Authentication in E-Learning systems: Challenges and solutions
Digitization is gradually penetrating all aspects of modern society. As it changes the way people
communicate, technology has revolutionized education and training in the 21st century. With the
advantages of reasonable costs and flexible study time, online training is increasingly seen as an
attractive alternative to the full-time on-campus training model. To assure quality of distance training and learning, it is crucial for the online learning management system to make sure the person
accessing the course resources and performing learning activities is actually enrolled in the course.
One of the important factors determining the security of this process is user authentication. In most
cases, this role is done with a password, but the evidence shows that this method is easily compromised. While there are many alternatives available such as biometric methods, user-challenging
methods, smart card methods, etc. The strong development of technology that requires confidentiality and authentication must be tightly coupled. A qualitative survey of user authentication
systems is being used in today's E-learning systems and a comparative study of various different authentication mechanisms presented in this paper. There are many methods of user authentication
for online learning systems, but each method will have different advantages and disadvantages and
has not completely solved the challenges of user authentication. The issue of user authentication
still has many challenges that need to be solved thoroughly to improve the security of the system
as well as the trust of users and society. This paper provides an overview of our approach and
recommendations to address the mentioned issues. In addition, we propose a number of feasible
approaches to improve user data privacy as well as improve the effectiveness of the authentication
process in the online learning system.

Trang 1

Trang 2

Trang 3
Trang 4

Trang 5

Trang 6

Trang 7
Tóm tắt nội dung tài liệu: Authentication in E-Learning systems: Challenges and solutions

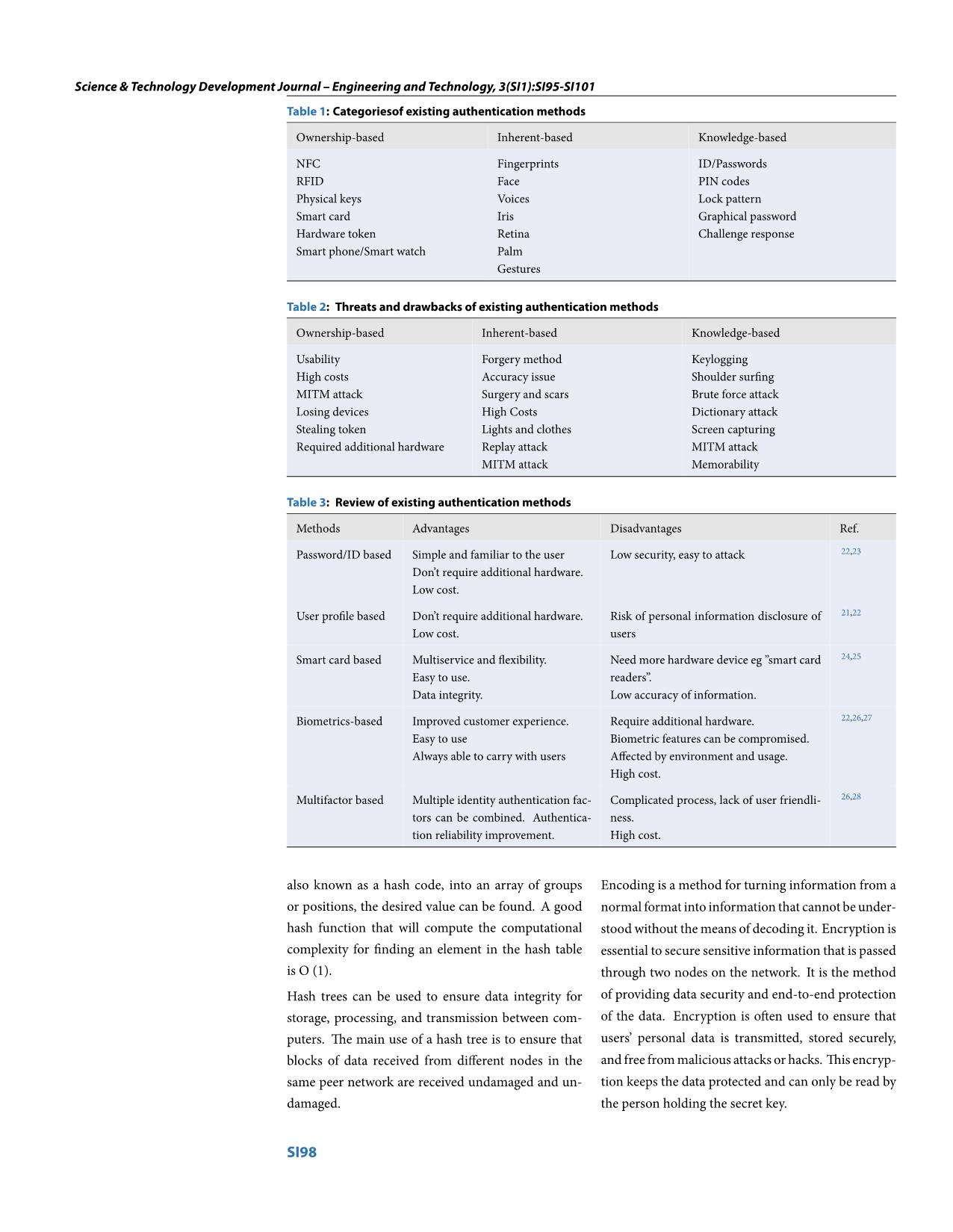
transmission between com- of the data. Encryption is often used to ensure that puters. The main use of a hash tree is to ensure that users’ personal data is transmitted, stored securely, blocks of data received from different nodes in the and free from malicious attacks or hacks. This encryp- same peer network are received undamaged and un- tion keeps the data protected and can only be read by damaged. the person holding the secret key. SI98 Science & Technology Development Journal – Engineering and Technology, 3(SI1):SI95-SI101 A linear dimension reducing transform that projects information field. While providing little data, the au- the profile and the verification data to a lower dimen- thentication process must prove that this data is part sion space, while preserving relative distances of the of the entire user authentication data. vectors and so correctness of authentication. Besides, we can use an Ethereum address as an identi- fier (no username or password is required) and the au- Ensure the Integrity of User Authentication thentication process will be done through smart con- Data tracts. This process is described simply by the follow- User authentication data needs to be absolutely se- ing steps: cure. In