Information leakage through electromagnetic radiation of ps/2 keyboard
Bàn phím máy tính thường được sử
dụng để nhập dữ liệu đầu vào cho một hệ thống
máy tính, các dữ liệu có thể là văn bản thông
thường hoặc thông tin cần được bảo mật như mật
khẩu hay khóa. Bàn phím sử dụng các linh kiện
điện tử, vì thế chúng sẽ gây ra bức xạ điện từ dẫn
đến lộ lọt các thông tin khi gõ phím. Bài báo này
trình bày về việc thu các tín hiệu bức xạ điện từ
phát ra từ bàn phím PS/2 khi gõ phím qua các con
đường khác nhau (nhiễu bức xạ trong không gian,
nhiễu dẫn trên đường nguồn, qua mạng LAN). Từ
đó, nghiên cứu xây dựng một module chương trình
trên MATLAB để khôi phục lại tín hiệu gõ phím từ
các dữ liệu thu được trong trường gần của bàn
phím. Kết quả của cách tấn công trên kênh kề này
là khôi phục trung bình được hơn 70% ký tự được
gõ trong trường gần của bàn phím PS/2. Trường
hợp tốt nhất kết quả có thể lên đến hơn 90% ký tự
được gõ. Từ kết quả nghiên cứu trên, nhóm nghiên
cứu rút ra kết luận, các loại bàn phím1
1 This manuscript is received June 14, 2019. It is
commented on June 17, 2019 and is accepted on June 24,
2019 by the first reviewer. It is commented on June 16, 2019
and is accepted on June 25, 2019 by the second reviewer.
PS/2 đều phát ra các bức xạ điện từ gây mất mát
thông tin và không an toàn để sử dụng khi nhập các
thông tin cần được bảo mật.

Trang 1

Trang 2

Trang 3
Trang 4

Trang 5
Trang 6

Trang 7
Trang 8

Trang 9

Trang 10
Tóm tắt nội dung tài liệu: Information leakage through electromagnetic radiation of ps/2 keyboard

. But even when a collision
signal depends on the scancode of pressed key, occurs, the falling edge technique also limited
so it is possible to accurately identify 11 falling the set of possible pressed key. For example, if
a password includes 8 letters, the number of
edges with equal spacing of the Clock signal 8 37
and the falling edge of Data signal in the possible passwords is 26 ~ 2 . With the falling
obtained signal (Fig.5). edge technique, the biggest number of possible
passwords is 68 ~ 220 when the letters in the
password belong to a group of 6 letters ("b",
"d", "h", "j", "m", "x"), but in reality, this case
rarely happens. Thus, the average result is only
about 210, much lower than the 237.
B. Keystroke signal recovery program for
electromagnetic radiation of keyboard
Based on the falling edge technique mentioned
above and analysed characteristics of scancode
Fig.5. Data signal, Clock signal and radiated signal of PS/2 such as the first bit is bit 0 (start), the last bit is bit 1
keyboard when key E is pressed [8] (stop), bit 1 always has a larger amplitude than the
bit 0... we built a program on MATLAB to recover
When key E is pressed in Fig.5, we can
the keystroke signal from obtained electromagnetic
clearly distinguish 11 falling edges of the Clock
radiations of the PS/2 keyboard with the block
signal and 3 falling edges of the Data signal.
diagram of the acquisition and recovery process is
Assuming the definition of falling edge trace as
shown in Fig.6.
