Performance of orthogonal frequency division multiplexing based advanced encryption standard
Currently, there are a lot of secure communication schemes have been proposed to hide
secret contents. In this work, one of the methods deploying encryption to cipher data is
represented. The primary object of this project is applying Advanced Encryption Standard (AES)
in communications based Orthogonal Frequency Division Multiplexing (OFDM). This article
discusses the security of the method encrypting directly QAM symbols instead of input bit-stream.
This leads to improving the security of transmitting data by utilization of authentication key
between the mobile and base station. The archived results demonstrate that the performance of the
AES-OFDM system is completely acceptable to compare with the criteria for 4G.
Keywords: Orthogonal Frequency Division Multiplexing (OFDM), Advanced Encryption Standard
(AES), Quadrature Amplitude Modulation (QAM), Authentication Key, Cellular Network,
Encryption, Physical Layer, 4G, LTE.

Trang 1

Trang 2

Trang 3
Trang 4

Trang 5

Trang 6
Trang 7

Trang 8
Tóm tắt nội dung tài liệu: Performance of orthogonal frequency division multiplexing based advanced encryption standard

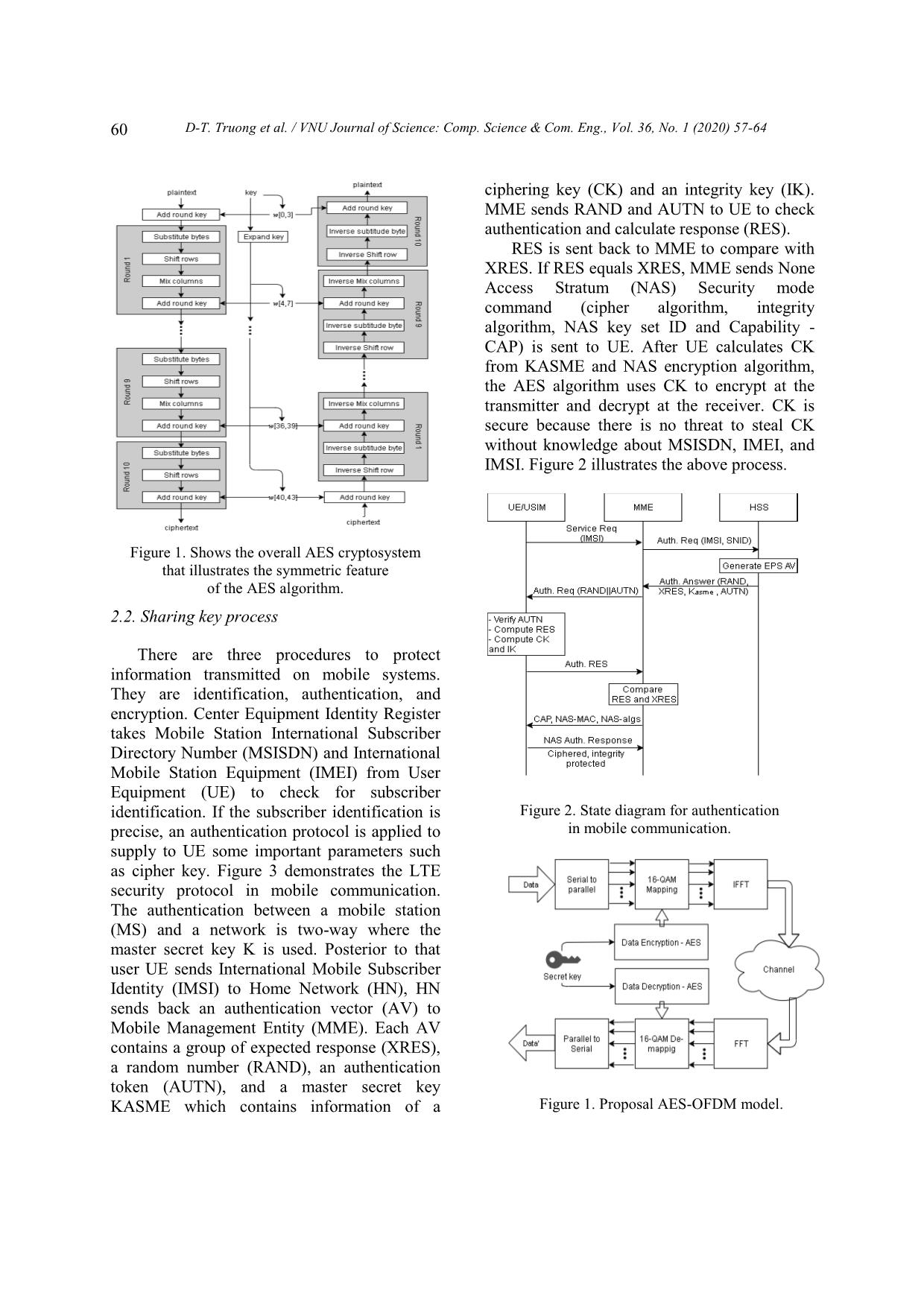
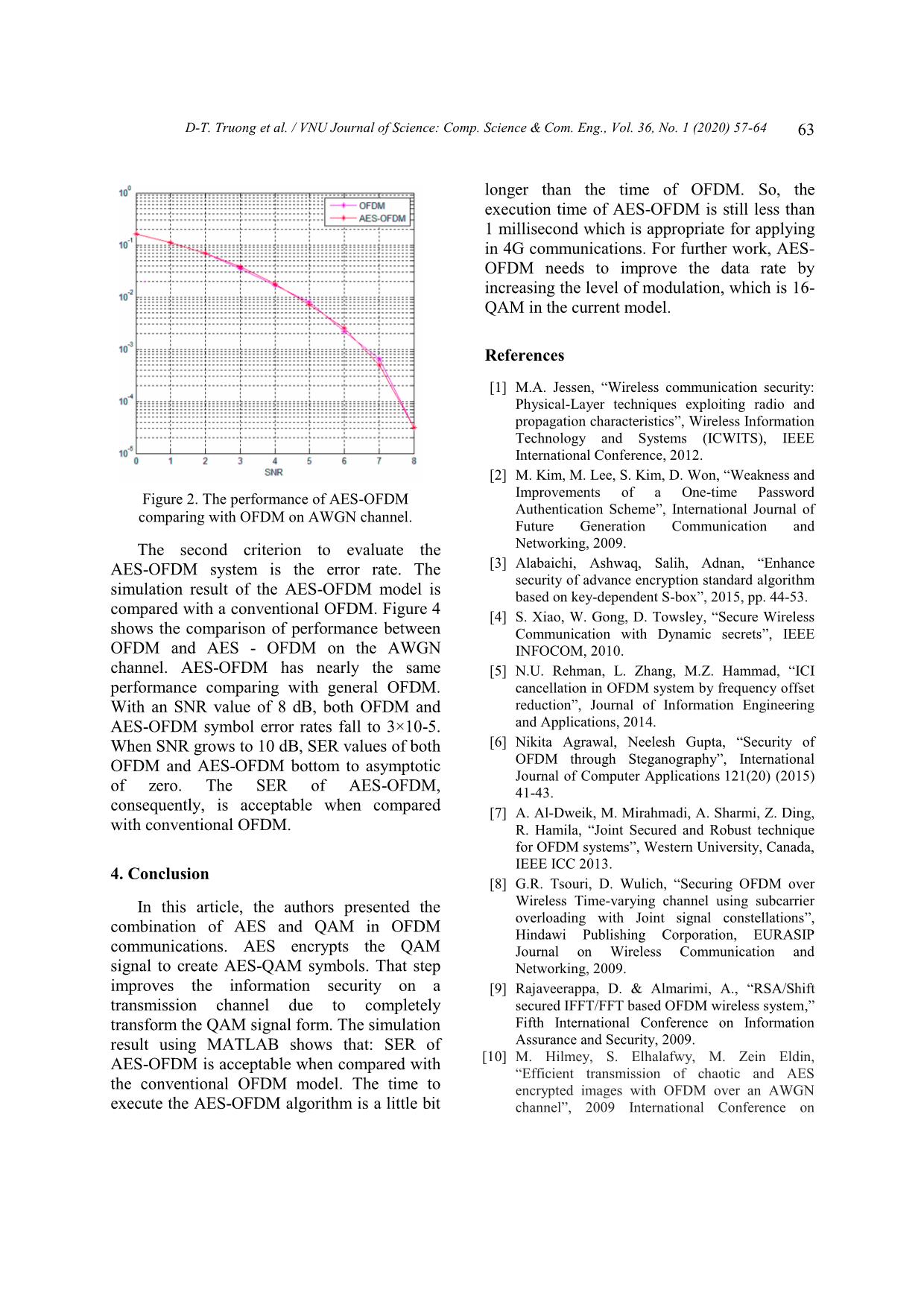
ection will be the discussion of previous work, while the third In the whole of this work, AES-128 is section would like to explain how AES-OFDM chosen to implement. system work and its diagram. The fourth Step 3: There are four functions section analyzes simulation results and assesses implemented sequentially except for the last the security and performance of the round. The general AES algorithm is AES-OFDM model. The conclusion will be determined as following pseudo-code: given in the final section. Algorithm 1. Pseudo-algorithm at transmitter 2. Proposed method 1 Begin 2 Add round key with current state 2.1. Advanced encryption standard algorithm 3 Expand key; 4 For i = 1 to 9 do AES is an algorithm adopted by the 5 Hexadecimal numbers. U.S government and widely used to protect data 6 Substitution of state using S-box; [15]. AES cipher block of 128-bit or 16-byte 7 Shift left each word in round data symmetrically. The basic unit in AES is a Mix Columns state using 8 byte. XOR operation effectuates the addition of arithmetic over GF(28) two bytes. The multiplication of two bytes in Add round key [i] with current AES is a multiplication in GF(28) which has state by XOR. an irreducible polynomial 9 End 843 m xxxxx 1. The secret key of Substitution of state by S-box AES has three types of length which are 