Decode - and - forward vs. amplify - andforward scheme in physical layer security for wireless relay beamforming networks
Việc bảo mật truyền thông vô tuyến
từ nơi gửi đến nơi nhận thường sử dụng các
thuật toán mật mã để mã hoá dữ liệu tại các tầng
phía trên trong mô hình phân lớp. Một xu hướng
khác đang được quan tâm rộng rãi là bảo mật
tầng vật lý dựa trên kỹ thuật truyền tin
beamforming và kỹ thuật tương tác fading kênh
chủ động. Xu hướng này hiện đang được thu hút
cả trong giới công nghiệp và nghiên cứu. Đóng
góp của bài báo này là làm rõ khả năng bảo mật
tầng vật lý và so sách chúng với phương pháp
bảo mật dùng kỹ thuật mật mã truyền thống. Bài
báo cũng so sánh hai kỹ thuật chuyển tiếp được
sử dụng chính trong bảo mật tầng vật lý cho
mạng vô tuyến chuyển tiếp là Amplify-andForward và Decode-and-Forward.

Trang 1

Trang 2
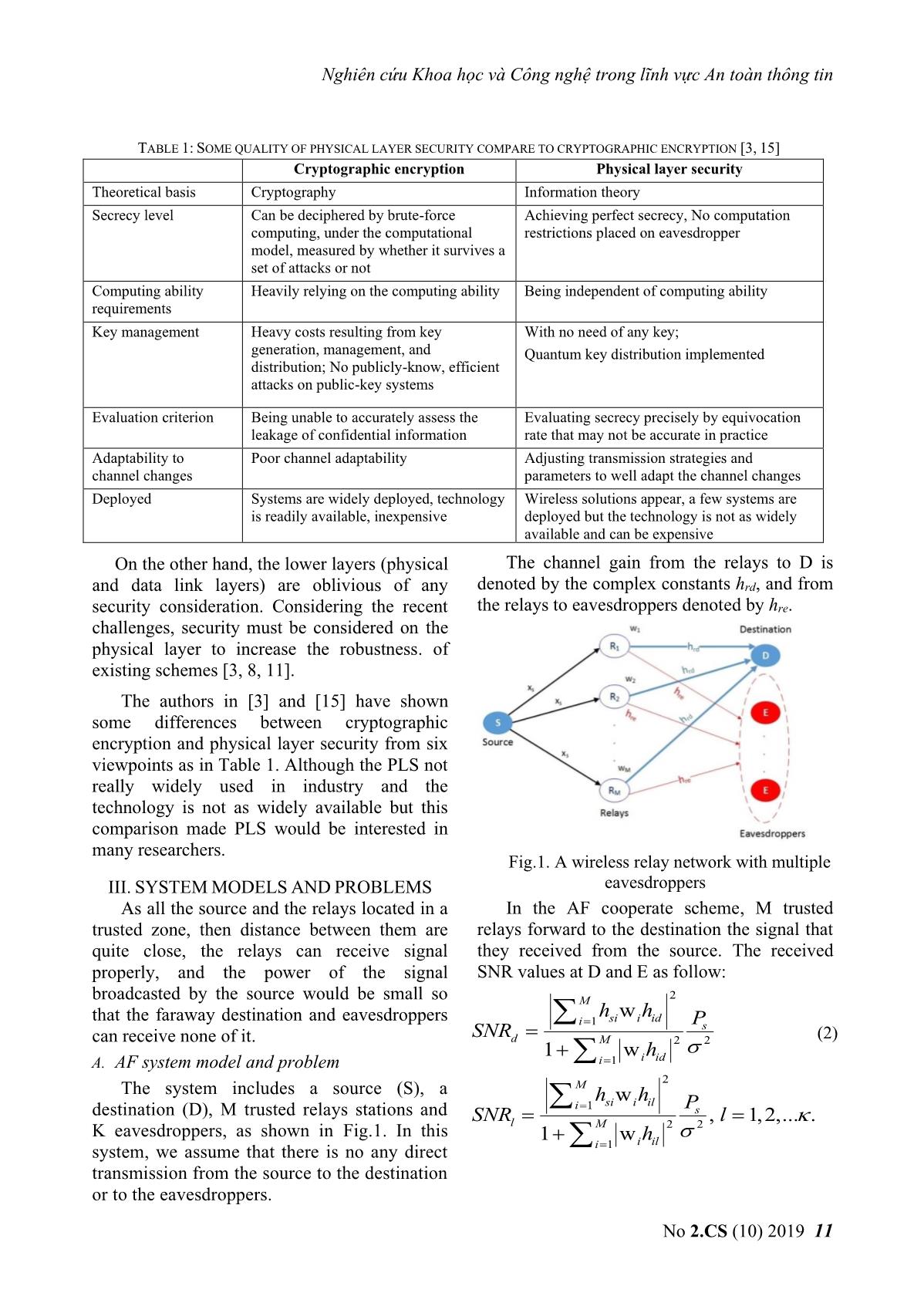
Trang 3

Trang 4

Trang 5

Trang 6
Trang 7
Trang 8

Trang 9
Tóm tắt nội dung tài liệu: Decode - and - forward vs. amplify - andforward scheme in physical layer security for wireless relay beamforming networks
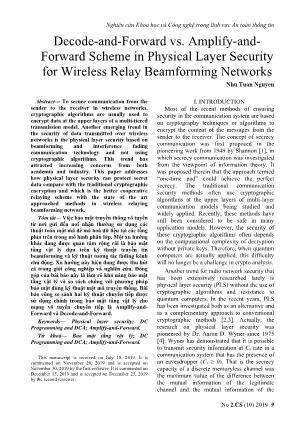
in general. x,t t (9)
Recalled that the problem (6) has form of s.., txT B x t − 2 j K
Quadratically Constrained Quadratic Program j
xxT Pt, 0.
(QCQP) with nonconvex objective function and R
nonconvex constraints. It is difficult to find the
global optimal solution of that problem by Where:
solving directly in general. The existing method
Re(R) − Im( R) Re( w)
