Bài giảng Mã hóa DES Data Encryption Standard
Data Encryption Standard (DES)
and Alternatives
• Basic design ideas of block ciphers, including
confusion (xáo trộn) and diffusion (khuếch
tán), which are important properties of all
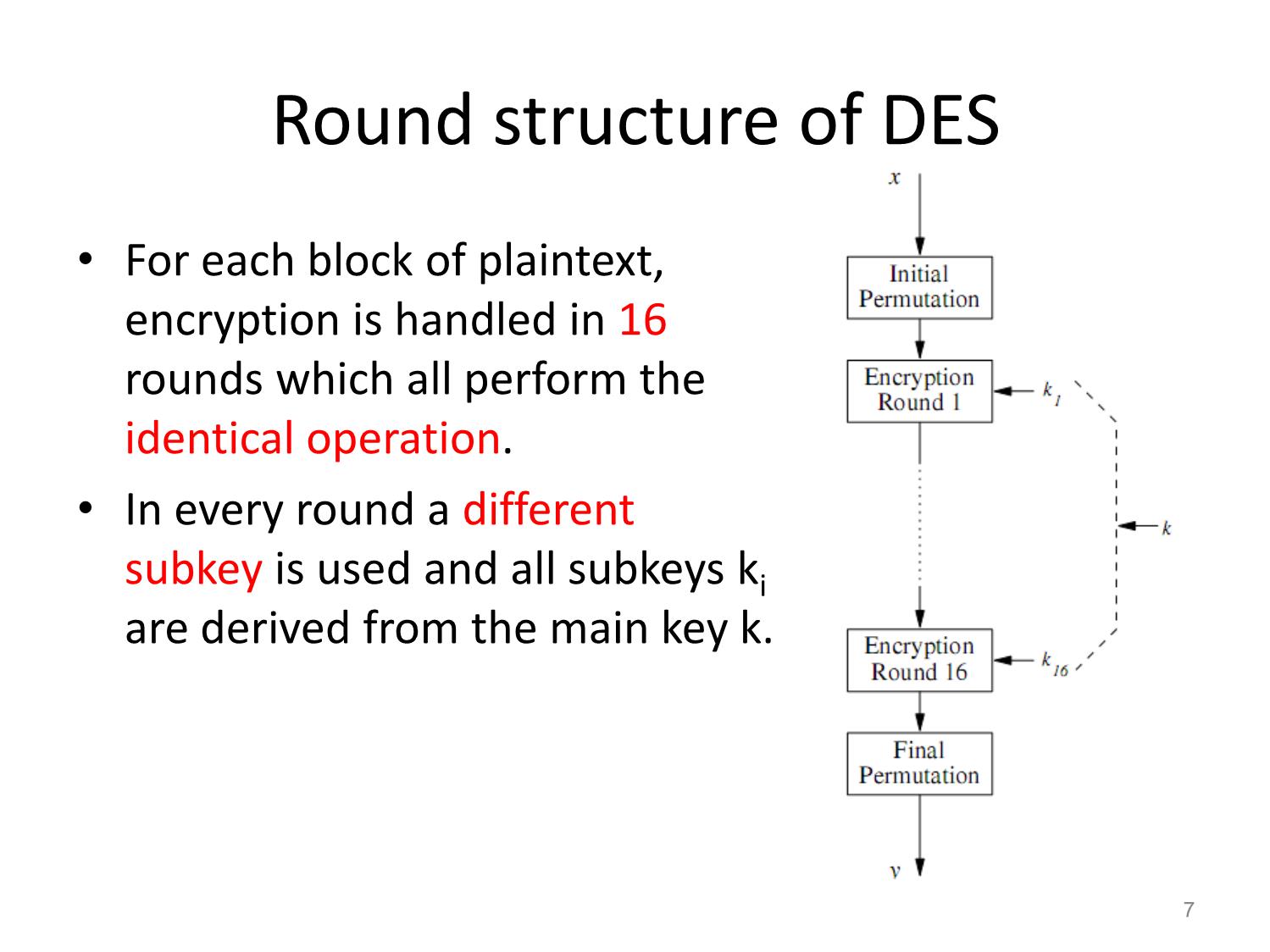
modern block ciphers
