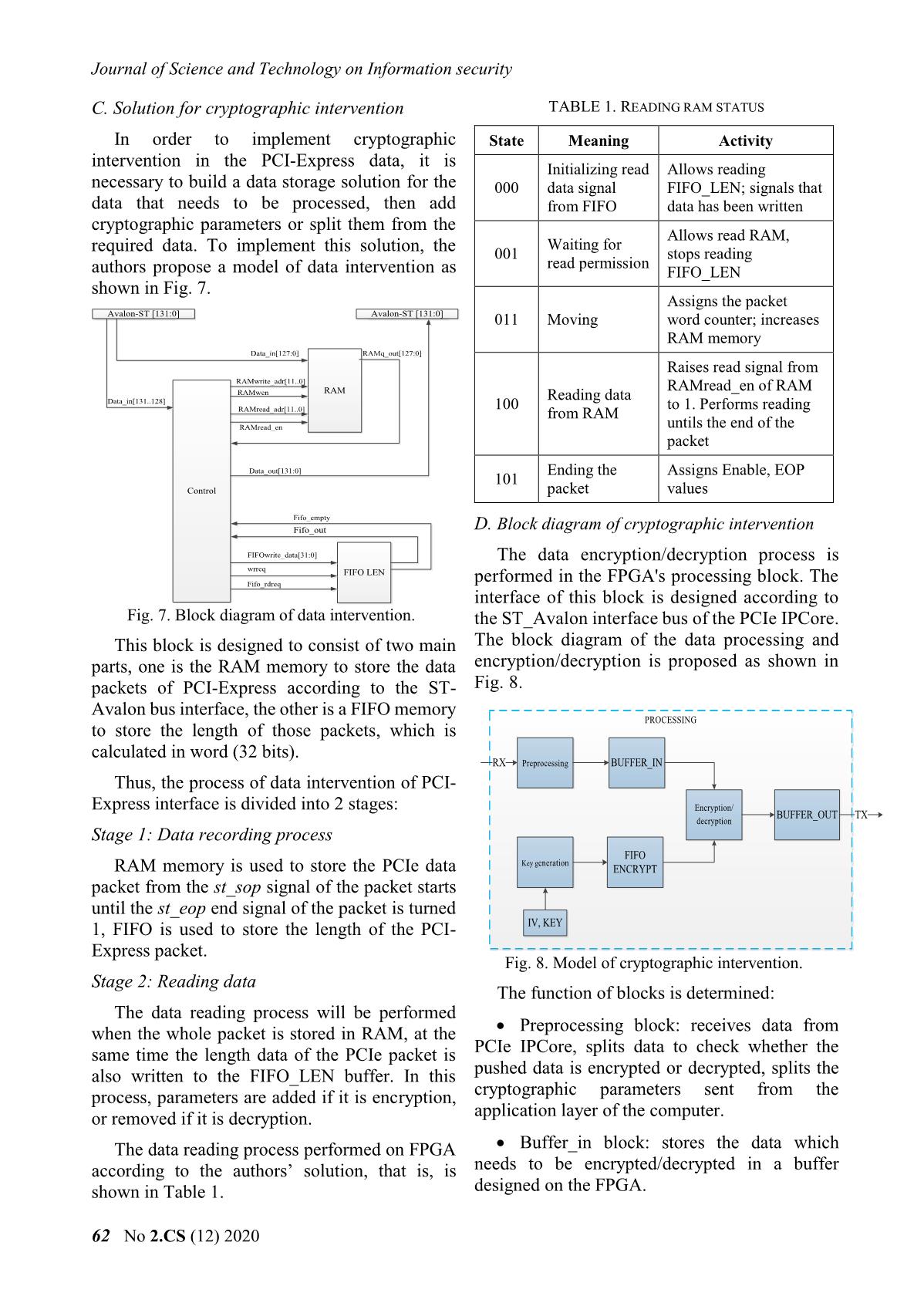
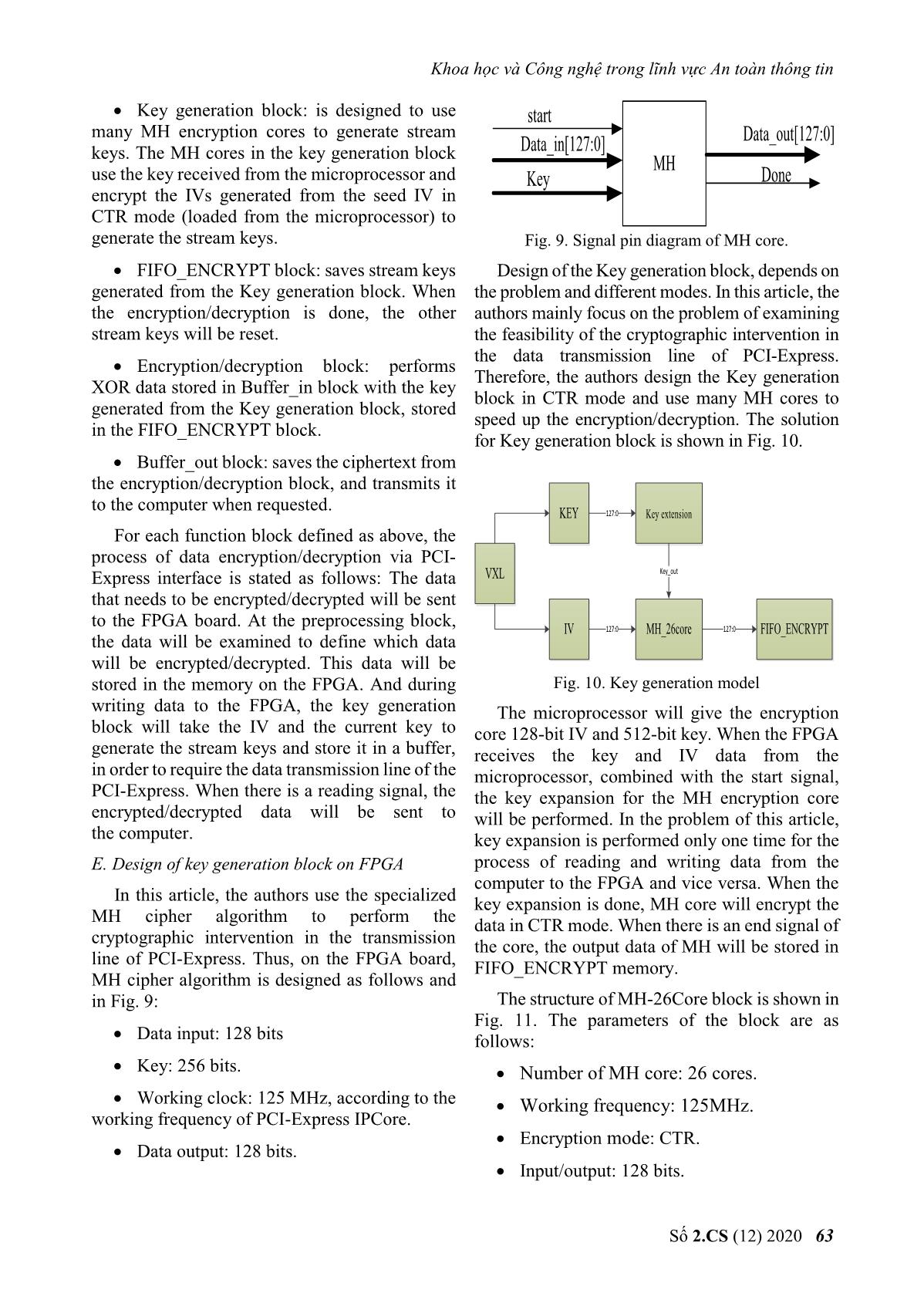
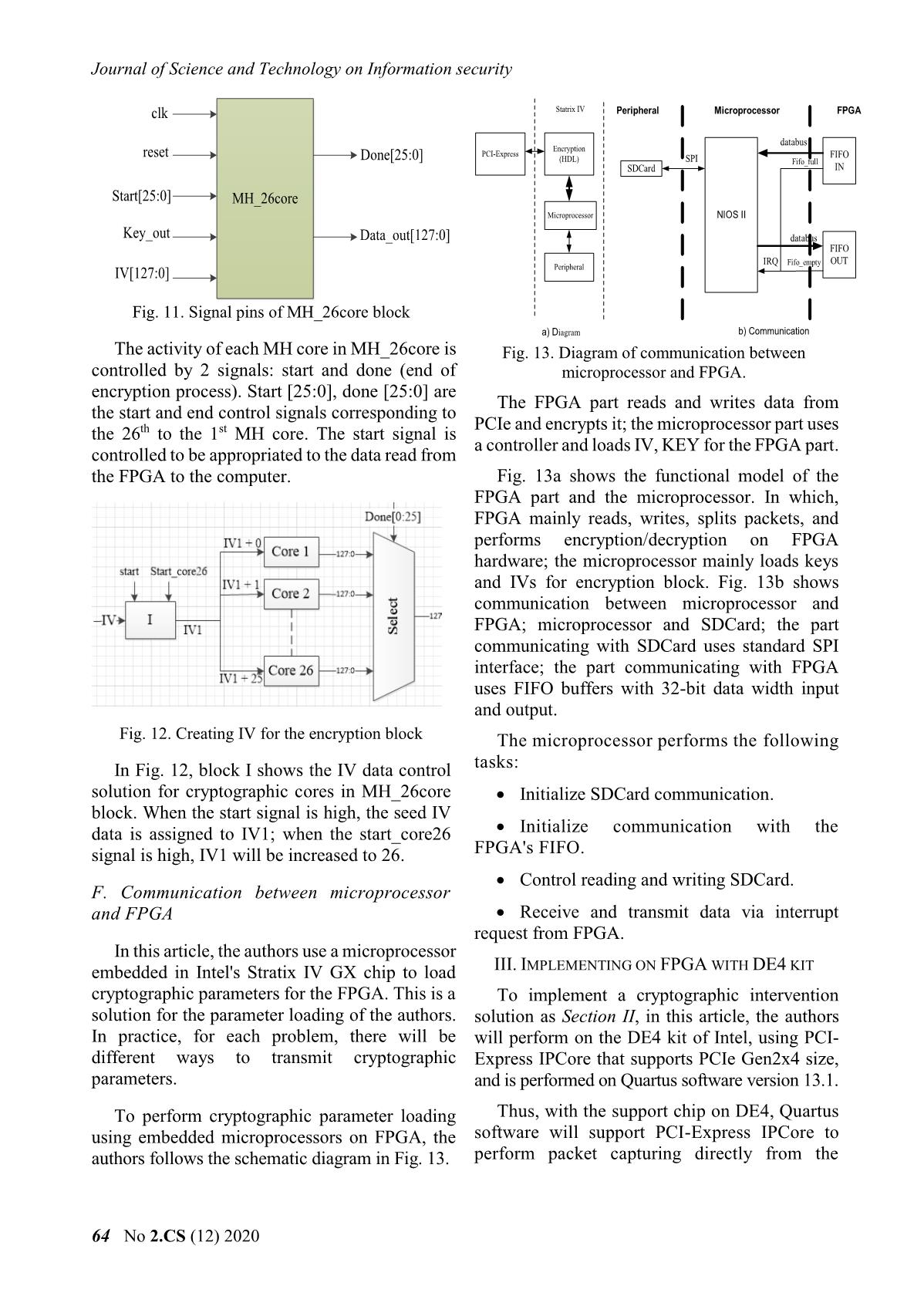
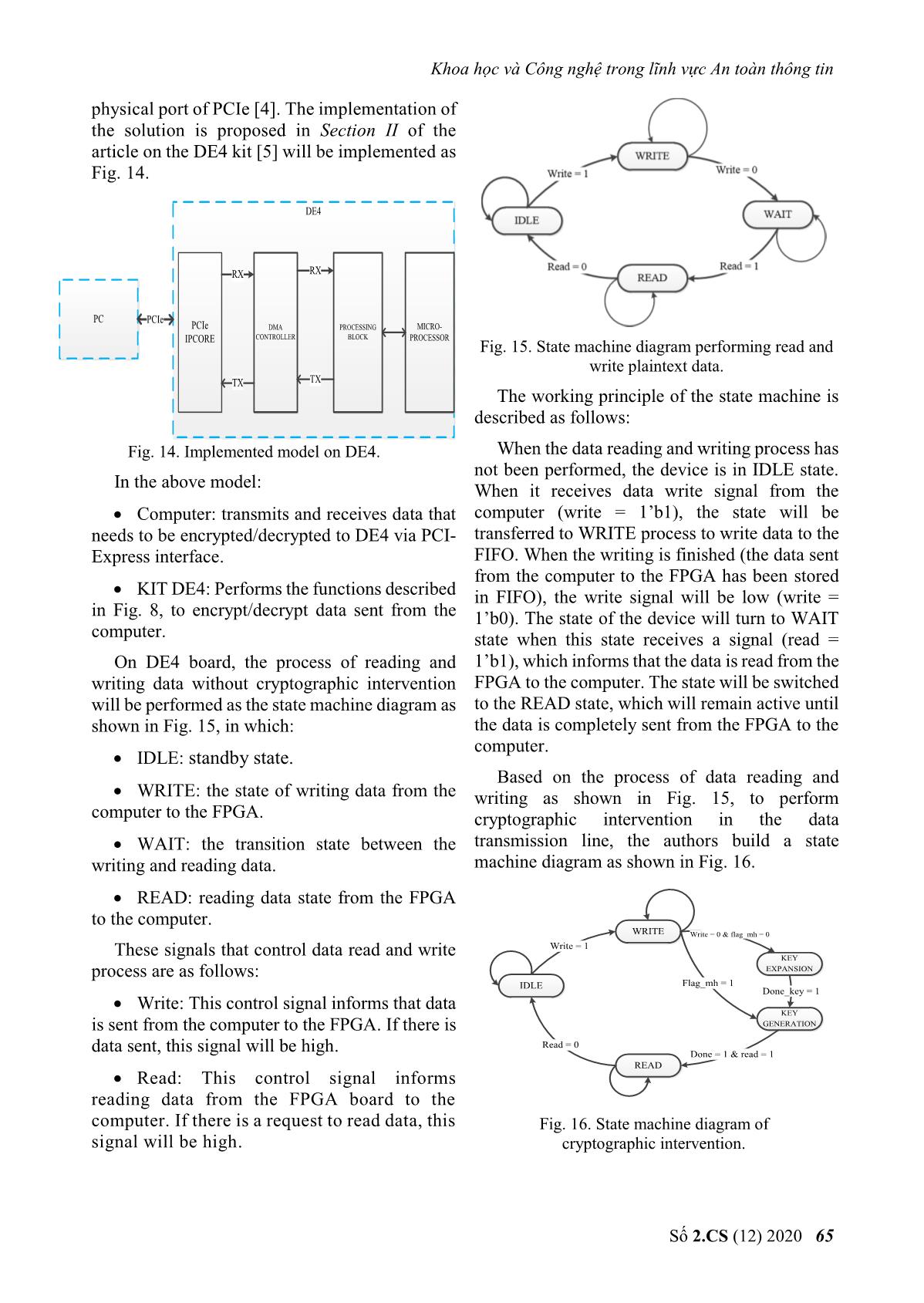
g tin Key generation block: is designed to use start many MH encryption cores to generate stream Data_in[127:0] Data_out[127:0] keys. The MH cores in the key generation block MH use the key received from the microprocessor and Key Done encrypt the IVs generated from the seed IV in CTR mode (loaded from the microprocessor) to generate the stream keys. Fig. 9. Signal pin diagram of MH core. FIFO_ENCRYPT block: saves stream keys Design of the Key generation block, depends on generated from the Key generation block. When the problem and different modes. In this article, the the encryption/decryption is done, the other authors mainly focus on the problem of examining stream keys will be reset. the feasibility of the cryptographic intervention in the data transmission line of PCI-Express. Encryption/decryption block: performs Therefore, the authors design the Key generation XOR data stored in Buffer_in block with the key block in CTR mode and use many MH cores to generated from the Key generation block, stored speed up the encryption/decryption. The solution in the FIFO_ENCRYPT block. for Key generation block is shown in Fig. 10. Buffer_out block: saves the ciphertext from the encryption/decryption block, and transmits it to the computer when requested. KEY 127:0 Key extension For each function block defined as above, the process of data encryption/decryption via PCI- Express interface is stated as follows: The data VXL Key_out that needs to be encrypted/decrypted will be sent to the FPGA board. At the preprocessing block, IV 127:0 MH_26core 127:0 FIFO_ENCRYPT the data will be examined to define which data will be encrypted/decrypted. This data will be stored in the memory on the FPGA. And during Fig. 10. Key generation model writing data to the FPGA, the key generation The microprocessor will give the encryption block will take the IV and the current key to core 128-bit IV and 512-bit key. When