proposed in [18] is to find suboptimal solution Z ==rd rd , x
by Semi-definite Relaxation (SDR) method as
Im(Rrd) Re( R rd ) Im( w)
following. T
† Re(RRre,, j )− Im( rej )
By defined U = uu and considering B = .
j ImR Re R
relaxation on rank one symmetric positive ( re,, j) ( re j )
semi-definite (PSD) constraint (rank(U) = 1),
the optimization program (6) can be written as The problem (9) is actually a general DC
program at the objective function and first K
†
푡 푒(풉푠풉푠 ∗ 푼)
푼 constrains [19], then we proposed DCA-AFME
(7) scheme by applied DCA to solve this problem
푠. 푡. 푡 푒(푪 ∗ 푼) ≤ 1, ∈ 휅 as the following.
푡 푒(푫푖 ∗ 푼) ≤ 1, 푖 ∈
As the objective function and all constraints
in (7) are convex, this problem can be solved
by CVX optimization tool. Once problem (7) is
solved, we can find the corresponding optimal
u and thereby w by applying eigenvalue
decompression on matrix U.
2) DC programming and DCA Solution
In [16], we proposed to apply DC
programming and DCA to solve the problem
(6). By define
2
+ 1 − |𝜌푖, | , 푖 |𝜌푖, | ≤ 1
𝜌 = {
0, 푒푙푠푒
2
− |𝜌푖, | − 1, 푖 |𝜌푖, | ≥ 1
𝜌 = {
0, 푒푙푠푒
No 2.CS (10) 2019 13
Journal of Science and Technology on Information Security
DCA-AFME SCHEME By used the equality power constrain
†
Input: Channel coefficients from source to 푤 푤 = 푃푅 instead of inequality power
constrain as
relays hs, from relays to destination hd and from
relays to eavesdroppers Hil, the predefined max 퐰′퐇 퐰
퐰†퐰=푃
threshold . 푅
(12)
0 s.t. 퐰′퐡 퐰 = 0 .