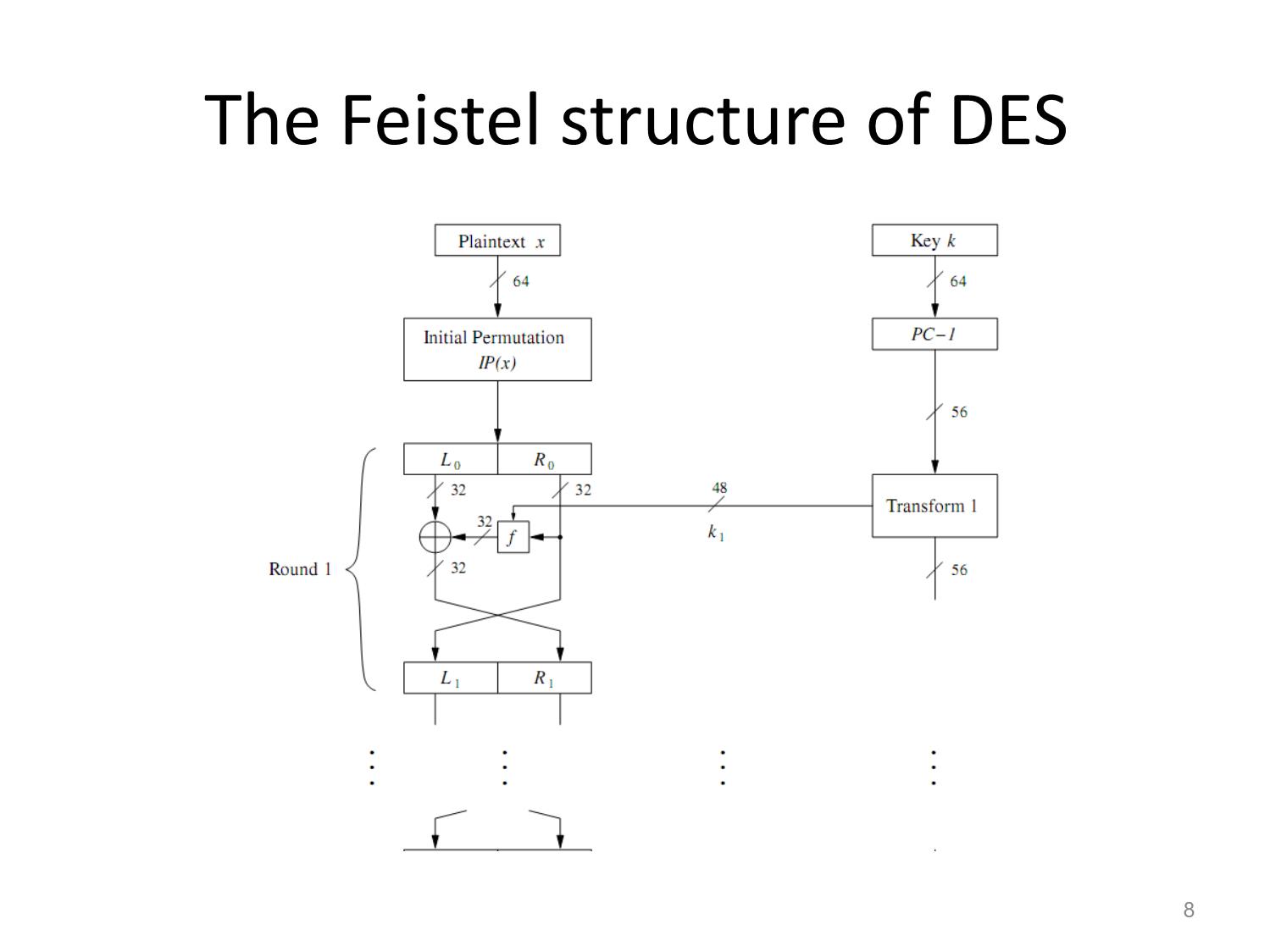
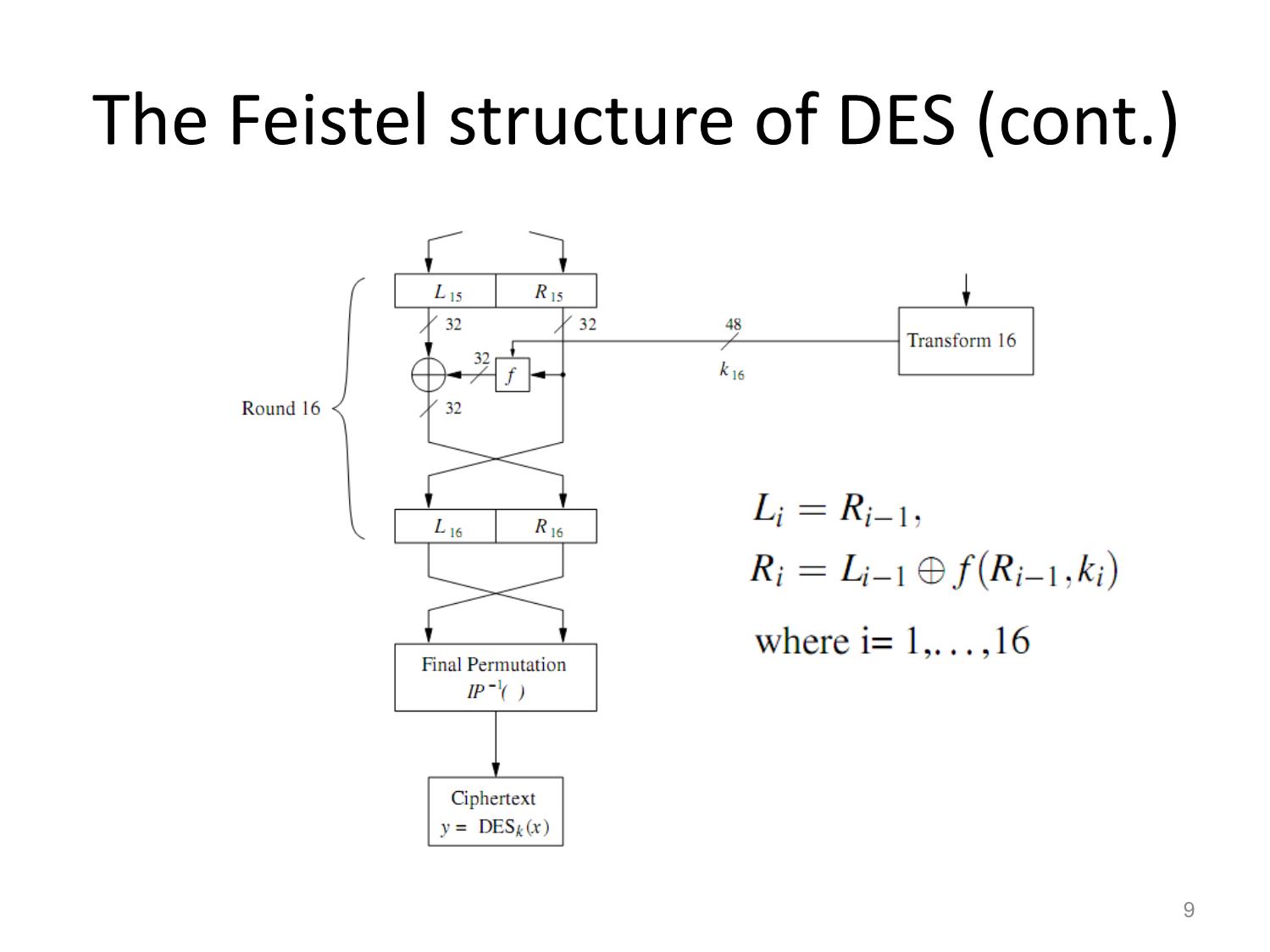
• The internal structure of DES, including Feistel
networks, S-boxes and the key schedule.