“2” when there are radiated peaks of Data and
No 2.CS (10) 2019 55
Journal of Science and Technology on Information security
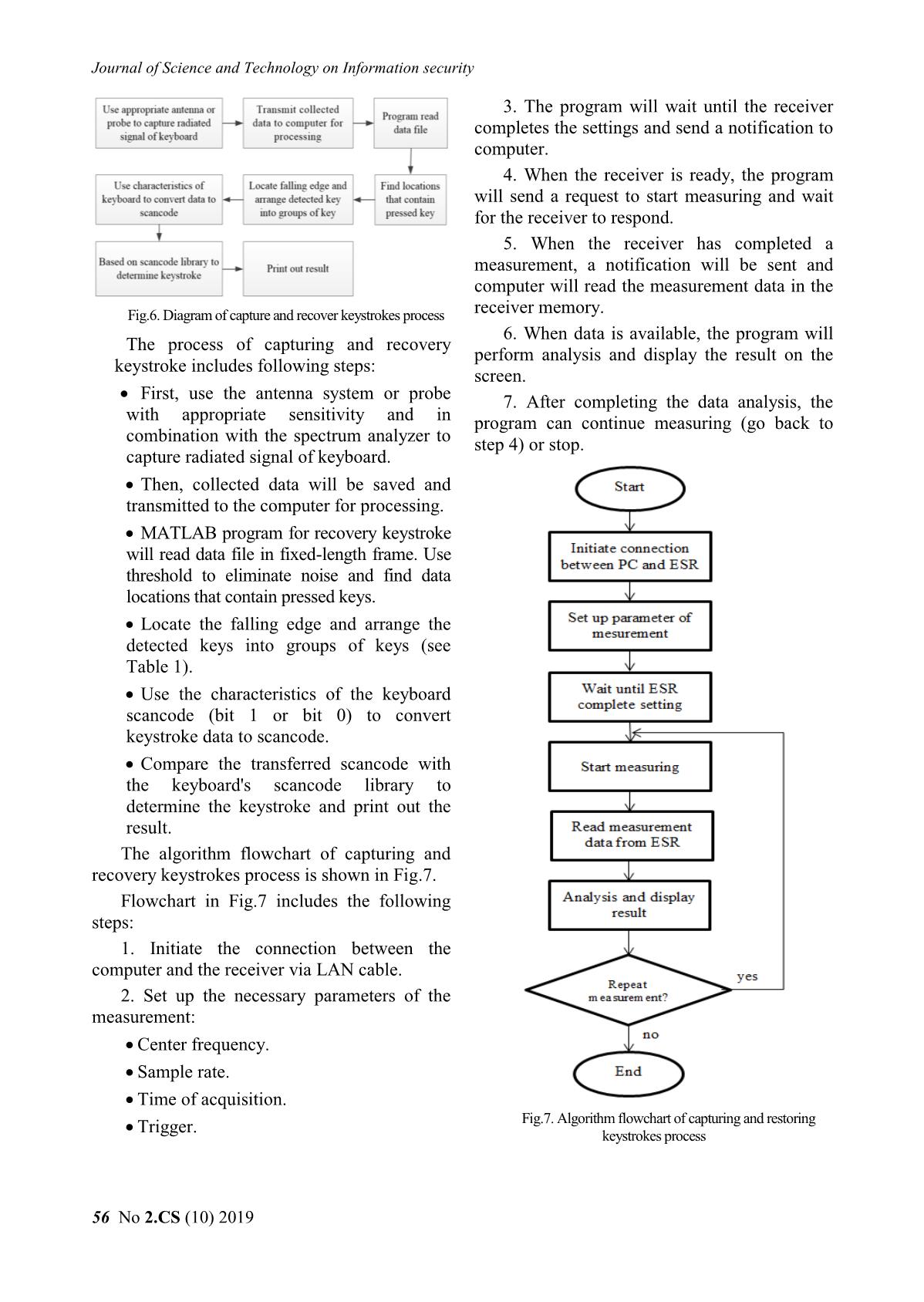
3. The program will wait until the receiver
completes the settings and send a notification to
computer.
4. When the receiver is ready, the program
will send a request to start measuring and wait
for the receiver to respond.