Initialization. Chose a random initial point x , 푒푗 퐾×1
l=0
l The optimization problem (12) has the
Repeat: l = l+1, calculate x by solve this optimal solution given by
subproblem:
푡−1 † √푃푅
푖푛 − (푯푠풙 ) 풙 + 휏푡 풘 = (퐈 − 퐏 )퐡 ,
풙,푡 푒
‖(퐈 − 퐏 푒)퐡 ‖
푠. 푡. 풙†푪+풙 − 2(푪−풙푙−1)†풙⟨풙 −
−1
푙−1 − 푙−1 푙−1 † − 푙−1 † †
풙 , 2(푪 풙 )⟩풙 ≤ 1 + (풙 ) 푪 풙 + where 퐏 푒 = 퐇 푒(퐇 푒퐇 푒) 퐇 푒 is the
푙−1 † − 푙−1 ,
2((풙 ) 푪 풙 ) + 푡, ∀ ∈ 휅 orthogonal projection matrix onto the subspace
풙†푫 풙 ≤ 1, ∀푖 ∈ , 푡 ≥ 0
푖 spanned by the columns of 푯 .
Until: 풓풆
‖풙푙−풙푙−1‖ | (풙푙)− (풙푙−1)| 3) DC programming and DCA approach
≤ 휀 or ≤ 휀
1+‖풙푙−1‖ 1+| (풙푙−1)| In [18], we proposed a DC decomposition
푙 푙 † 푙
where (풙 ) = (풙 ) 푯푠풙 by recall problem (5) with the total power
l l constrain as
Output: Rs = h(t , x ), SNRe, SNRe (2).
2 †
𝜎 + 풘 푯 풘
B. The approaches for DF problem
풘 (𝜎2 + 풘†푯 풘)
Null steering 푗=1..퐾 푒,푗 (13)
The authors in [9] focus on the case of Null †
푠. 푡 풘 풘 ≤ 푃푅
steering beamforming. In which, the signal is
completely nulled out at all eavesdroppers, then equivalent to
the problem (5) addition constraints 𝜎2 + 풘†푯 풘
퐰′퐡 푒 퐰 = 0퐾×1 푖푛 −
푗 풘,풕 푡 (14)
†
and rewrite as s.t. 풘 풘 ≤ 푃푅, 푡 > 0,
2
2 2 †
𝜎 + |∑ =1 ℎ , 푤 | 𝜎 + 풘 푯 풘 ≤ 푡, ∀푗 ∈ 퐾.
max (log ( )) 푒,푗
풘 𝜎2
Change to real variables form we have an
(10)
† equivalent problem as
s.t. 퐰 퐰 ≤ 푃푅
𝜎2 + 풙 풁풙
퐰′퐡 퐰 = 0 . 푖푛 0 −
푒푗 퐾×1 풙,푡 푡
(15)
2
Then can be rewritten as 푠. 푡. 풙 푗풙 ≤ 푡 − 𝜎 , ∀푗 ∈ 퐾
max 퐰′퐇 퐰
풘 풙 풙 ≤ 푃푅, 푡 ≥ 0
† (11)
s.t. 퐰 퐰 ≤ 푃푅 where
푅푒(푯 ) − (푯 ) 푅푒(풘)
퐰′퐡 푒푗 퐰 = 0퐾×1. 풁 = [ ] , = [ ]
(푯 ) 푅푒(푯 ) (풘)
Where 푅푒( 푯 푒,푗) − ( 푯 푒,푗)
= [ ] .
푗
퐇 = 퐡′ 퐡 and 퐡 = [ℎr ,1, , ℎ , ] (푯 푒,푗) 푅푒(푯 푒,푗)
14 No 2.CS (10) 2019
Nghiên cứu Khoa học và Công nghệ trong lĩnh vực An toàn thông tin
The problem (15) is restated as a standard station to the relay station and from the relay
DC program, then we can apply DCA stations to the destination one and to the
algorithm to have DCA-DFME scheme eavesdroppers with the given configuration
following: parameters as above mentioned. These datasets
are shared for all four methods.