• Alternatives to DES, including 3DES
3Confusion and Diffusion
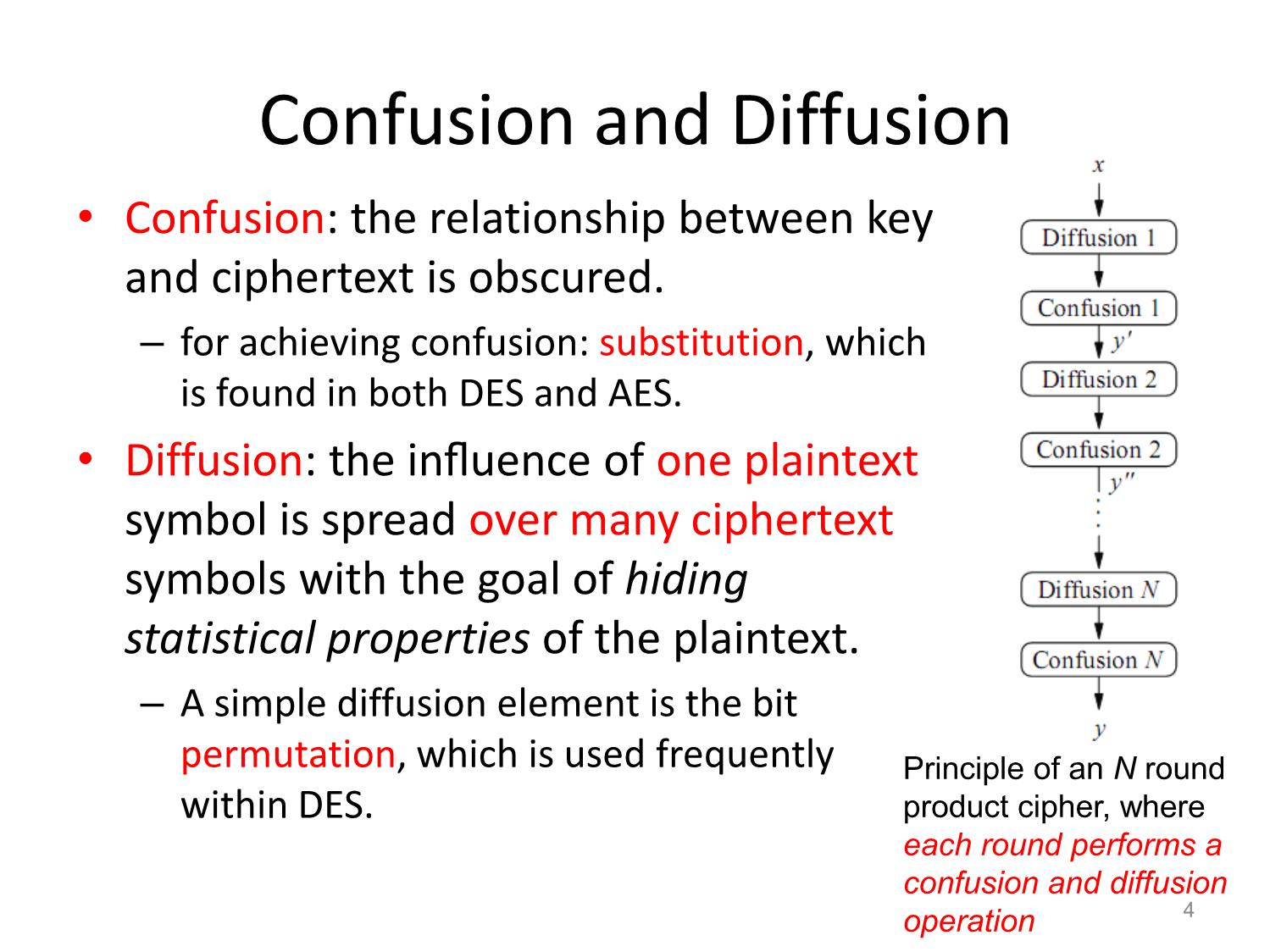
• Confusion: the relationship between key
and ciphertext is obscured.
– for achieving confusion: substitution, which
is found in both DES and AES.
• Diffusion: the influence of one plaintext
symbol is spread over many ciphertext
symbols with the goal of hiding
statistical properties of the plaintext.
– A simple diffusion element is the bit
permutation, which is used frequently
within DES.