5. When the receiver has completed a
measurement, a notification will be sent and
computer will read the measurement data in the
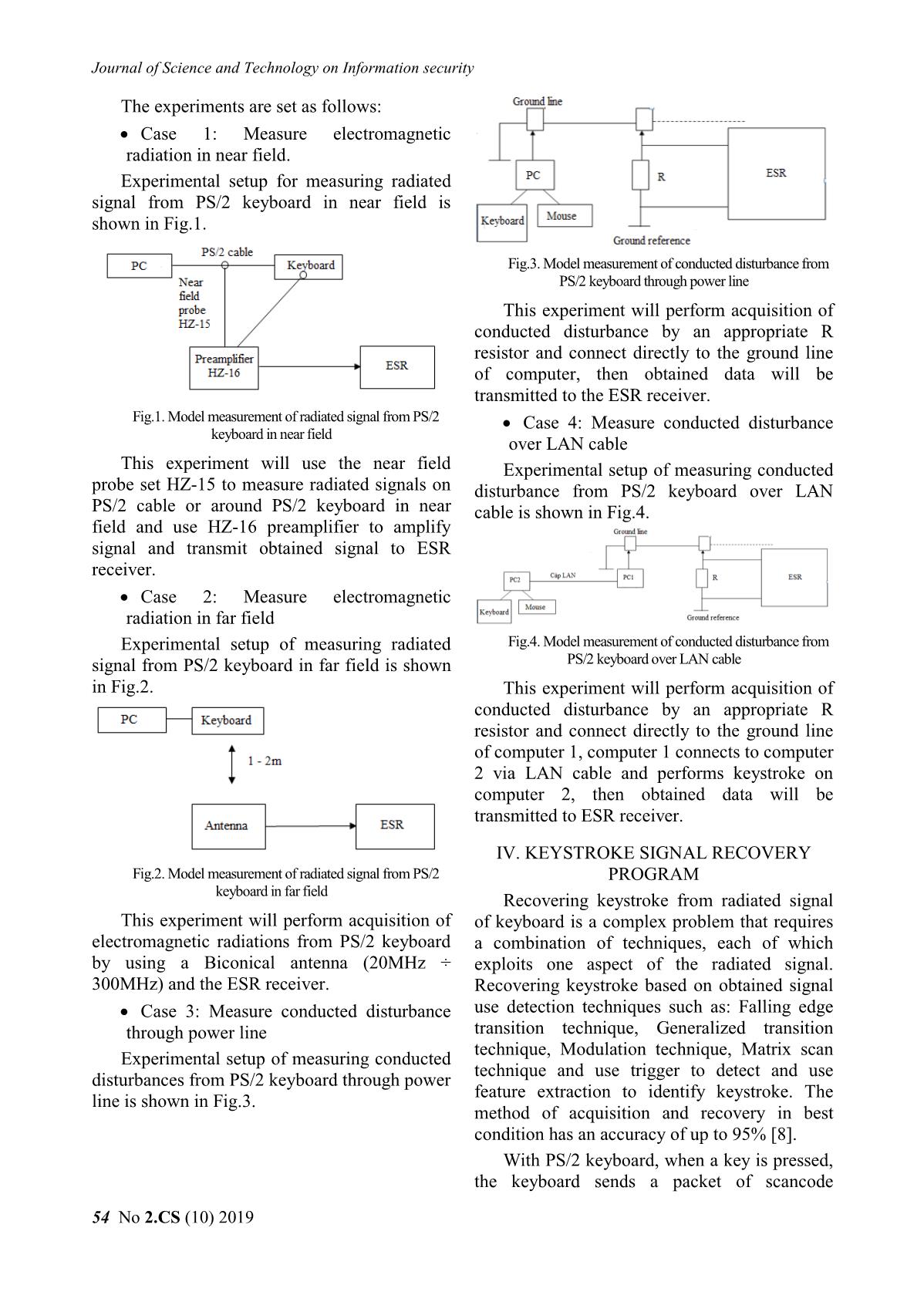
Fig.6. Diagram of capture and recover keystrokes process receiver memory.
6. When data is available, the program will
The process of capturing and recovery
perform analysis and display the result on the
keystroke includes following steps:
screen.