16, 24 Shift left each word in round Add round key [10] with current and 32 bytes (128, 192 and 256 bits). AES-128, AES-192, AES-256 is three algorithms state by XOR corresponding to the length of the cipher key. 10 End 60 D-T. Truong et al. / VNU Journal of Science: Comp. Science & Com. Eng., Vol. 36, No. 1 (2020) 57-64 ciphering key (CK) and an integrity key (IK). MME sends RAND and AUTN to UE to check authentication and calculate response (RES). RES is sent back to MME to compare with XRES. If RES equals XRES, MME sends None Access Stratum (NAS) Security mode command (cipher algorithm, integrity algorithm, NAS key set ID and Capability - CAP) is sent to UE. After UE calculates CK from KASME and NAS encryption algorithm, the AES algorithm uses CK to encrypt at the transmitter and decrypt at the receiver. CK is secure because there is no threat to steal CK without knowledge about MSISDN, IMEI, and IMSI. Figure 2 illustrates the above process. Figure 1. Shows the overall AES cryptosystem that illustrates the symmetric feature of the AES algorithm. 2.2. Sharing key process There are three procedures to protect information transmitted on mobile systems. They are identification, authentication, and encryption. Center Equipment Identity Register takes Mobile Station International Subscriber Directory Number (MSISDN) and International Mobile Station Equipment (IMEI) from User Equipment (UE) to check for subscriber identification. If the subscriber identification is Figure 2. State diagram for authentication precise, an authentication protocol is applied to in mobile communication. supply to UE some important parameters such as cipher key. Figure 3 demonstrates the LTE security protocol in mobile communication. The authentication between a mobile station (MS) and a network is two-way where the master secret key K is used. Posterior to that user UE sends International Mobile Subscriber Identity (IMSI) to Home Network (HN), HN sends back an authentication vector (AV) to Mobile Management Entity (MME). Each AV contains a group of expected response (XRES), a random number (RAND), an authentication token (AUTN), and a master secret key KASME which contains information of a Figure 1. Proposal AES-OFDM model. D-T. Truong et al. / VNU Journal of Science: Comp. Science & Com. Eng., Vol. 36, No. 1 (2020) 57-64 61 2.3. AES-OFDM model For instance, a sub-stream bbbb has M bits. Those bits To secure transmit data at the physical llllM 12 are constellation mapped. If 16-QAM is layer, this article proposes a combination of applied, the number of elements each substream AES and OFDM, so-called AES-OFDM. The