the FPGA generate the stream keys and store it in a buffer, receives the key and IV data from the in order to require the data transmission line of the microprocessor, combined with the start signal, PCI-Express. When there is a reading signal, the the key expansion for the MH encryption core encrypted/decrypted data will be sent to will be performed. In the problem of this article, the computer. key expansion is performed only one time for the E. Design of key generation block on FPGA process of reading and writing data from the computer to the FPGA and vice versa. When the In this article, the authors use the specialized key expansion is done, MH core will encrypt the MH cipher algorithm to perform the data in CTR mode. When there is an end signal of cryptographic intervention in the transmission the core, the output data of MH will be stored in line of PCI-Express. Thus, on the FPGA board, FIFO_ENCRYPT memory. MH cipher algorithm is designed as follows and in Fig. 9: The structure of MH-26Core block is shown in Fig. 11. The parameters of the block are as Data input: 128 bits follows: Key: 256 bits. Number of MH core: 26 cores. Working clock: 125 MHz, according to the Working frequency: 125MHz. working frequency of PCI-Express IPCore. Encryption mode: CTR. Data output: 128 bits. Input/output: 128 bits. Số 2.CS (12) 2020 63 Journal of Science and Technology on Information security clk Statrix IV Peripheral Microprocessor FPGA databus Encryption reset PCI-Express FIFO Done[25:0] (HDL) SPI Fifo_full SDCard IN Start[25:0] MH_26core Microprocessor NIOS II Key_out Data_out[127:0] databus FIFO IRQ Fifo_empty OUT IV[127:0] Peripheral Fig. 11. Signal pins of MH_26core block a) Diagram b) Communication The activity of each MH core in MH_26core is Fig. 13. Diagram of communication between controlled by 2 signals: start and done (end of microprocessor and FPGA. encryption process). Start [25:0], done [25:0] are The FPGA part reads and writes data from the start and end control signals corresponding to PCIe and encrypts it; the microprocessor part uses the 26th to