particular, this data needs to be guaranteed to not be changed to pass the authentication step of 1. User requests access to the service. the system. There have been many attacks on user databases to steal and modify user in- formation for 2. Service provider sends some challenging ques- many nefarious purposes. This leads to the need for tions to the user. storage methods to ensure the transparency and in- 3. User use the private key of their Ethereum ac- tegrity of the data. With these strict requirements, count to sign the answer then submit the signed blockchain becomes a potential candidate with its answer. preeminent characteristics. 4. Service provider call the smart contract to verify Blockchain technology is commonly known for its ap- answer, signature and user address. plications in the monetary and banking sectors, but it works a little differently from the typical bank- With this approach, service providers will not have to ing system. Instead of relying on centralized regula- store user data, so user data privacy is guaranteed. Be- tors, it guarantees the functionality of the blockchain sides the authentication process is done by smart con- through a set of nodes. This technology ensures im- mutability, blockchain keeps the information in the tract, and this contract is immutable so the authenti- 8,30 best security, not lost, modified and stolen. Trans- cation result is transparent and reliable . parency and makes it anti-corruption CONCLUSION where every node on the system has a copy of the digi- tal ledger. Same rules of consensus so that every node There are many methods of user authentication for needs to check the validity of a transaction. One fea- online learning systems, but each method will have ture of blockchain is that once transaction blocks are different advantages and disadvantages and has not added to the ledger, no one can go back and change it. completely solved the challenges of user authentica- Another potential approach is IPFS, which works by tion. The issue of user authentication still has many storing data on the network in the form of a file struc- challenges that need to be solved thoroughly to im- 29 ture . This file structure is Merkle DAG, which com- prove the security of the system as well as the trust of bines a Merkle tree (which is a form of hash tree to users and society. In addition, we propose a number ensure immutability) and Guided Ring Graph (used of feasible approaches to improve user data privacy as in Git version control, which also allows users to see well as improve the effectiveness of the authentication content version on IPFS). process in the online learning system. Usually a website requires centralized data storage for In the future we will study and propose an effective its files in the server to be able to do so. Operating authentication and identity management solution for with great advantages over http, IPFS is immune to online learning systems that not only ensures security DDoS attacks, which cause a lot of internet resources but also enhances the privacy of users’ data. concentrated today. Another advantage of IPFS is its ability to connect to IoT devices. ACKOWLEDGEMENT Efficient Authentication Process This research was supported by Infinity Blockchain Most authentication processes require users to pro- Labs (IBL) and Vietnam Blockchain Corporation vide