Bài giảng Other Block Ciphers
What will we learn?
• The most important modes of operation for
block ciphers in practice
• Security pitfalls when using modes of
operations
• The principles of key whitening
• Why double encryption is not a good idea,
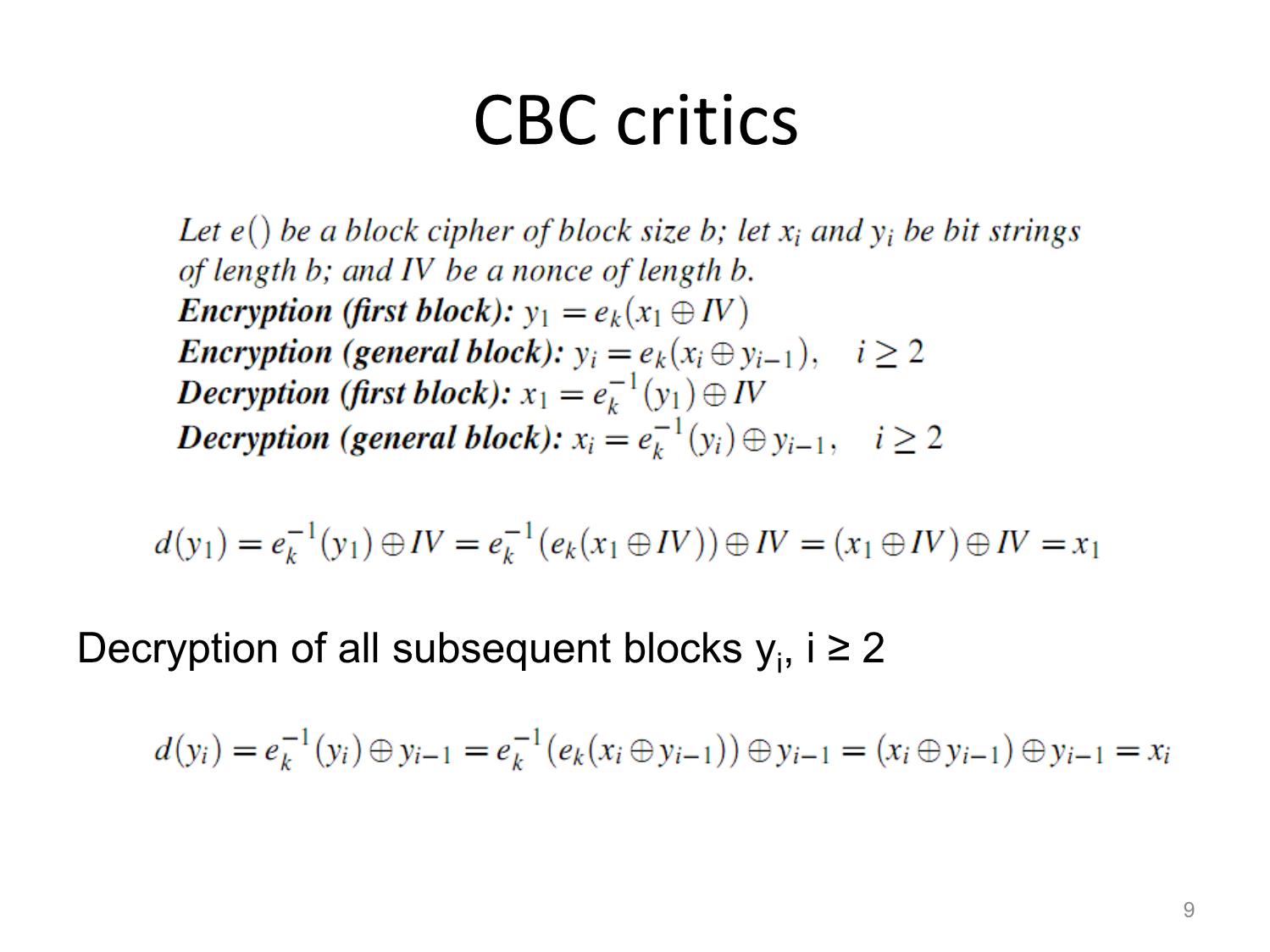