First, use the antenna system or probe 7. After completing the data analysis, the
with appropriate sensitivity and in program can continue measuring (go back to
combination with the spectrum analyzer to step 4) or stop.
capture radiated signal of keyboard.
Then, collected data will be saved and
transmitted to the computer for processing.
MATLAB program for recovery keystroke
will read data file in fixed-length frame. Use
threshold to eliminate noise and find data
locations that contain pressed keys.
Locate the falling edge and arrange the
detected keys into groups of keys (see
Table 1).
Use the characteristics of the keyboard
scancode (bit 1 or bit 0) to convert
keystroke data to scancode.
Compare the transferred scancode with
the keyboard's scancode library to
determine the keystroke and print out the
result.
The algorithm flowchart of capturing and
recovery keystrokes process is shown in Fig.7.
Flowchart in Fig.7 includes the following
steps:
1. Initiate the connection between the
computer and the receiver via LAN cable.
2. Set up the necessary parameters of the
measurement:
Center frequency.
Sample rate.
Time of acquisition.
Fig.7. Algorithm flowchart of capturing and restoring
Trigger. keystrokes process
56 No 2.CS (10) 2019
Nghiên cứu Khoa học và Công nghệ trong lĩnh vực An toàn thông tin
Note that the time of acquisition or the
number of samples collected per frame must be
large enough to contain all pulses of a
keystroke. In order to minimize the amount of
redundant data collected, the collection method
only focuses on data frames that contain
keystroke by using trigger. In principle, the
clock is always high when there is no data
transmitted between the keyboard and the
computer, so the first clock pulse is always
changing the state from 1 to 0, which means
appearing a falling edge. Based on the above
rule, the program selects trigger so that
receiver starts from the first clock pulse of
keystroke pulse sequence.
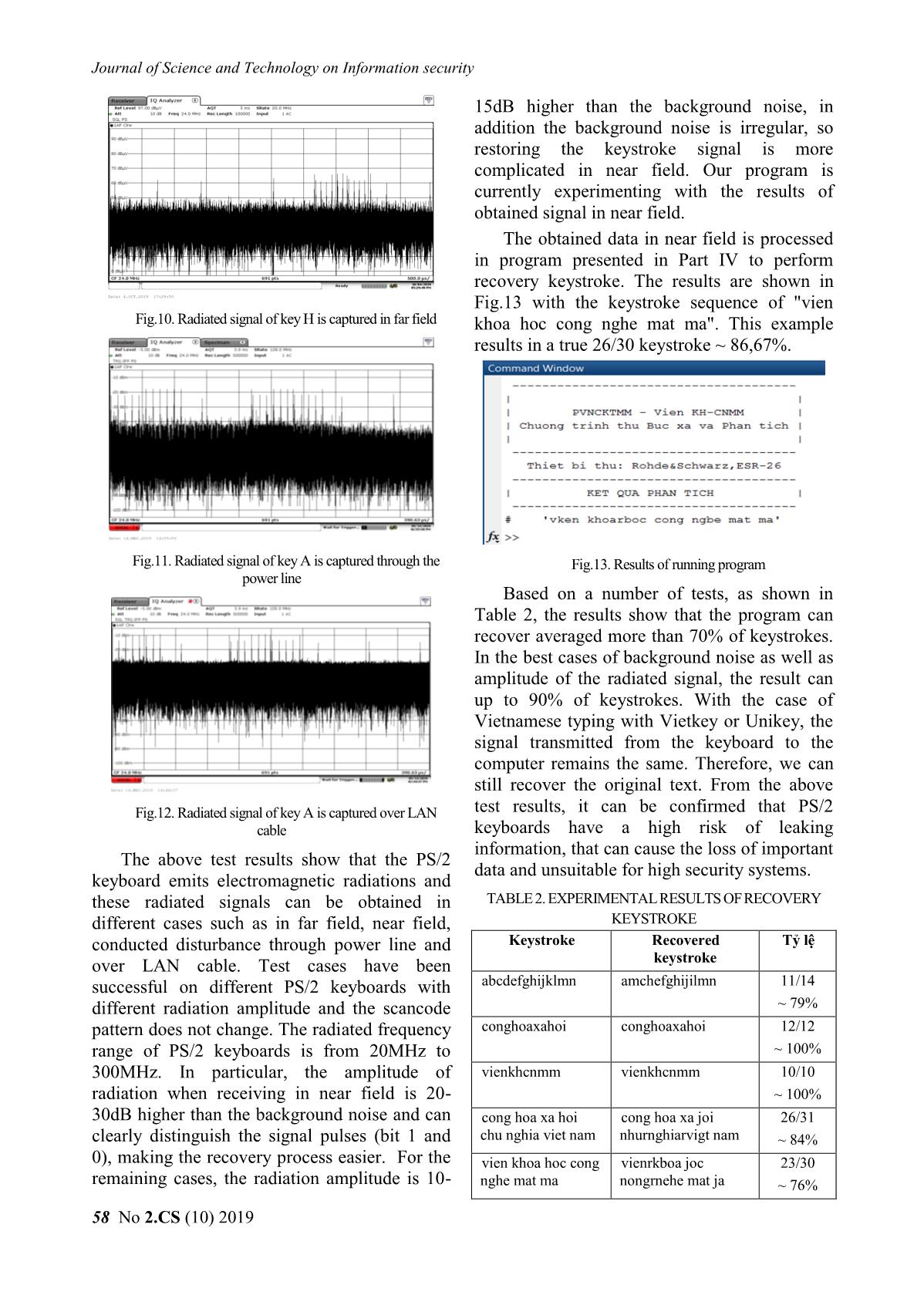
The algorithm flowchart of analyzing
obtained data process in Fig.8.
Flowchart in Fig.8 includes the following
steps:
Step 1. From receiver memory, the
program checks to see if there is enough data