personal information for authentication, which (VBC). leads to users having to provide too much sensitive in- CONFLICT OF INTEREST formation, and obviously this is a matter of concern. Therefore, the authentication process should only re- The authors declare no conflict of interest in this arc- quire a small amount of data or even part of a user ticle. SI99 Science & Technology Development Journal – Engineering and Technology, 3(SI1):SI95-SI101 AUTHOR’S CONTRIBUTION Conference on Acoustics, Speech and Signal Processing - Pro- ceedings. 2010;p. 1814–1817. Available from: https://doi.org/ Quang-Huan Luu and Duy-Minh Nguyen verified 10.1109/ICASSP.2010.5495401. the analytical methods. Nguyen Huynh-Tuong and 15. Eveno N, Besacier L. Co-inertia analysis for ”liveness” test in audio-visual biometrics. 2008;p. 257–261. Hoang-Anh Pham supervised the findings of this 16. Meshoul S. Combining Fisher Discriminant Analysis And work. All authors discussed the results and con- Probabilistic Neural Network for Effective On-Line Signature tributed to the final manuscript. Recognition. 2010;p. 658–661. Available from: https://doi.org/ 10.1109/ISSPA.2010.5605586. 17. Jazahanim KS, Ibrahim Z, Mohamed A. Online zones’ iden- REFERENCES tification using signature baseline. 2nd International Confer- 1. Ellis RK. Learning Management Systems. ASTD learning cir- ence on the Applications of Digital Information and Web Tech- cuits, pages. 2009;p. 1–7. nologies, ICADIWT 2009. 2009;p. 363–368. Available from: 2. Alwi HM, Fan IP. Information security management in e- https://doi.org/10.1109/ICADIWT.2009.5273916. learning. (July 2015). 2014;p. 1–6. 18. Brosso I, Neve AL, Bressan G, Ruggiero WV. A continuous au- 3. Kiennert C, Rocher PO, et al. Security challenges in e- thentication system based on user behavior analysis. ARES assessment and technical solutions To cite this version. HAL Id 2010 - 5th International Conference on Availability, Reliabil- : hal-01699388. 2018;Available from: https://doi.org/10.1109/ ity, and Security. 2010;p. 380–385. Available from: https://doi. iV.2017.70. org/10.1109/ARES.2010.63. 4. Miguel J, Caballe S, Xhafa F. Security for e-Learning. Intelligent 19. Muthumanickam K, Ilavarasan E. Behavior based authen- Data Analysis for e-Learning. 2016;p. 7–23. PMID: 28778063. tication mechanism to prevent malicious code attacks in Available from: https://doi.org/10.1016/B978-0-12-804535-0. windows. 2015 IEEE International Conference on Innova- 00002-2. tions in Information, Embedded and Communication Sys- 5. Adamski M, Saeed K. Online signature classification and its tems. 2015;p. 0–4. Available from: https://doi.org/10.1109/ verification system. Proceedings of the 7th Computer In- ICIIECS.2015.7193071. formation Systems and Industrial Management Applications, 20. Ullah A, Xiao H, Lilley M, Barker T. Using Challenge Questions CISIM 2008. 2008;(1):189–194. Available from: https://doi.org/ for Student Authentication in Online Examination. Interna- 10.1109/CISIM.2008.38. tional Journal for Infonomics. 2016;5(3/4):631–639. Available 6. Asha S, Chellappan C. Authentication of e-learners us- from: https://doi.org/10.20533/iji.1742.4712.2012.0072. ing multi-modal bometric technology. IEEE- Interna- 21. Ullah A, Xiao H, Barker T, Lilley M. Graphical and text-based tional Symposium on Biomet- rics and Security Technolo- challenge questions for secure and usable authentication in gies, ISBAST’08. 