having now is 32: main idea is encoding QAM symbols directly in the OFDM classical model. Figure 2 illustrates the proposed AES-OFDM model. The process stsssllll 1232 of the proposed system is mostly the same as the original OFDM model except for the The elements are encrypted by AES to constellation mapping step where the AES become completely new symbols. algorithm is embedded. After converting from serial to parallel, each sub-channel contains 128 '''' sl t s l1 s l 2 s l 32 bits, thus 1000 sub-channels constitute 128000 bits. The data transmission rate is the same at Table 2. QAM states and corresponding all individual channels because of orthogonality hexadecimal number and the same bandwidth. AES algorithm Carrier Carrier Hexadecimal operates with a byte as the data unit which is Input represented as a couple of hexadecimal phase amplitude mapping o numbers. Consequently, 16-QAM modulation 0000 225 0.33 0 o is appropriate to cooperate with the AES 0001 255 0.75 1 o algorithm due to that a byte can convey two 16- 0010 195 0.75 3 o QAM states also. This way not only improves 0011 225 1.0 2 o the security of pure OFDM but also makes the 0100 135 0.33 4 o attacker hard to decrypt the information. The 0101 105 0.75 5 o reason is that the encryption is performed with 0110 165 0.75 7 o 16-QAM symbols while the normal security 0111 135 1.0 6 o methods apply AES on the bit-stream. Thus, the 1000 315 0.33 C o attempt of attacker to decrypt the bit-stream or 1001 285 0.75 D o to decrypt at the application layer will fail. In 1010 345 0.75 F o detail, the mapping of 16-QAM states and 1011 315 1.0 E o hexadecimal numbers are shown in Table 2. 1100 45 0.33 8 After the encryption process, the ciphertext 1101 75o 0.75 9 will be remapping to QAM again and perform 1110 15o 0.75 B similar steps as the traditional OFDM model. 1111 45o 1.0 A Whole system operation can be represented by mathematical as follow: Therefore, the transmitted data will be Firstly, the original data is paralleled by N totally different from the original data. This substreams which contain 128 bits each as step ensures the transmission security. After that, IFFT is used to divide signals b11 b 12 b 1128 b b b into several frequency stacks. The final shown: 21 22 2128 transmitted AES-OFDM is given as below: b b b N NNN1 2 128 N 128 ' m ts tf t cos 2 l l 0 62 D-T. Truong et al. / VNU Journal of Science: Comp. Science & Com. Eng., Vol. 36, No. 1 (2020) 57-64 Pseudo-algorithm at the transmitter is Execute time is an important parameter to considered as follow: consider a system being available or not with a temporary