and the meet-in-the-middle attack
• Triple encryption
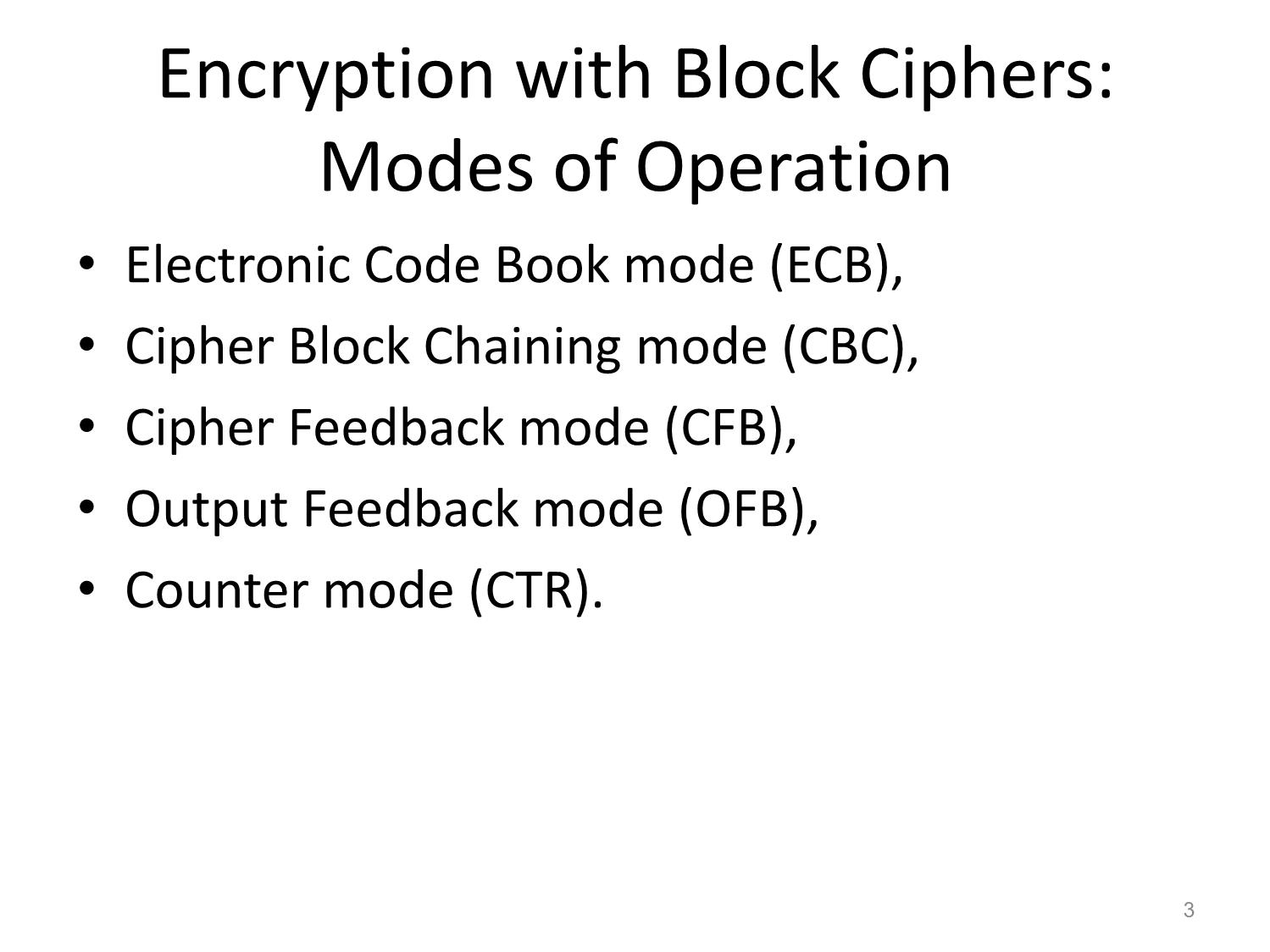
2Encryption with Block Ciphers:
Modes of Operation
• Electronic Code Book mode (ECB),
• Cipher Block Chaining mode (CBC),
• Cipher Feedback mode (CFB),
• Output Feedback mode (OFB),
• Counter mode (CTR).