2008;Available from: https://doi.org/10.1109/ online examinations. 2014 9th International Conference for ISBAST.2008.4547640. Internet Technology and Secured Transactions, ICITST 2014, 7. Gil C, Castro M, Wyne M. Identification in web evaluation pages 302-308, 2014 ;Available from: https://doi.org/10.1109/ in learning management system by fingerprint identification ICITST.2014.7038825. system. Proceedings - Frontiers in Education Conference, FIE. 22. Ullah A, Xiao H, Lilley M. Profile Based Student Authentication 2010;p. 1–6. Available from: https://doi.org/10.1109/FIE.2010. in Online Examination. International Conference on Informa- 5673638. tion Society (i-Society). 2012;p. 109–113. 8. Aggarwal G, Ratha NK, Jea TY, Bolle RM. Gradient based textu- 23. Jiang H. Strong password authentication protocols. ICDLE ral characterization of fingerprints. BTAS 2008 - IEEE 2nd Inter- 2010 - 2010 4th International Conference on Distance Learn- national Conference on Biometrics: Theory, Applications and ing and Education, Proceedings. 2010;p. 50–52. Systems. 2008;Available from: https://doi.org/10.1109/BTAS. 24. Kumar SA, Ashish K, Tarun G. Survey of Remote User Pass- 2008.4699383. word Authentication Scheme Using Smart Cards. Interna- 9. Zhao Q, Ye M. The application and implementation of face tional Journal of Advanced Research. 2015;3(4). recognition in authentication system for distance education. 25. Elwahab AA, Eldin AMB, et al. A security layer for smart 2010 International Conference on Networking and Digital So- card applications authentication. The 2009 International ciety, ICNDS 2010. 2010;1:487–489. Available from: https: Conference on Computer Engineering and Systems, ICCES’09. //doi.org/10.1109/ICNDS.2010.5479246. 2009;p. 514–517. Available from: https://doi.org/10.1109/ 10. Agulla EG, Rifo’n LA, Castro JLA, Mateo CG. Is my student at the ICCES.2009.5383211. other side? applying bio-metric web authentication to elearn- 26. Lim SY, Fotsing PT, et al. Blockchain Technology the Identity ing environments. Proceedings - The 8th IEEE International Management and Authentication Service Disruptor: A Sur- Conference on Advanced Learning Technologies, ICALT 2008. vey. International Journal on Advanced Science, Engineer- 2008;p. 551–553. ing and Information Technology. 2018;8(4-2):1735. Available 11. Toor AS, Wechsler H, Choo KKR. Visual question authentica- from: https://doi.org/10.18517/ijaseit.8.4-2.6838. tion protocol (vqap). Computers Security. 2017;76:12. Avail- 27. Toor AS, Wechsler H, Nappi M, Choo KKR. Visual Question able from: https://doi.org/10.1016/j.cose.2017.11.017. Authentication Protocol (VQAP). Com- puters and Security. 12. Gusev PD, Borzunov GI. The analysis of modern meth- 2018;76:285–294. Available from: https://doi.org/10.1016/j. ods for video authentication. Procedia Computer Science. cose.2017.11.017. 2018;123:161–164. Available from: https://doi.org/10.1016/j. 28. Ometov A, Bezzateev S. Multi-factor authentication: A survey procs.2018.01.026. and challenges in V2X applications. International Congress on 13. Hayes B, Ringwood J. Authenticating student work in an e- Ultra Modern Telecommunications and Control Systems and learning programme via speaker recognition. 3rd Interna- Workshops 2017. 2018;p. 129–136. Available from: https://doi. tional Conference on Signals, Circuits and Systems, SCS 2009. org/10.1109/ICUMT.2017.8255200. 