the 1st MH core. The start signal is a controller and loads IV, KEY for the FPGA part. controlled to be appropriated to the data read from the FPGA to the computer. Fig. 13a shows the functional model of the FPGA part and the microprocessor. In which, FPGA mainly reads, writes, splits packets, and performs encryption/decryption on FPGA hardware; the microprocessor mainly loads keys and IVs for encryption block. Fig. 13b shows communication between microprocessor and FPGA; microprocessor and SDCard; the part communicating with SDCard uses standard SPI interface; the part communicating with FPGA uses FIFO buffers with 32-bit data width input and output. Fig. 12. Creating IV for the encryption block The microprocessor performs the following In Fig. 12, block I shows the IV data control tasks: solution for cryptographic cores in MH_26core Initialize SDCard communication. block. When the start signal is high, the seed IV data is assigned to IV1; when the start_core26 Initialize communication with the signal is high, IV1 will be increased to 26. FPGA's FIFO. Control reading and writing SDCard. F. Communication between microprocessor and FPGA Receive and transmit data via interrupt request from FPGA. In this article, the authors use a microprocessor embedded in Intel's Stratix IV GX chip to load III. IMPLEMENTING ON FPGA WITH DE4 KIT cryptographic parameters for the FPGA. This is a To implement a cryptographic intervention solution for the parameter loading of the authors. solution as Section II, in this article, the authors In practice, for each problem, there will be will perform on the DE4 kit of Intel, using PCI- different ways to transmit cryptographic Express IPCore that supports PCIe Gen2x4 size, parameters. and is performed on Quartus software version 13.1. To perform cryptographic parameter loading Thus, with the support chip on DE4, Quartus using embedded microprocessors on FPGA, the software will support PCI-Express IPCore to authors follows the schematic diagram in Fig. 13. perform packet capturing directly from the 64 No 2.CS (12) 2020 Khoa học