technology. The required Algorithm 2. Pseudo-algorithm at transmitter transmission time interval in a 4G system must 1 Begin below 1 millisecond. In the journal of Schneier 2 For each frame do et al. [16], AES - Rijndael encryption and 3 Modulated Data = 16-QAM decryption setup take respectively 300 and modulation of original data; 1370 clock cycles on 32-bit CPUs. On the other 4 Plain text = mapping 16-QAM hand, each OFDM symbol needs 7142 clocks modulated symbols to hexadecimal numbers. cycles to be processed entirely [17]. Definitely, 5 Ciphered text = implement AES total required clocks for AES-OFDM with plaintext and key; processing is maximum at around 23600 cycles 6 Ciphered symbols = Remapping that takes 9.83 microseconds on 2.4 GHz CPUs. ciphertext to 16-QAM symbols; That executive time is much less than the 7 IFFT ciphered symbols; required transmission time interval in 4G. Thus, 8 Add cyclic prefix; 9 End the proposed AES-OFDM system can be 10 End possible to deal with 4G technology. At the receiver, symmetric blocks are used to demodulate sent signals. Due to the effect of 3. Simulation result the channel, the received message differs from the transmitted signal. Thus, received symbols In this section, simulation results focus on is fluctuated with fixed values in table 1, so it two criteria, security, and error rate of AES- requires a balancing method in blocks of AES OFDM. The scenario is there will be 32000 16- decryption. By applying boundaries, every QAM symbols randomly created to transmit by symbol is assigned to a fixed value in Table 2. AES-OFDM. The simulation results are This approach improves the symbol error rate investigated on the AWGN channel. which is mentioned in the next section. The To determine the security of AES-OFDM, pseudo algorithm at the receiver is shown the 16-QAM symbols before and after AES are as below: observed. It is notable that there is no clue to Algorithm 3. Pseudo-algorithm at receiver detect the key when the attackers have both original and encrypted symbols without 1 Begin knowledge of the cipher algorithm. In a random 2 For each frame do 3 Remove cyclic prefix; test case as an instance, there are three symbols 4 FFT received symbols; represented as 3.0000 + 1.0000i in thirty-two 5 Estimate received symbols to 16 original symbols. However, the three values of 16-QAM; corresponding symbols after applying AES are 6 Ciphertext = Mapping received totally nonrelative, -1.0000 - 1.0000i -3.0000 symbols to hexadecimal numbers + 3.0000i -1.0000 + 3.0000i. Therefore the 7 Plaintext = AES decryption of ciphertext and key security of the OFDM signal is ensured. 