for analysis. If not, exit program or else,
analysis will be executed.
Step 2. From the data block, read out N
data samples. N is defined so that it can
contain no more than 1 pulse of clock.
Step 3. Find falling edge in those N data
samples (radiated impulse detection). If not,
go back to step 1 and read the next N data
samples, if there is a falling edge then go to Fig.8. Algorithm flowchart of analyzing radiatied signal
step 4. process
Step 4. When appearing a falling edge, the V. EXPERIMENTAL RESULTS
program will read the next N1 samples, N1 The experiments capture radiated signal as
will include the entire data of a keystroke. described in Part III with 4 different cases. The
N1 is determined based on the keyboard’s results are shown in Fig.9 to Fig.12.
clock frequency and the receiver sample rate.
Step 5. Find the remaining falling edges
positions in the N1 samples.
Step 6. Based on the searching results for
the position of falling edges, divide the
keystroke into the key group according to
Table 1 for falling edge traces.
Step 7. Based on the characteristics of the
keyboard scancode to recover scancode of
the keystroke.
Step 8. Compare the scancode results Fig.9. Radiated signal of key A is captured in near field
with the scancode library and display the
results on the screen. Then go back to Step 1.
No 2.CS (10) 2019 57
Journal of Science and Technology on Information security
15dB higher than the background noise, in
addition the background noise is irregular, so
restoring the keystroke signal is more
complicated in near field. Our program is
currently experimenting with the results of
obtained signal in near field.
The obtained data in near field is processed
in program presented in Part IV to perform
recovery keystroke. The results are shown in
Fig.13 with the keystroke sequence of "vien
Fig.10. Radiated signal of key H is captured in far field khoa hoc cong nghe mat ma". This example
results in a true 26/30 keystroke ~ 86,67%.
Fig.11. Radiated signal of key A is captured through the Fig.13. Results of running program
power line
Based on a number of tests, as shown in
Table 2, the results show that the program can
recover averaged more than 70% of keystrokes.