2009;p. 1–6. Available from: https://doi.org/10.1109/ICSCS. 29. Benet J. IPFS - Content Addressed, Versioned, P2P File System. 2009.5412484. (Draft 3). 2014;. 14. Shaver CD, Acken JM. Effects of equipment variation on 30. Buterin V. A next generation Smart Contract & Decentralized speaker recognition error rates. ICASSP, IEEE International Application platform. 2009;p. 1–36. SI100 Tạp chí Phát triển Khoa học và Công nghệ – Kĩ thuật và Công nghệ, 3(SI1):SI95-SI101 Open Access Full Text Article Bài Tổng quan Xác thực người dùng trong hệ thống học tập trực tuyến: Thách thức và giải pháp Lưu Quang Huân*, Nguyễn Duy Minh, Phạm Hoàng Anh, Huỳnh Tường Nguyên TÓM TẮT Ngày nay, học tập trực tuyến đang ngày càng phổ biến và được xem như là một phương pháp thay thế hấp dẫn so với học tập truyền thống. Một hệ thống học tập trực tuyến là sự kết hợp của các Use your smartphone to scan this công cụ giảng dạy, thảo luận cũng như các công cụ hỗ trợ kiểm tra nhằm đánh giá kỹ năng của QR code and download this article người học. Một trong những yếu tố quan trọng quyết định tính bảo mật quả quá trình này là xác thực người dùng. Cũng như các hệ thống thông tin khác, vấn đề xác thực danh tính người dùng trong hệ thống học tập trực tuyến cũng là một vấn đề còn chưa được giải quyết thấu đáo. Trong phần lớn các trường hợp, vai trò này được thực hiện bằng mật khẩu, nhưng bằng chứng cho thấy phương pháp này dễ bị xâm phạm. Trong khi đó có nhiều sự lựa chọn thay thế tồn tại như phương pháp sinh trắc học, phương pháp thử thách người dùng và nhiều các phương pháp khác. Sự phát triển mạnh mẽ của công nghệ đòi hỏi tính bảo mật và xác thực phải được kết hợp chặt chẽ với nhau. Một cuộc khảo sát định tính về các hệ thống xác thực người dùng đang được sử dụng trong các hệ thống E-learning ngày nay và một nghiên cứu so sánh về các cơ chế xác thực khác nhau được trình bày trong bài báo này. Có nhiều phương pháp xác thực người dùng cho các hệ thống học trực tuyến, tuy nhiên mỗi phương pháp sẽ có những ưu nhược điểm khác nhau và chưa giải quyết triệt để những thách thức về xác thực người dùng. Vấn đề xác thực người dùng vẫn còn nhiều thách thức cần được giải quyết triệt để để nâng cao tính bảo mật của hệ thống cũng như sự tin tưởng của người dùng và xã hội Ngoài ra, chúng tôi đề xuất một số phương pháp khả thi để cải thiện quyền riêng tư dữ liệu người dùng cũng như cải thiện hiệu quả của quá trình xác thực trong hệ thống học tập trực tuyến. Từ khoá: Xác thực phân tán, Tính riêng tư, Cây Merkle, Blockchain Trường Đại học Bách Khoa, Đại học Quốc gia Tp. Hồ Chí Minh, Việt Nam Liên hệ Lưu Quang Huân, Trường Đại học Bách Khoa, Đại học Quốc gia Tp. Hồ Chí Minh, Việt Nam Email: huanluuquang@gmail.com Lịch sử • Ngày nhận: 28-7-2019 • Ngày chấp nhận: 23-8-2019 • Ngày đăng: 04-12-2020 DOI : 10.32508/stdjet.v3iSI1.516 Bản quyền © ĐHQG Tp.HCM. Đây là bài báo công bố mở được phát hành theo các điều khoản của the Creative Commons Attribution 4.0 International license. Trích dẫn bài báo này: Huân L Q, Minh N D, Anh P H, Nguyên H T. Xác thực người dùng trong hệ thống học tập trực tuyến: Thách thức và giải pháp. Sci. Tech. Dev. J. - Eng. Tech.; 3(SI1):SI95-SI101. 101
File đính kèm:
 authentication_in_e_learning_systems_challenges_and_solution.pdf
authentication_in_e_learning_systems_challenges_and_solution.pdf