và Công nghệ trong lĩnh vực An toàn thông tin physical port of PCIe [4]. The implementation of the solution is proposed in Section II of the article on the DE4 kit [5] will be implemented as Fig. 14. DE4 RX RX PC PCIe PCIe DMA PROCESSING MICRO- CONTROLLER BLOCK PROCESSOR IPCORE Fig. 15. State machine diagram performing read and write plaintext data. TX TX The working principle of the state machine is described as follows: Fig. 14. Implemented model on DE4. When the data reading and writing process has not been performed, the device is in IDLE state. In the above model: When it receives data write signal from the Computer: transmits and receives data that computer (write = 1’b1), the state will be needs to be encrypted/decrypted to DE4 via PCI- transferred to WRITE process to write data to the Express interface. FIFO. When the writing is finished (the data sent from the computer to the FPGA has been stored KIT DE4: Performs the functions described in FIFO), the write signal will be low (write = in Fig. 8, to encrypt/decrypt data sent from the 1’b0). The state of the device will turn to WAIT computer. state when this state receives a signal (read = On DE4 board, the process of reading and 1’b1), which informs that the data is read from the writing data without cryptographic intervention FPGA to the computer. The state will be switched will be performed as the state machine diagram as to the READ state, which will remain active until shown in Fig. 15, in which: the data is completely sent from the FPGA to the computer. IDLE: standby state. Based on the process of data reading and WRITE: the state of writing data from the writing as shown in Fig. 15, to perform computer to the FPGA. cryptographic intervention in the data WAIT: the transition state between the transmission line, the authors build a state writing and reading data. machine diagram as shown in Fig. 16. READ: reading data state from the FPGA to the computer. WRITE Write = 0 & flag_mh = 0 Write = 1 These signals that control data read and write KEY process are as follows: EXPANSION IDLE Flag_mh = 1 Done_key = 1 Write: This control signal informs that data KEY is sent from the computer to the FPGA. If there is GENERATION Read = 0 data sent, this signal will be high. Done = 1 & read = 1 READ Read: This control signal informs reading data from the FPGA board to the computer. If there is a request to read data, this Fig. 16. State machine diagram of signal will be high. cryptographic intervention. Số 2.CS (12) 2020 65 Journal of Science and Technology on Information security In addition to the states such as IDLE, WRITE, The block diagram is designed as shown in Fig. READ as in the plaintext reading and writing 8 and Fig. 14; the key generation block is designed process, the implementation of using cryptographic MH_26core block in CTR encryption/decryption has 2 other states, KEY mode. The designed resources and blocks are EXPANSION and KEY GENERATION. aggregated and shown in Fig. 17 and Fig. 18. KEY EXPANSION: the state of expanding key for MH core. KEY GENERATION: the state of pre- generating stream keys using MH_26core block. The signals that control the state machine are as follows: flag_mh: controls the key extension for the key generation block. If the encryption has performed key expansion, this signal will be high to signal. Fig. 17. Designed resources on DE4. done_key: signals that the key expansion IV. RESULTS is completed. With the solution of cryptographic done: signals that the stream key has been intervention as shown in Fig. 8 and created from the KEY GENERATION block. encryption/decryption, in this article, the authors used the MH algorithm in CTR mode to generate The working principle of the state machine stream keys. The software on the computer will will be stated as follows: send data to the FPGA board via the PCIe At the end of the write process from the interface and receive data back from the FPGA. computer to the FPGA via PCI-Express, the key To evaluate the data read and write speed, the data extension for the encryption core will be size from the software is changed. The authors performed. The key extension is controlled to performed tests with corresponding data of 1500 perform once via the flag_mh signal. If flag_mh words (4 bytes), 5000 words, 16,000 words and = 1, the KEY EXPANSION status is ignored. 