In the best cases of background noise as well as
amplitude of the radiated signal, the result can
up to 90% of keystrokes. With the case of
Vietnamese typing with Vietkey or Unikey, the
signal transmitted from the keyboard to the
computer remains the same. Therefore, we can
still recover the original text. From the above
Fig.12. Radiated signal of key A is captured over LAN test results, it can be confirmed that PS/2
cable keyboards have a high risk of leaking
information, that can cause the loss of important
The above test results show that the PS/2
data and unsuitable for high security systems.
keyboard emits electromagnetic radiations and
these radiated signals can be obtained in TABLE 2. EXPERIMENTAL RESULTS OF RECOVERY
different cases such as in far field, near field, KEYSTROKE
conducted disturbance through power line and Keystroke Recovered Tỷ lệ
over LAN cable. Test cases have been keystroke
successful on different PS/2 keyboards with abcdefghijklmn amchefghijilmn 11/14
different radiation amplitude and the scancode ~ 79%
pattern does not change. The radiated frequency conghoaxahoi conghoaxahoi 12/12
range of PS/2 keyboards is from 20MHz to ~ 100%
300MHz. In particular, the amplitude of vienkhcnmm vienkhcnmm 10/10
radiation when receiving in near field is 20- ~ 100%
30dB higher than the background noise and can cong hoa xa hoi cong hoa xa joi 26/31
clearly distinguish the signal pulses (bit 1 and chu nghia viet nam nhurnghiarvigt nam ~ 84%
0), making the recovery process easier. For the vien khoa hoc cong vienrkboa joc 23/30
remaining cases, the radiation amplitude is 10- nghe mat ma nongrnehe mat ja ~ 76%
58 No 2.CS (10) 2019
Nghiên cứu Khoa học và Công nghệ trong lĩnh vực An toàn thông tin
hello good morning hgllo gooh morning 16/18 ACKNOWLEDGMENT
~ 89% This work was supported by Institute of
bùi đức chính buif jhuwcs nhinbs 14/18 Cryptographic Science and Technology,
~78% Viet Nam.
demo thu ban phim dgmo thu ban phim 22/23 REFERENCES
co day co day ~ 96% [1]. Andrea Barisan Daniele Bianco, “Side Channel
Attacks Using Optical Sampling of Mechanical
Energy and Power Line Leakage”, Copyright
Future studies are being carried out by us Inverse Path Ltd, 2009.
regarding restoring other cases of PS/2 [2]. Asonov, D., and Agrawal, R., “Keyboard Acoustic
keyboards, such as eliminating the increase of Emanations”, In IEEE Symposium on Security
noise and amplifying the radiated signals. In and Privacy, 2004.
addition, we are also studying methods of [3]. Blzarotti, D., Cova, M., and Vigna, G., “Clearshot:
capturing radiated signals of other keyboards Eavesdropping on keyboard input from video”, In
such as USB keyboard, wireless keyboard and IEEE Symposium on Security and Privacy, 2008.
Laptop keyboard. This requires improving the [4]. Kuhn, M. G., “Compromising Emanations:
Eavesdropping risks of Computer Displays”,
acquisition process by using preamplifiers as Technical Report, 2003.
well as testing in environments with low [5]. John V. Monaco, “SoK: Keylogging Side
background noise such as semi-anechoic Channels”, IEEE Symposium on Security and
chamber. The initial results of these studies are Privacy, 2018.
relatively positive, but the results are not [6]. Lizhuang, Fengzhou, J. D. Tygar, “Keyboard
comprehensive so we do not present in this Acoustic Emanations Revisited”, In Proceedings
th
article. of the 12 ACM Conference on Computer and
Communications Security, November 2005.
VI. CONCLUSION [7]. Loughry, J., and Umphress, D. A., “Information
The keyboard is an input component of a leakage from optical emanations”, ACM Trans.