Trang 1

Trang 2
Trang 3
Trang 4
Trang 5
Trang 6
Trang 7
Trang 8
Trang 9

Trang 10
Tải về để xem bản đầy đủ
Tóm tắt nội dung tài liệu: Bài giảng Mã hóa DES Data Encryption Standard

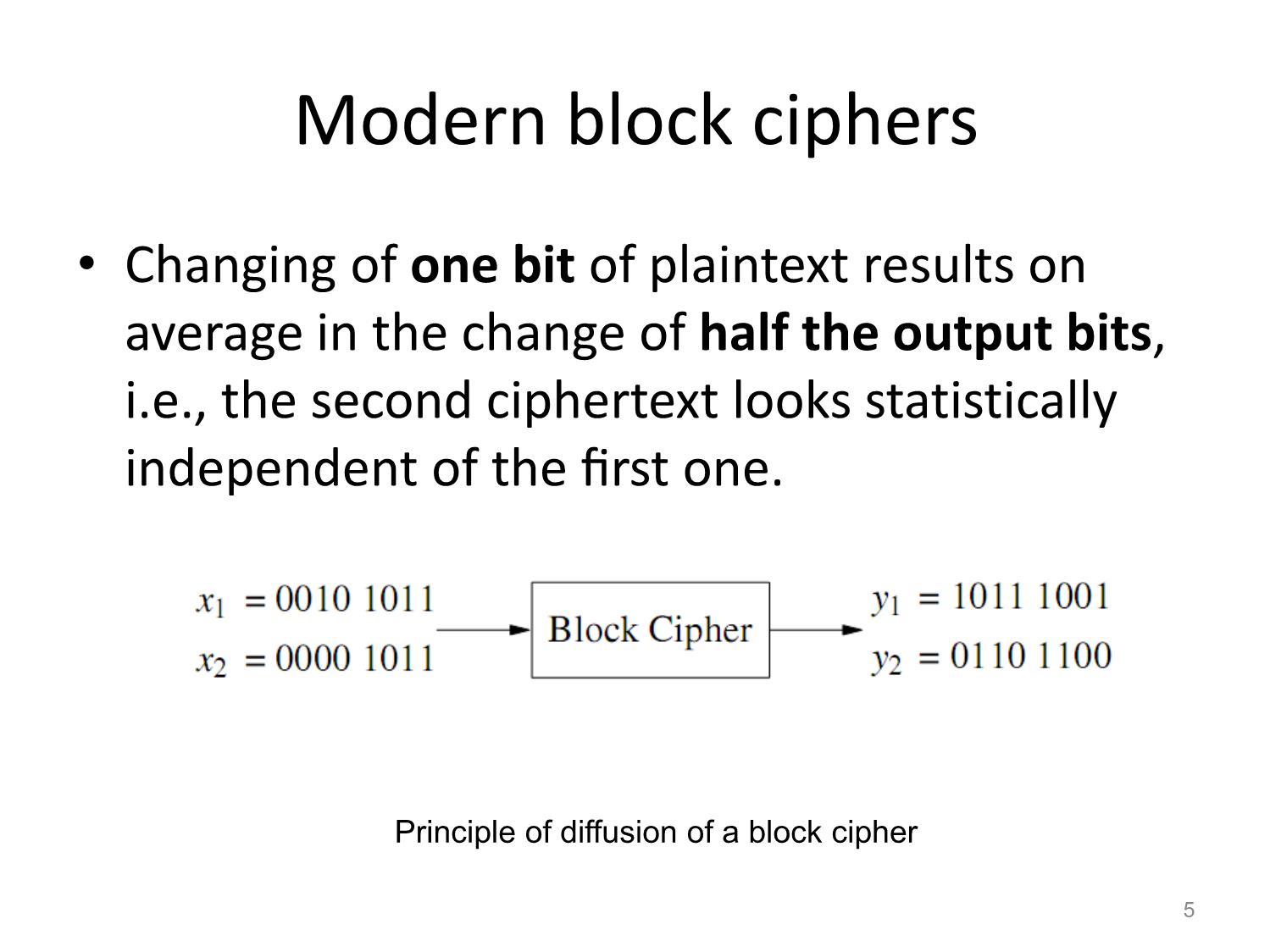
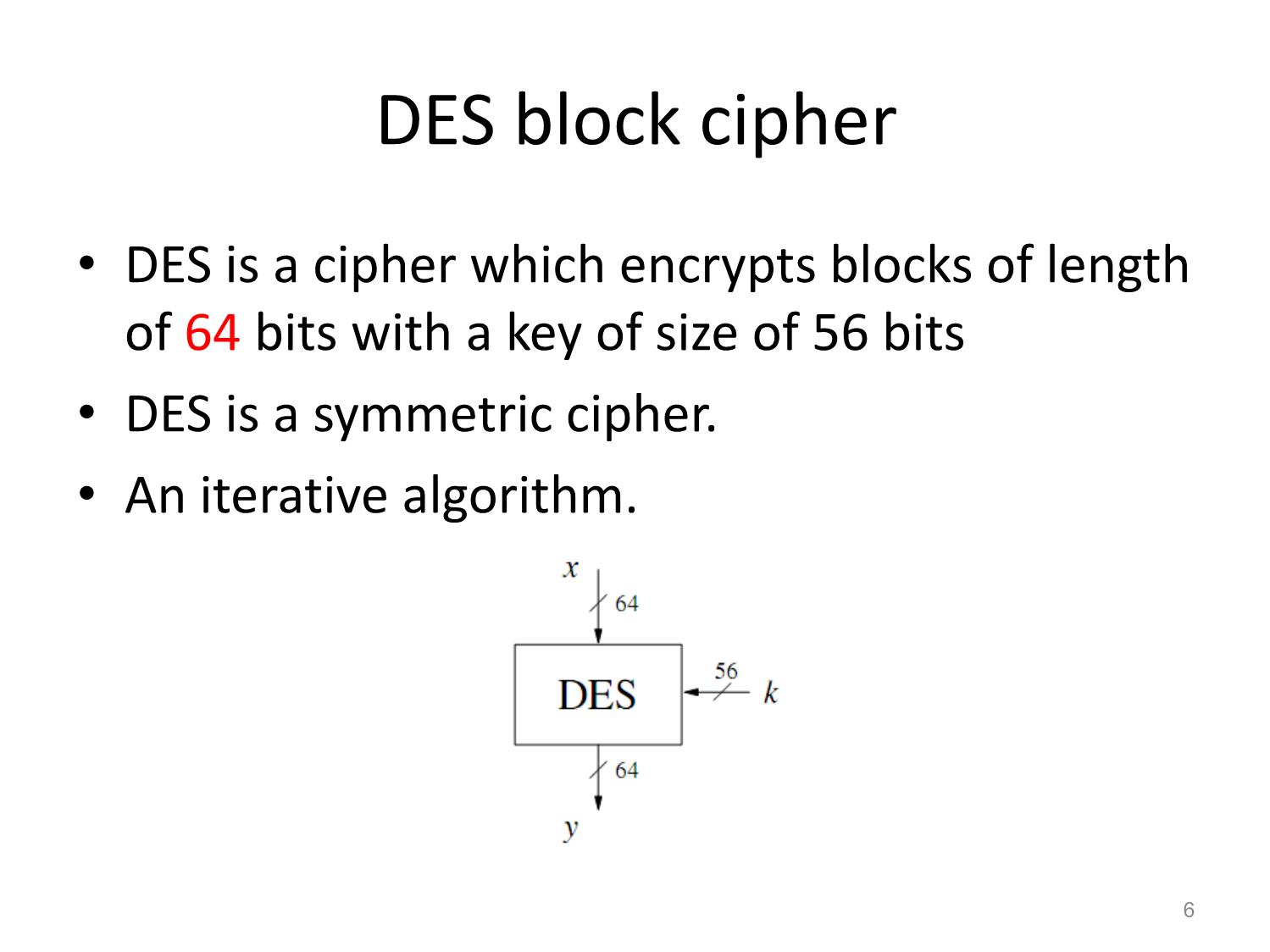
Mã hóa DES Data Encryption Standard Huỳnh Trọng Thưa htthua@ptithcm.edu.vn Part 1 - Encryption of DES • Feistel structure of DES • S-boxes • Key Schedule 2 Data Encryption Standard (DES) and Alternatives • Basic design ideas of block ciphers, including confusion (xáo trộn) and diffusion (khuếch tán), which are important properties of all modern block ciphers • The internal structure of DES, including Feistel networks, S-boxes and the key schedule. • Alternatives to DES, including 3DES 3 Confusion and Diffusion • Confusion: the relationship between key and ciphertext is obscured. – for achieving confusion: substitution, which is found in both DES and AES. • Diffusion: the influence of one plaintext symbol is spread over many ciphertext symbols with the goal of hiding statistical properties of the plaintext. – A simple diffusion element is the bit permutation, which is used frequently Principle of an N round within DES. product cipher, where each round performs a confusion and diffusion operation 4 Modern block ciphers • Changing of one bit of plaintext results on average in the change of half the output bits, i.e., the second ciphertext looks statistically independent of the first one. Principle of diffusion of a block cipher 5 DES block cipher • DES is a cipher which encrypts blocks of length of 64 bits with a key of size of 56 bits • DES is a symmetric cipher. • An iterative algorithm. 