The DCA-DFME scheme [18]:
B. Experimental results
Input: The channel coefficient matrix Bj, Z
Initialization: the random initial points x0, t0>0 With the assumption of one-way
communication system model (considering
and set l=0, 풖0 = (푡0, 풙0)
only the direction from source station S to
푙 푙 푙
Repeat: l=l+1, to calculate 풖 = (푡 , 풙 ) by receiver D without the opposite direction) as
solving the following subproblem: illustrated in Fig.2 with the given parameters.
푖푛 0 − ⟨ 푙−1, 풖⟩ For each case, 100 independent tests were
풖=(푡,풙)
2 carried out and took the average result for the
푠. 푡. 풙 푗풙 ≤ 푡 − 𝜎 , ∀푗 ∈ 퐾 optimal solution value and the signal-to-noise-
풙 풙 ≤ 푃 , 푡 > 0, ratio received at legitimate destination and
‖풖푙−풖푙−1‖ | (풖푙)− (풖푙−1)| eavesdroppers for the comparison. The
Until: ≤ 휀 or ≤ 휀
1+‖풖푙‖ 1+| (풖푙)| experimental results are as follows:
𝜎2+ 풙푙 풁풙푙
where (풖푙) = ( )
푡푙
Output: 푅 = ℎ(푡푙, 풙푙) = (풖푙), SNR , SNR .
푠 d e
V. EXPERIMENT AND RESULTS
This section presents the experimental
results and evaluation of all four proposed
methods in part IV. We compare the quality of
AF scheme to DF scheme in wireless relying
network from the perspectives of the values of
secrecy rate. It shows that, DF scheme has
better secrecy performance than AF scheme. In
the rest of this section, we also describe
received signal-to-noise-ratio at destination and
eavesdroppers. From this viewpoint, it is clear
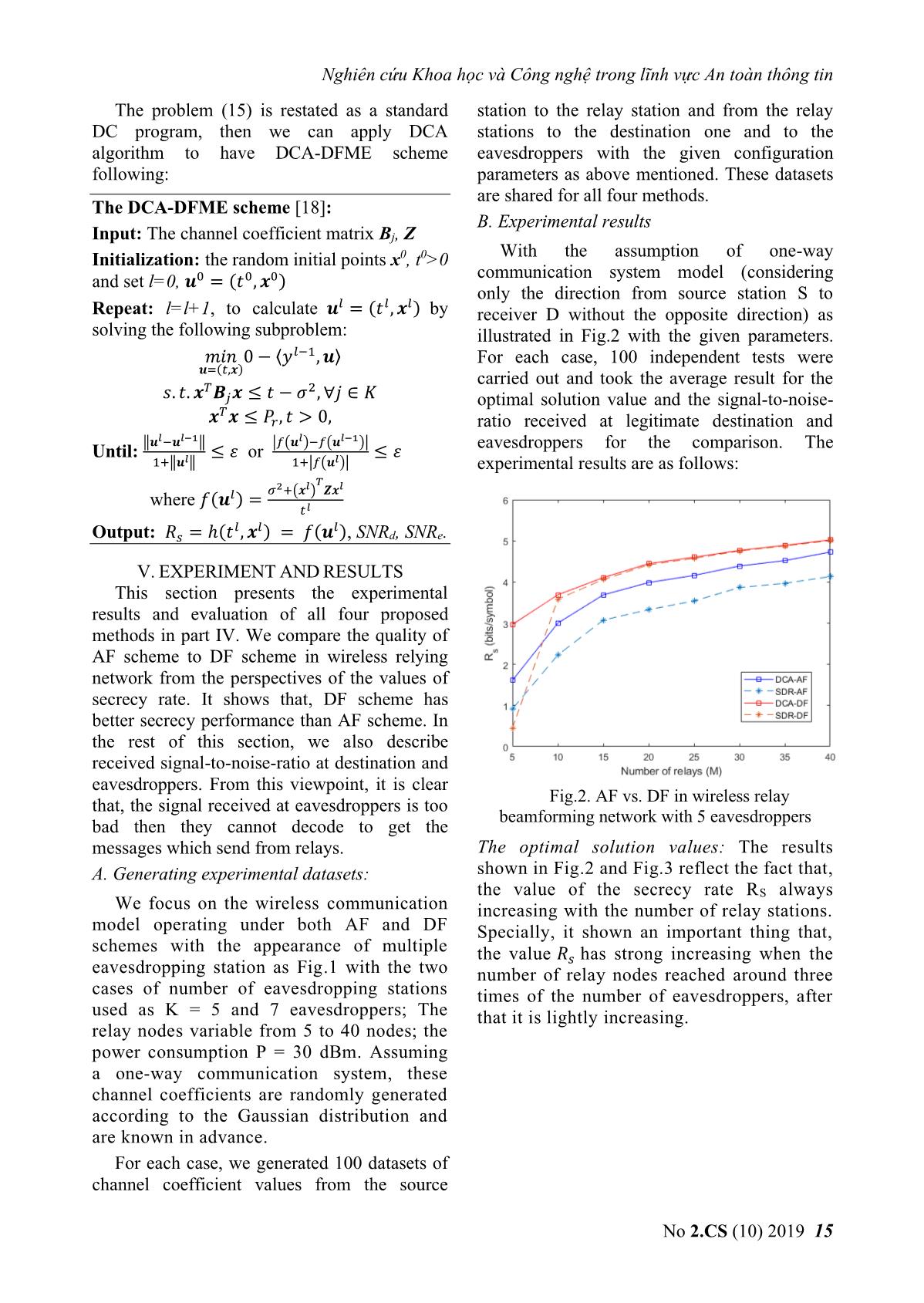
Fig.2. AF vs. DF in wireless relay