Trang 1

Trang 2
Trang 3
Trang 4

Trang 5

Trang 6
Trang 7
Trang 8
Trang 9

Trang 10
Tải về để xem bản đầy đủ
Bạn đang xem 10 trang mẫu của tài liệu "Bài giảng Other Block Ciphers", để tải tài liệu gốc về máy hãy click vào nút Download ở trên
Tóm tắt nội dung tài liệu: Bài giảng Other Block Ciphers

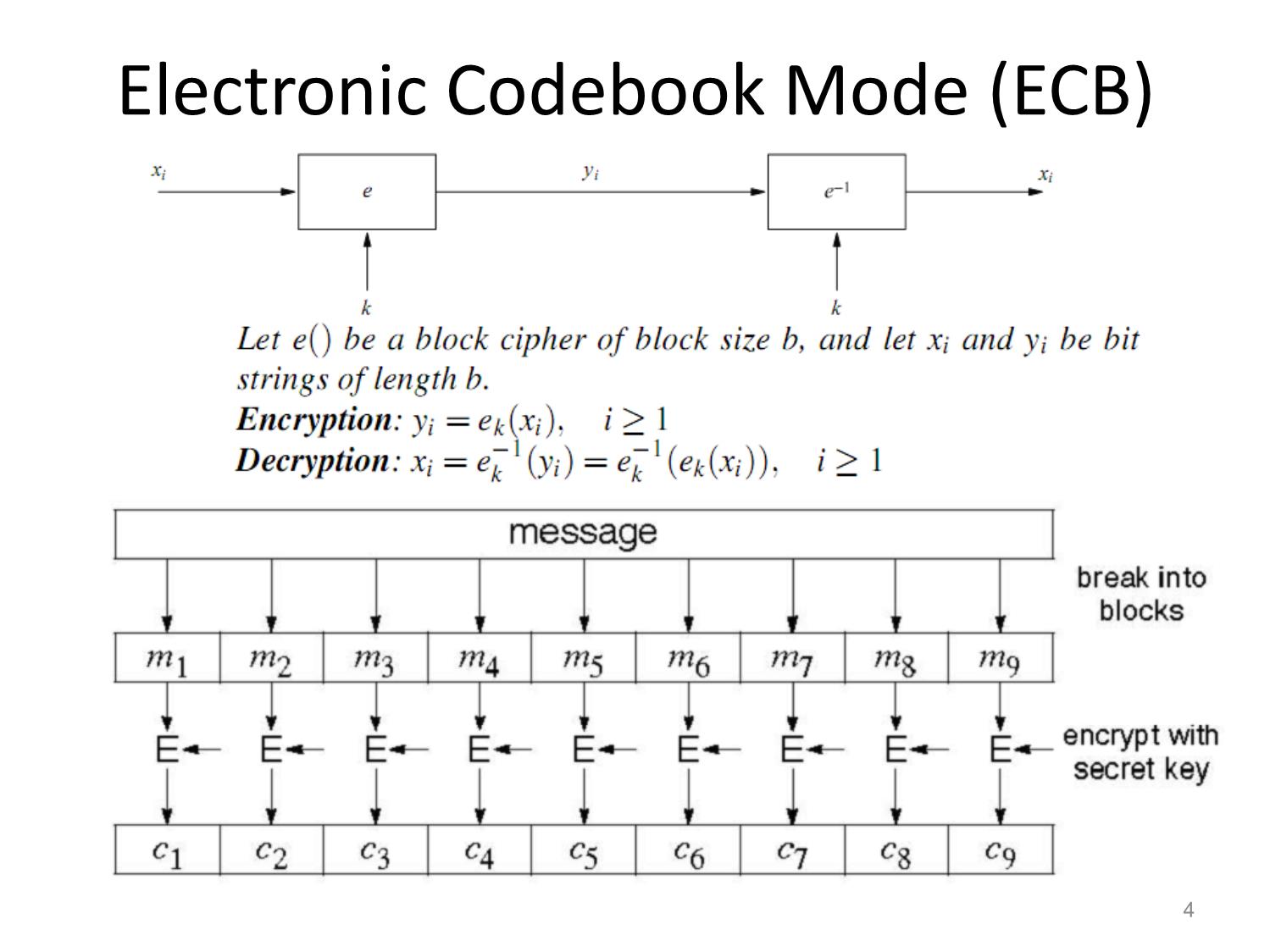
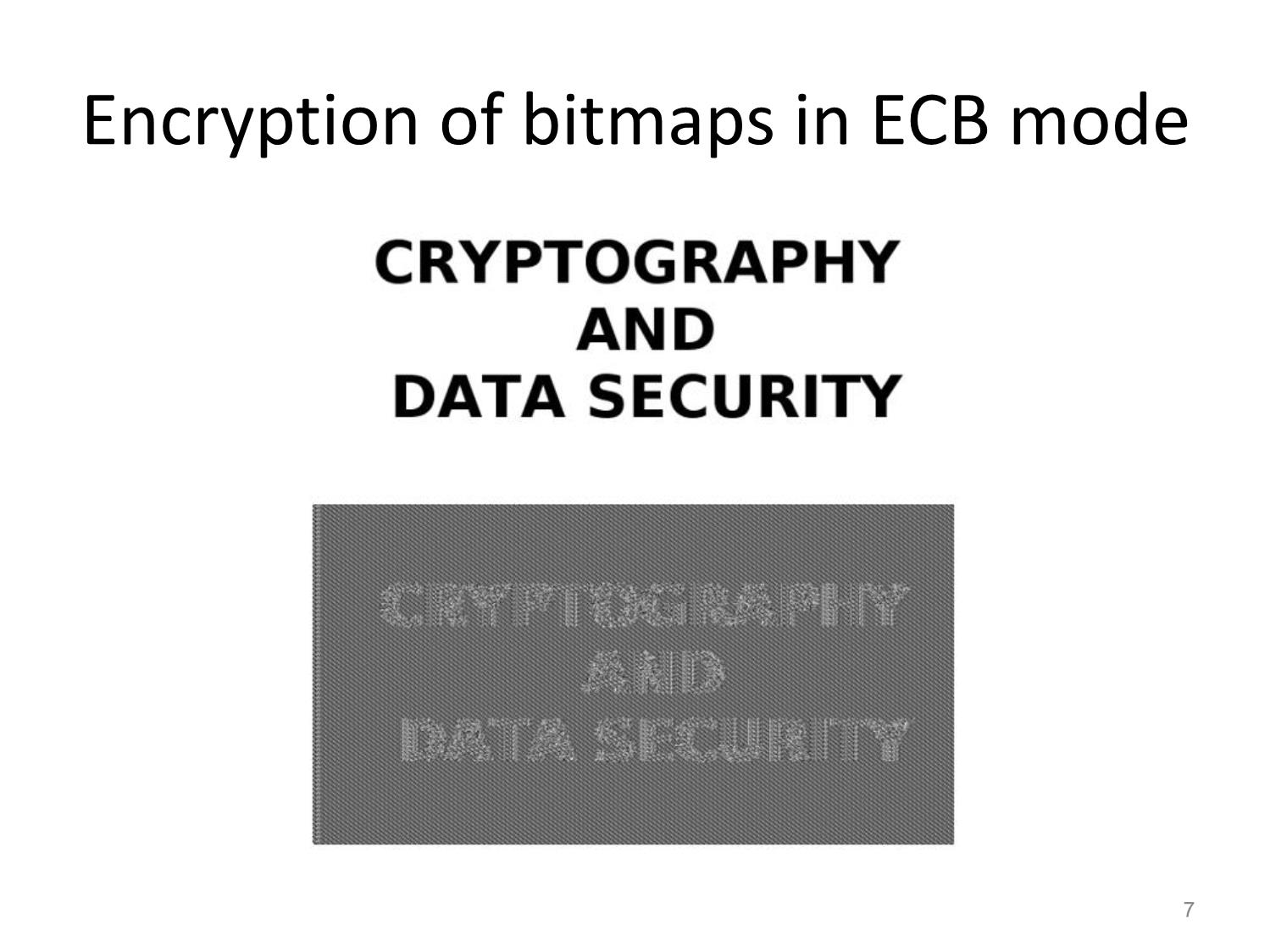
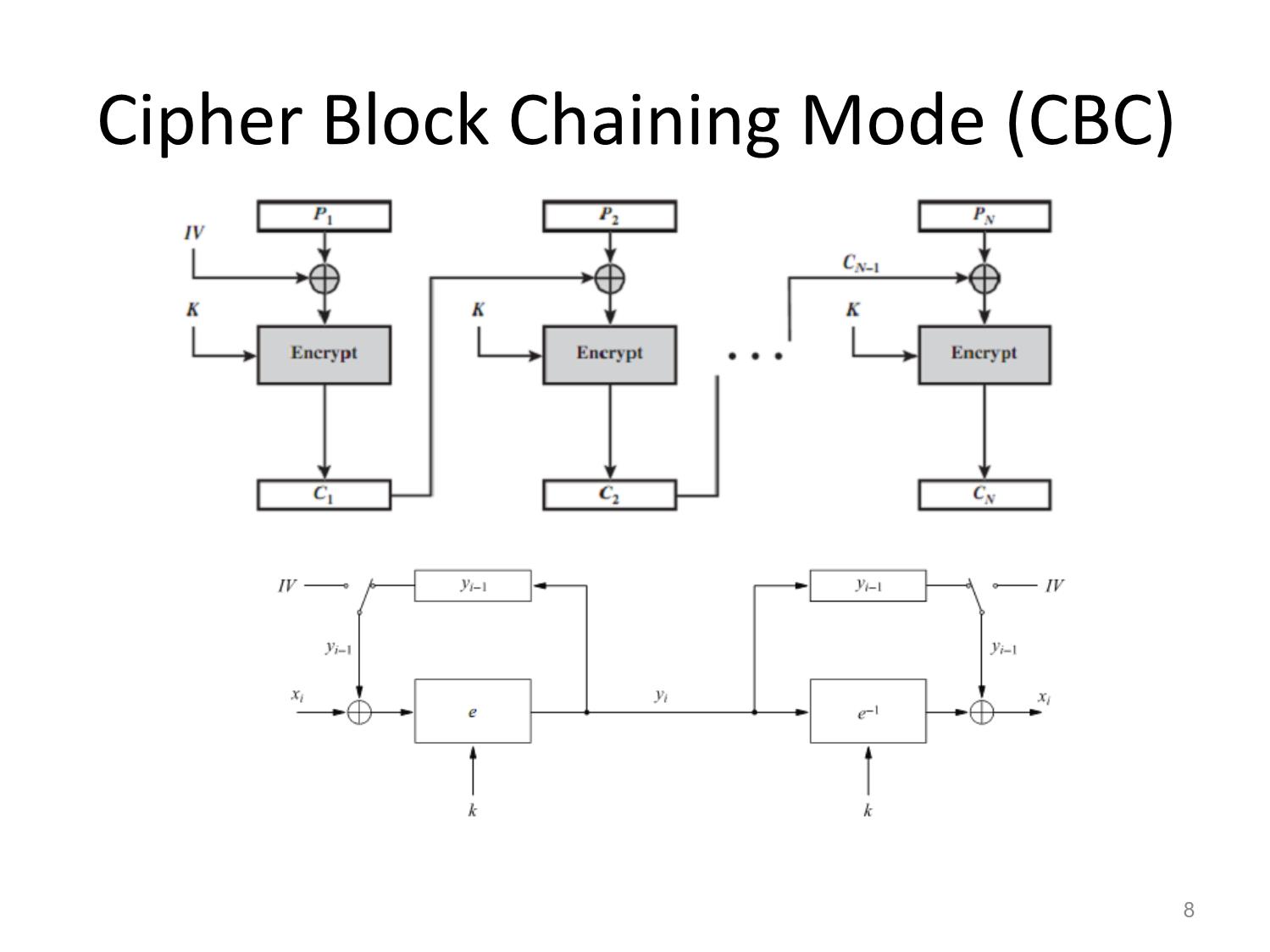
Other Block Ciphers Huỳnh Trọng Thưa htthua@ptithcm.edu.vn What will we learn? • The most important modes of operation for block ciphers in practice • Security pitfalls when using modes of operations • The principles of key whitening • Why double encryption is not a good idea, and the meet-in-the-middle attack • Triple encryption 2 Encryption with Block Ciphers: Modes of Operation • Electronic Code Book mode (ECB), • Cipher Block Chaining mode (CBC), • Cipher Feedback mode (CFB), • Output Feedback mode (OFB), • Counter mode (CTR). 