32,000 words. In case of key expansion, when the done_key Test and evaluation results of the solution signal turns to 1 to indicate that key extension is implemented on computer using the core duo chip finished, the status will be changed to KEY are as follows: GENERATION. The key generation will pre- For packets of 1500 words generate 26 stream keys and store them in FIFO_ENCRYPT. After creating 26 stream keys, read signal turns to 1. The state transforms to READ to read data from the FPGA to the computer. In data read state, data from 2 FIFO which are FIFO_DATA and FIFO_ENCRYPT will be read simultaneously. Reading from FIFO_ENCRYPT will also control the MH_26core block to work. For packets of 5000 words The purpose of this process is to respond that FIFO_ENCRYPT always contains data not to interfere with the process of XOR data from FIFO_DATA with FIFO_ENCRYPT. After the reading is finished, data in FIFO_ENCYPT will be deleted, to perform a new reading and writing process with new IV data. 66 No 2.CS (12) 2020 Khoa học và Công nghệ trong lĩnh vực An toàn thông tin For packets of 16,000 words V. CONCLUSION In this article, the authors present a general solution that implements cryptographic intervention in the data transmission line via PCI- Express interface using the FPGA board. The results of the solution achieved by evaluating on the DE4 kit show that intervening in the data transmission line of the PCI-Express interface is completely feasible. For packets of 32,000 words The data transmission rate via PCI-Express depends on the size of the data. The larger the data, the higher data read and write speed via PCI- Express. REFERENCES [1] Intel, “DE4 PCIe Qsys example designs”, February 2, 2018. [2] Intel, “PCI-Express high performance reference If the encrypted data has different sizes, the design”, 2014. result of data read and write performance via PCI- Express