that, the signal received at eavesdroppers is too
beamforming network with 5 eavesdroppers
bad then they cannot decode to get the
messages which send from relays. The optimal solution values: The results
A. Generating experimental datasets: shown in Fig.2 and Fig.3 reflect the fact that,
the value of the secrecy rate RS always
We focus on the wireless communication increasing with the number of relay stations.
model operating under both AF and DF Specially, it shown an important thing that,
schemes with the appearance of multiple
the value 푅푠 has strong increasing when the
eavesdropping station as Fig.1 with the two number of relay nodes reached around three
cases of number of eavesdropping stations times of the number of eavesdroppers, after
used as K = 5 and 7 eavesdroppers; The that it is lightly increasing.
relay nodes variable from 5 to 40 nodes; the
power consumption P = 30 dBm. Assuming
a one-way communication system, these
channel coefficients are randomly generated
according to the Gaussian distribution and
are known in advance.
For each case, we generated 100 datasets of
channel coefficient values from the source
No 2.CS (10) 2019 15
Journal of Science and Technology on Information Security
values at eavesdroppers in the Null steering
case as in the Tables 2 is suitable with the
constrain of this system model (11). When the
number of relays and eavesdroppers are
equally, these SNRs become to similar then
the Rs values down to zero (1) as in Fig.2 and
Fig.3.