3 Electronic Codebook Mode (ECB) 4 ECB critics • Advantages – Block synchronization is not necessary. • Problem – identical plaintext blocks result in identical ciphertext blocks, as long as the key does not change – Replay attack • Usage: – not recommended to encrypt more than one block of data – encryption in database 5 Ex of Substitution attack against electronic bank transfer • Oscar observes the ciphertexts going through the communication network. • After a while he can recognize the five blocks of his own transfer. He now stores blocks 1, 3 and 4 of these transfers. • The same key is used for several other transfers between bank A and B. • By comparing blocks 1 and 3 of all subsequent messages with the ones he has stored, Oscar recognizes all transfers that are made from some account at bank A to some account at bank B. • He now simply replaces block 4 — which contains the receiving account number — with the block 4 that he stored before. 6 Encryption of bitmaps in ECB mode 7 Cipher Block Chaining Mode (CBC) 8 CBC critics Decryption of all subsequent blocks yi, i ≥ 2 9 CBC critics (cont.) • Good – Randomized encryption: repeated text gets mapped to different encrypted data. – A ciphertext block depends on all preceding plaintext blocks blocks • reorder affects decryption • Bad – Errors in one block propagate to two blocks – Sequential encryption, cannot use parallel hardware 10 Encryption of bitmaps in CBC mode 11 Output Feedback Mode (OFB) Key stream is not generated bitwise but instead in a blockwise fashion. 12 Cipher Feedback Mode (CFB) 13 Counter Mode (CTR) 14 Exhaustive Key Search Revisited • A brute-force attack can produce false positive results. • Ex: A cipher with a block width of 64 bit and a key size of 80 bit. we find on average 280/264 = 16 2 keys that perform the mapping ek(x1)= y1. Multiple keys map between one plaintext and one ciphertext 15 Increasing the Security of Block Ciphers • Multiple encryption – Double Encryption – Triple Encryption – Problem: Meet-in-the-Middle Attack • Key whitening 16 Double Encryption and Meet-in- the-Middle Attack • Key length: κ bits • Brute-force attack: require 2κ ·2κ =22κ encryptions (or decryptions) • Meet-in-the-middle attack: – The total complexity is 2κ +2κ = 2·2κ = 2κ+1. 17 Triple Encryption and Meet-in-the- Middle Attack • Key length: κ bits • Brute-force attack: require 2κ ·2κ ·2κ =23κ encryptions (or decryptions) • Meet-in-the-middle attack: – The total complexity is 22κ. – 3DES;:56 bits key => attacker performs 2112 key tests (not 2168) 18 Key Whitening 19
File đính kèm:
 bai_giang_other_block_ciphers.pdf
bai_giang_other_block_ciphers.pdf