8 Modulated Symbols = Remapping However, the security in this work relies on the plaintext to 16-QAM symbols secret key mostly. If the key is not reveal, the 9 Output data = demodulate attacker cannot decrypt the encrypted signals. modulated symbols Since the secret key is generated randomly, the 10 End protection of the AES-OFDM is certain. 11 End D-T. Truong et al. / VNU Journal of Science: Comp. Science & Com. Eng., Vol. 36, No. 1 (2020) 57-64 63 longer than the time of OFDM. So, the execution time of AES-OFDM is still less than 1 millisecond which is appropriate for applying in 4G communications. For further work, AES- OFDM needs to improve the data rate by increasing the level of modulation, which is 16- QAM in the current model. References [1] M.A. Jessen, “Wireless communication security: Physical-Layer techniques exploiting radio and propagation characteristics”, Wireless Information Technology and Systems (ICWITS), IEEE International Conference, 2012. [2] M. Kim, M. Lee, S. Kim, D. Won, “Weakness and Figure 2. The performance of AES-OFDM Improvements of a One-time Password Authentication Scheme”, International Journal of comparing with OFDM on AWGN channel. Future Generation Communication and The second criterion to evaluate the Networking, 2009. AES-OFDM system is the error rate. The [3] Alabaichi, Ashwaq, Salih, Adnan, “Enhance security of advance encryption standard algorithm simulation result of the AES-OFDM model is based on key-dependent S-box”, 2015, pp. 44-53. compared with a conventional OFDM. Figure 4 [4] S. Xiao, W. Gong, D. Towsley, “Secure Wireless shows the comparison of performance between Communication with Dynamic secrets”, IEEE OFDM and AES - OFDM on the AWGN INFOCOM, 2010. channel. AES-OFDM has nearly the same [5] N.U. Rehman, L. Zhang, M.Z. Hammad, “ICI performance comparing with general OFDM. cancellation in OFDM system by frequency offset With an SNR value of 8 dB, both OFDM and reduction”, Journal of Information Engineering AES-OFDM symbol error rates fall to 3×10-5. and Applications, 2014. When SNR grows to 10 dB, SER values of both [6] Nikita Agrawal, Neelesh Gupta, “Security of OFDM and AES-OFDM bottom to asymptotic OFDM through Steganography”, International Journal of Computer Applications 121(20) (2015) of zero. The SER of AES-OFDM, 41-43. consequently, is acceptable when compared [7] A. Al-Dweik, M. Mirahmadi, A. Sharmi, Z. Ding, with conventional OFDM. R. Hamila, “Joint Secured and Robust technique for OFDM systems”, Western University, Canada, IEEE ICC 2013. 