6 Round structure of DES • For each block of plaintext, encryption is handled in 16 rounds which all perform the identical operation. • In every round a different subkey is used and all subkeys ki are derived from the main key k. 7 The Feistel structure of DES 8 The Feistel structure of DES (cont.) 9 Internal Structure of DES • Initial and Final Permutation • f – function • Key Schedule 10 Initial and Final Permutation • are bitwise permutations bit swaps of the initial permutation bit swaps of the final permutation read from left to right, top to bottom 11 f - function 12 Bit swaps of the expansion function E 13 S-boxes • Each S-box contains 26 =64 entries. • Each entry is a 4-bit value. Decoding of the input 1001012 by S-box 1 • Ex: The S-box input b =(100101)2 indicates the row 112 = 3 (i.e., fourth row, numbering starts with 002) and the column 00102 = 2 (i.e., the third column). If the input b is fed into S-box 1, the output is S1(37 = 1001012)= 8 = 10002. 14 S-boxes table for Ref. 15 The permutation P within the f - function 16 Key Schedule • PC-1: ignoring every eighth bit (64-bit key -> 56 bits ) • 56-bit key is split into two halves C0 and D0 • The two 28-bit halves are cyclically shifted, i.e., rotated, Initial key permutation PC−1 left by one or two bit positions depending on the round i. In rounds i = 1,2,9,16, the two halves are rotated left by one bit. In the other rounds i 1,2,9,16, the two halves are rotated left by two bits. 17 Key schedule for DES encryption Round key permutation PC−2 18 Part 2 - Descryption of DES • Descryption of DES • Security of DES • DES Alternatives 19 Block diagram for DES decryption y 20 Block diagram for DES decryption (cont.) 21 Reversed Key Schedule • k16 can be directly derived after