IV. CONCLUSION
With the emergence of 5G communication
networks and the powerful development of IoT
networks, wireless communication networks
are gradually replacing fiber optic
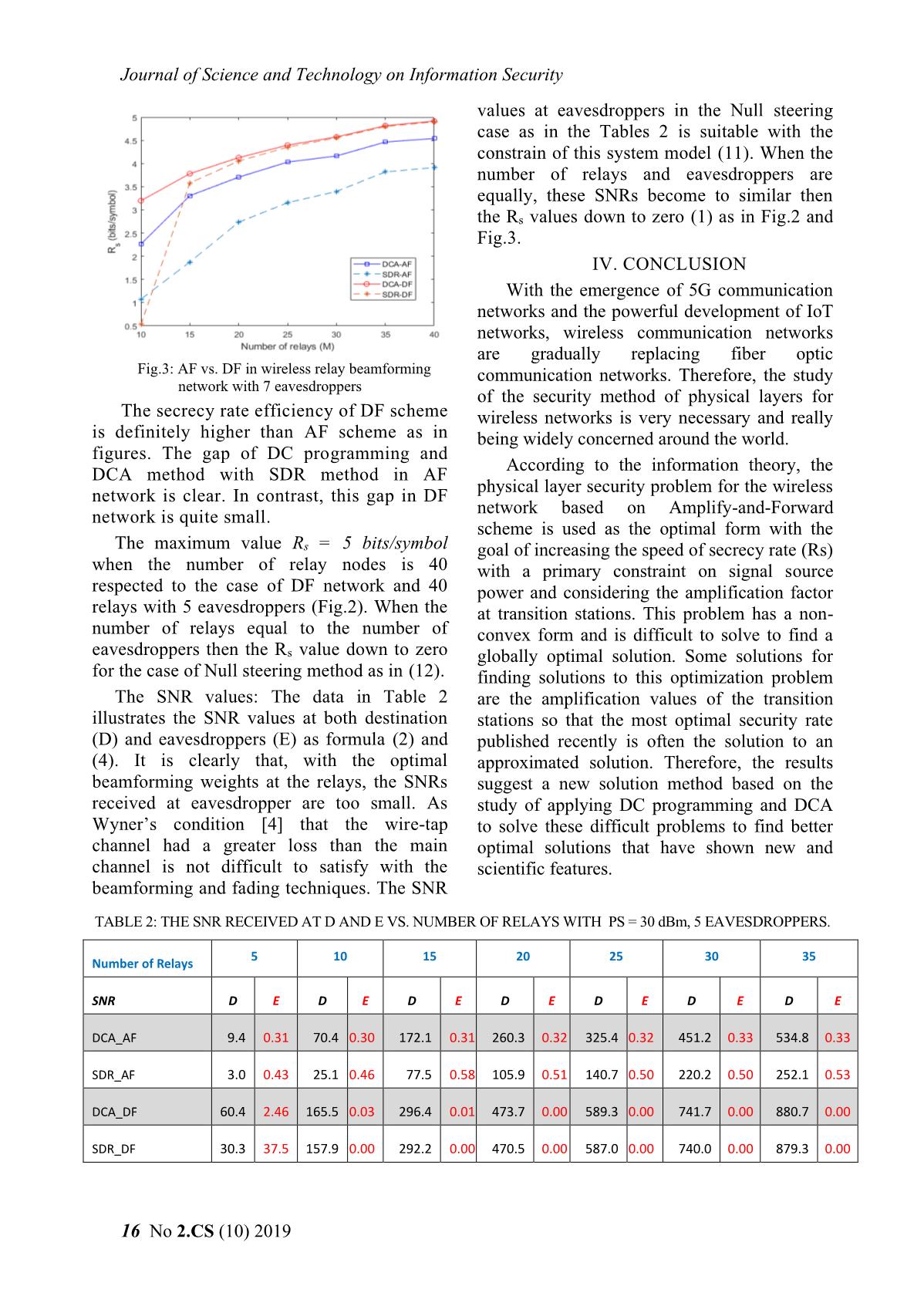
Fig.3: AF vs. DF in wireless relay beamforming communication networks. Therefore, the study
network with 7 eavesdroppers
of the security method of physical layers for
The secrecy rate efficiency of DF scheme wireless networks is very necessary and really
is definitely higher than AF scheme as in being widely concerned around the world.
figures. The gap of DC programming and
According to the information theory, the
DCA method with SDR method in AF
physical layer security problem for the wireless
network is clear. In contrast, this gap in DF
network based on Amplify-and-Forward
network is quite small.