4. Conclusion [8] G.R. Tsouri, D. Wulich, “Securing OFDM over In this article, the authors presented the Wireless Time-varying channel using subcarrier overloading with Joint signal constellations”, combination of AES and QAM in OFDM Hindawi Publishing Corporation, EURASIP communications. AES encrypts the QAM Journal on Wireless Communication and signal to create AES-QAM symbols. That step Networking, 2009. improves the information security on a [9] Rajaveerappa, D. & Almarimi, A., “RSA/Shift transmission channel due to completely secured IFFT/FFT based OFDM wireless system,” transform the QAM signal form. The simulation Fifth International Conference on Information result using MATLAB shows that: SER of Assurance and Security, 2009. AES-OFDM is acceptable when compared with [10] M. Hilmey, S. Elhalafwy, M. Zein Eldin, “Efficient transmission of chaotic and AES the conventional OFDM model. The time to encrypted images with OFDM over an AWGN execute the AES-OFDM algorithm is a little bit channel”, 2009 International Conference on 64 D-T. Truong et al. / VNU Journal of Science: Comp. Science & Com. Eng., Vol. 36, No. 1 (2020) 57-64 Computer Engineering & Systems, Cairo, 2009, [14] Y. Liang, J. Ren, T. Li, “Secure OFDM System pp. 353-358. Design and Capacity Analysis Under Disguised [11] B.V. Naik, N.L.K. Sai, C.M. Kumar, “Efficient Jamming”, in IEEE Transactions on Information transmission of encrypted images with OFDM Forensics and Security 15 (2020) 738-752. system”, 2017 IEEE International Conference on [15] Westlund, B. Harold, “NIST reports measurable Power, Control, Signals and Instrumentation success of Advanced Encryption Engineering (ICPCSI), Chennai, 2017, Standard”, Journal of Research of the National pp. 2383-2388. Institute of Standards and Technology, 2002. [12] S.M.S. Eldin, “Optimized OFDM Transmission of [16] B. Schneier, J. Kelsey, D. Whiting, D. Wagner, C. Encrypted Image Over Fading Channel”, An Hall, N. Ferguson, Performance Comparison of International Journal on Sensing and Imaging the AES Submissions, Proceedings of the Second 15(1) (2014), pp. 1-14. AES Candidate Conference, 1999. [13] C. Akbar, H. Mahmood, Q. Minhas, I. Mustafa, [17] S. He, A. Tang, H. Zhang, “A high-performance “Secure AES OFDM with channel reciprocity Implementation of OFDM-MIMO base-band in exploitation through relative calibration”, 2016 wireless video system”, Information Technology International Conference on Open Source Systems & Journal 13 (2014), pp. 1678-1685. Technologies (ICOSST), Lahore, 2016, pp. 54-61. H h
File đính kèm:
 performance_of_orthogonal_frequency_division_multiplexing_ba.pdf
performance_of_orthogonal_frequency_division_multiplexing_ba.pdf