Inf. Syst. Secur, 2002.
computer system, so if it is attacked, security of
[8]. Martin Vuagnoux, Sylvain Pasini, “Compromising
the system becomes insignificant. This article Electromagnetic Emanations of Wired and
has proven the risk of information leakage Wireless Keyboards”, Security and Cryptography
through electromagnetic radiations of PS/2 Laboratory, 2007-2009.
keyboard. The article also presented the [9]. Smulders, P., “The Threat of Information Theft by
successful acquisition of electromagnetic Reception of Electromagnetic Radiation from RS-
radiations from PS/2 keyboard with cases of 232 Cables”, Computers and Security, 1990.
electromagnetic radiation in near field, far field [10]. Tuttlebee, W., “Software Defined Radio: Enabling
and conducted disturbance through the power Technologies”, John Wiley and Sons, England,
2003.
line and over LAN cable. Result of the [11]. Tzipora Halevi, Nitesh Saxena, “Keyboard
keystroke recovery program can achieve an acoustic side channel attacks: exploring realistic
average of 70% of the keystrokes and up to and security-sensitive scenarios”, International
more than 90% of keystrokes in the best case. Journal of Information Security, Springer, 2014.
With PS/2 keyboard, it is difficult to improve [12]. Van Eck, W., “Electronagmetic radiation from
the hardware to avoid attacks as when video Display Units: An eavesdropping risk?”,
improving the errors of software or operating Comput. Secur, 198.
system with patches. Therefore, for a high
security computer system, keyboards with lower
electromagnetic radiation leakage should be
used and tested before being use in practice as
well as applying some techniques to reduce
electromagnetic radiation, such as using filters,
shielding or generate noise.
No 2.CS (10) 2019 59
Journal of Science and Technology on Information security
ABOUT THE AUTHOR Ngoc Vinh Hao Nguyen
M.Sc. Duc Chinh Bui Workplace: Institute of
Workplace: Institute of Cryptographic Science and
Cryptographic Science and Technology, Vietnam Government
Technology, Vietnam Government Information Security Commission.
Information Security Commission. Email: nnvh89@gmail.com
Email: ducchinh1108@gmail.com Education: Received the Degree of
Education: Received the Degree of Engineer and Master in Aerospace
Engineer in Electronics and Radio-Electronic System from
Telecommunication Engineering in Karkov Aviation University, Ukraine, in 2013 and
2013 and the Degree of Master of Enginerring in 2015 respectively.
Electronics Engineering in 2016 from the School of Research today: Field of electromagnetic compatibility.
Electronics and Telecommunications, Hanoi University Currently, he is working on cryptography analysis
of Science and Technology, Vietnam. through side channels.
Research today: Field of electromagnetic compatibility,
include solutions to ensure EMC for electronic devices
and exploit information leakage through side channels.
M.Sc. Manh Tuan Pham
Workplace: 129 Company Limited,
M.Sc. The Minh Ngo Vietnam Government Information
Workplace: Institute of Cryptographic Security Commission.
Science and Technology, Vietnam Email: tuanpm.129@gmail.com
Government Information Security
Education: Received the Degree of
Commission.
Engineer from Posts and
Email: ntminh1963@yahoo.com Telecommunications Institute of
Education: Received the Degree of Technology, Vietnam, in 2003.
Engineer from Faculty of Electrical Engineering and Received the Degree of Master from Military Technical
Informatics, Budapest University of Technology and Academy, Vietnam, in 2008. Received the Degree of
Economics, Hungary, in 1987. Received the Degree of Doctor of Physolophy from Posts and
Master of Engineering from Academy of Cryptography Telecommunications Institute of Technology, Vietnam,
Techniques, Vietnam, in 2005. in 2017.
Research today: Field of electromagnetic compatibility, Research today: design and implement cryptographic
include solutions to ensure EMC for electronic devices algorithms on hardware; overall study of security
and research about EMC standards. solutions for voice and video data on different media
environments.
60 No 2.CS (10) 2019
File đính kèm:
 information_leakage_through_electromagnetic_radiation_of_ps2.pdf
information_leakage_through_electromagnetic_radiation_of_ps2.pdf