scheme is used as the optimal form with the
The maximum value Rs = 5 bits/symbol goal of increasing the speed of secrecy rate (Rs)
when the number of relay nodes is 40 with a primary constraint on signal source
respected to the case of DF network and 40 power and considering the amplification factor
relays with 5 eavesdroppers (Fig.2). When the at transition stations. This problem has a non-
number of relays equal to the number of convex form and is difficult to solve to find a
eavesdroppers then the Rs value down to zero globally optimal solution. Some solutions for
for the case of Null steering method as in (12). finding solutions to this optimization problem
The SNR values: The data in Table 2 are the amplification values of the transition
illustrates the SNR values at both destination stations so that the most optimal security rate
(D) and eavesdroppers (E) as formula (2) and published recently is often the solution to an
(4). It is clearly that, with the optimal approximated solution. Therefore, the results
beamforming weights at the relays, the SNRs suggest a new solution method based on the
received at eavesdropper are too small. As study of applying DC programming and DCA
Wyner’s condition [4] that the wire-tap to solve these difficult problems to find better
channel had a greater loss than the main optimal solutions that have shown new and
channel is not difficult to satisfy with the scientific features.
beamforming and fading techniques. The SNR
TABLE 2: THE SNR RECEIVED AT D AND E VS. NUMBER OF RELAYS WITH PS = 30 dBm, 5 EAVESDROPPERS.
5 10 15 20 25 30 35
Number of Relays
SNR D E D E D E D E D E D E D E
DCA_AF 9.4 0.31 70.4 0.30 172.1 0.31 260.3 0.32 325.4 0.32 451.2 0.33 534.8 0.33
SDR_AF 3.0 0.43 25.1 0.46 77.5 0.58 105.9 0.51 140.7 0.50 220.2 0.50 252.1 0.53
DCA_DF 60.4 2.46 165.5 0.03 296.4 0.01 473.7 0.00 589.3 0.00 741.7 0.00 880.7 0.00
SDR_DF 30.3 37.5 157.9 0.00 292.2 0.00 470.5 0.00 587.0 0.00 740.0 0.00 879.3 0.00
16 No 2.CS (10) 2019
Nghiên cứu Khoa học và Công nghệ trong lĩnh vực An toàn thông tin
REFERENCE [13]. O. G. Aliu, A. Imran, M. A. Imran, and B. Evans,
“A Survey of Self Organisation in Future Cellular
[1]. C. E. Shannon, “Communication theory of secrecy Networks,” IEEE Commun. Surv. Tutor., vol. 15,
systems,” Bell Syst. Tech. J., vol. 28, no. 4, pp. no. 1, pp. 336–361, First 2013.
656–715, Oct. 1949, [14]. F. I. Kandah, O. Nichols, and Li Yang, “Efficient
[2]. G. de Meulenaer, F. Gosset, F.-X. Standaert, and key management for Big Data gathering in
O. Pereira, “On the Energy Cost of dynamic sensor networks,” in 2017 International
Communication and Cryptography in Wireless Conference on Computing, Networking and
Sensor Networks,” in 2008 IEEE International Communications (ICNC), 2017, pp. 667–671, doi:
Conference on Wireless and Mobile Computing, 10.1109/ICCNC.2017.7876209.
Networking and Communications, 2008, pp. 580– [15]. Physical Layer Security: Bounds, Codes and
585, doi: 10.1109/WiMob.2008.16. Protocols (João Barros) - Part 2
[3]. D. Wang, B. Bai, W. Zhao, and Z. Han, “A Survey (SPCodingSchool).
of Optimization Approaches for Wireless Physical [16]. N. N. Tuan and D. V. Son, “DC Programming and
Layer Security,” ArXiv190107955 Cs Math, Jan. DCA for Enhancing Physical Layer Security in
2019. Amplify-and-Forward Relay Beamforming
[4]. A. D. Wyner, “The Wire-Tap Channel,” Bell Syst. Networks Based on the SNR Approach,” in
Tech. J., vol. 54, no. 8, pp. 1355–1387, Oct. 1975, Advanced Computational Methods for Knowledge
doi: 10.1002/j.1538-7305.1975.tb02040.x. Engineering, vol. 629, N.-T. Le, T. van Do, N. T.