interface is different. The larger the data, [3] PCI-SIG, “PCI Express Base Specification the higher the read and write speed. The test Revision 2.01”, March 4, 2009. results with different data sizes performed on [4] Intel, “IP Compiler for PCI Express user guide”, computer equipped with a core duo chip are August 2014. shown in Fig. 18. [5] Altera Corp (2016), “DE4 User manual”. url: 4 ftp://ftp.altera.com/up/pub/Altera_Material/Boa rds/DE4/DE4_User_Manual.pdf 3 [6] Ankita R. Tembhare, Dr.Pramod B. Patil, 2 “Design & Implementation of PCI Express BUS Gbps Physical layer using VHDL”, IRITCC July 1 2014, Vl.2 Issue 7. 0 [7] Kun Cheng, Weiyue Liu, Qi Shen, Shengkai 0 20000 40000 60000 80000 Liao, “Design and Implementation of High- word throughput PCIe with DMA Architecture between FPGA and PowerPC”, Journal of IEEE Transactions on Nuclear Science, 2018. Fig. 18. The test result of data read and write. Số 2.CS (12) 2020 67 Journal of Science and Technology on Information security ABOUT THE AUTHOR Phan Van Ky La Huu Phuc Workplace: Institute of Cryptographic Workplace: Institute of Science and Technology Cryptographic Science and Email: pvk.hvktqs@gmail.com Technology Education: Received bachelor’s degree Email: phucpvkt@hotmail.com in 2013, received master’s degree in Education: Received bachelor's degree 2017, in Saint Petersburg Electronical in 1998, master’s degree in 2002, and University. PhD in 2015 in Electronic engineering. Current research field: integrated circuit technology, FPGA. Current research field: Designing and producing security device, specialized cipher machine. Vu Ta Cuong Workplace: Institute of Cryptographic Science and Technology Email: vutacuong109@gmail.com Education: Received bachelor's degree in 2011, master's degree in 2013, and PhD in 2016, in Radio Electronics, Kharkiv Aerospace University, Ukraine. Current research field: PKI Token, cryptographic engineering. 68 No 2.CS (12) 2020
File đính kèm:
 solution_for_cryptographic_intervention_in_pci_express_data.pdf
solution_for_cryptographic_intervention_in_pci_express_data.pdf