PC−1. • Round 1, the key is not rotated. • Rounds 2, 9, and 16 the two halves are rotated right by one bit. • Other rounds 3, 4, 5, 6, 7, 8, 10, 11, 12, 13, 14 and 15 the two halves are rotated right by two bits. 22 Reversed key schedule for decryption of DES 23 Why is the decryption function essentially the same as the encryption function? 24 Why is the decryption function essentially the same as the encryption function? (cont.) where i = 0,1,...,16. In particular, after the last decryption round: Finally, at the end of the decryption process, we have to reverse the initial permutation: 25 Security of DES • The key space is too small, i.e., the algorithm is vulnerable against brute-force attacks. • The design criteria of the S-boxes was kept secret and there might have existed an analytical attack that exploits mathematical properties of the S-boxes, but which is only known to the DES designers. 26 DES Alternatives • Advanced Encryption Standard (AES) and the AES Finalist Ciphers • Triple DES (3DES) and DESX • Lightweight Cipher PRESENT 27 Advanced Encryption Standard (AES) and the AES Finalist Ciphers • AES is with its three key lengths of 128, 192 and 256 bit secure • Against brute-force attacks for several decades • There are no analytical attacks with any reasonable chance of success known. 28 Triple DES (3DES) and DESX • 3DES consists of three subsequent DES encryptions with different keys Another version of 3DES is A different approach for strengthening DES is to use key whitening 29 Lightweight Cipher PRESENT 30 Next class • Advanced Encryption Standard (AES) 31
File đính kèm:
 bai_giang_ma_hoa_des_data_encryption_standard.pdf
bai_giang_ma_hoa_des_data_encryption_standard.pdf