[5]. I. Csiszar and J. Korner, “Broadcast channels with Nguyen, and H. A. L. Thi, Eds. Cham: Springer
confidential messages,” IEEE Trans. Inf. Theory, International Publishing, 2018, pp. 23–33.
vol. 24, no. 3, pp. 339–348, May 1978. [17]. S. Sarma, S. Agnihotri, and J. Kuri, “Secure
[6]. F. Jameel, S. Wyne, G. Kaddoum, and T. Q. Communication in Amplify-and-Forward
Duong, “A Comprehensive Survey on Cooperative Networks with Multiple Eavesdroppers: Decoding
Relaying and Jamming Strategies for Physical with SNR Thresholds,” Wirel. Pers. Commun.,
Layer Security,” IEEE Commun. Surv. Tutor., vol. vol. 85, no. 4, pp. 1945–1956, Dec. 2015.
21, no. 3, pp. 2734–2771, 2019, doi: [18]. N. N. Tuan and T. T. Thuy, “Physical Layer
10.1109/COMST.2018.2865607. Security Cognitive Decode-and-Forward Relay
[7]. Tạp chí An toàn thông tin, “Bảo mật dữ liệu tầng Beamforming Network with Multiple
vật lý trong mạng truyền tin không dây: Những ý Eavesdroppers,” in Intelligent Information and
tưởng đầu tiên và hướng nghiên cứu hiện nay”, Database Systems, vol. 11432, N. T. Nguyen, F. L.
Gaol, T.-P. Hong, and B. Trawiński, Eds. Cham:
viet-cua-101779. [Accessed: 15-Feb-2020]. Springer International Publishing, 2019, pp. 254–
[8]. X. Chen, D. W. K. Ng, W. H. Gerstacker, and H.- 263.
H. Chen, “A Survey on Multiple-Antenna [19]. H. A. Le Thi, V. N. Huynh, and T. P. Dinh, “DC
Techniques for Physical Layer Security,” IEEE Programming and DCA for General DC
Commun. Surv. Tutor., vol. 19, no. 2, pp. 1027– Programs,” in Advanced Computational Methods
1053, Secondquarter 2017. for Knowledge Engineering, Cham, 2014, pp. 15–
[9]. L. Dong, Z. Han, A. P. Petropulu, and H. V. Poor, 35, doi: 10.1007/978-3-319-06569-4_2.
“Improving Wireless Physical Layer Security via
Cooperating Relays,” IEEE Trans. Signal Process., ABOUT THE AUTHOR
vol. 58, no. 3, pp. 1875–1888, Mar. 2010, doi:
M.Sc Nhu Tuan Nguyen
10.1109/TSP.2009.2038412.
[10]. Y.-W. P. Hong, P.-C. Lan, and C.-C. J. Kuo, Workplace: Vietnam Information
“Enhancing Physical-Layer Secrecy in Security Journal
Multiantenna Wireless Systems: An Overview of Email:nguyennhutuan@bcy.gov.vn
Signal Processing Approaches,” IEEE Signal
The education process: received
Process. Mag., vol. 30, no. 5, pp. 29–40, Sep.
the Master of science degree in
2013, doi: 10.1109/MSP.2013.2256953.
Engineering from Academy of
[11]. A. Mukherjee, S. A. A. Fakoorian, J. Huang, and Cryptography Technique in
A. L. Swindlehurst, “Principles of Physical Layer 2007. He is a PhD student in
Security in Multiuser Wireless Networks: A Academy of Cryptography Technique.
Survey,” IEEE Commun. Surv. Tutor., vol. 16, no.
3, pp. 1550–1573, 2014. Research today: machine learning and data mining
in cyber security, cloud computing security,
[12]. H.-M. Wang and X.-G. Xia, “Enhancing wireless
physical layer security.
secrecy via cooperation: signal design and
optimization,” IEEE Commun. Mag., vol. 53, no.
12, pp. 47–53, Dec. 2015, doi:
10.1109/MCOM.2015.7355565.
No 2.CS (10) 2019 17 File đính kèm:
 decode_and_forward_vs_amplify_andforward_scheme_in_physical.pdf
decode_and_forward_vs_amplify_andforward_scheme_in_physical.pdf

