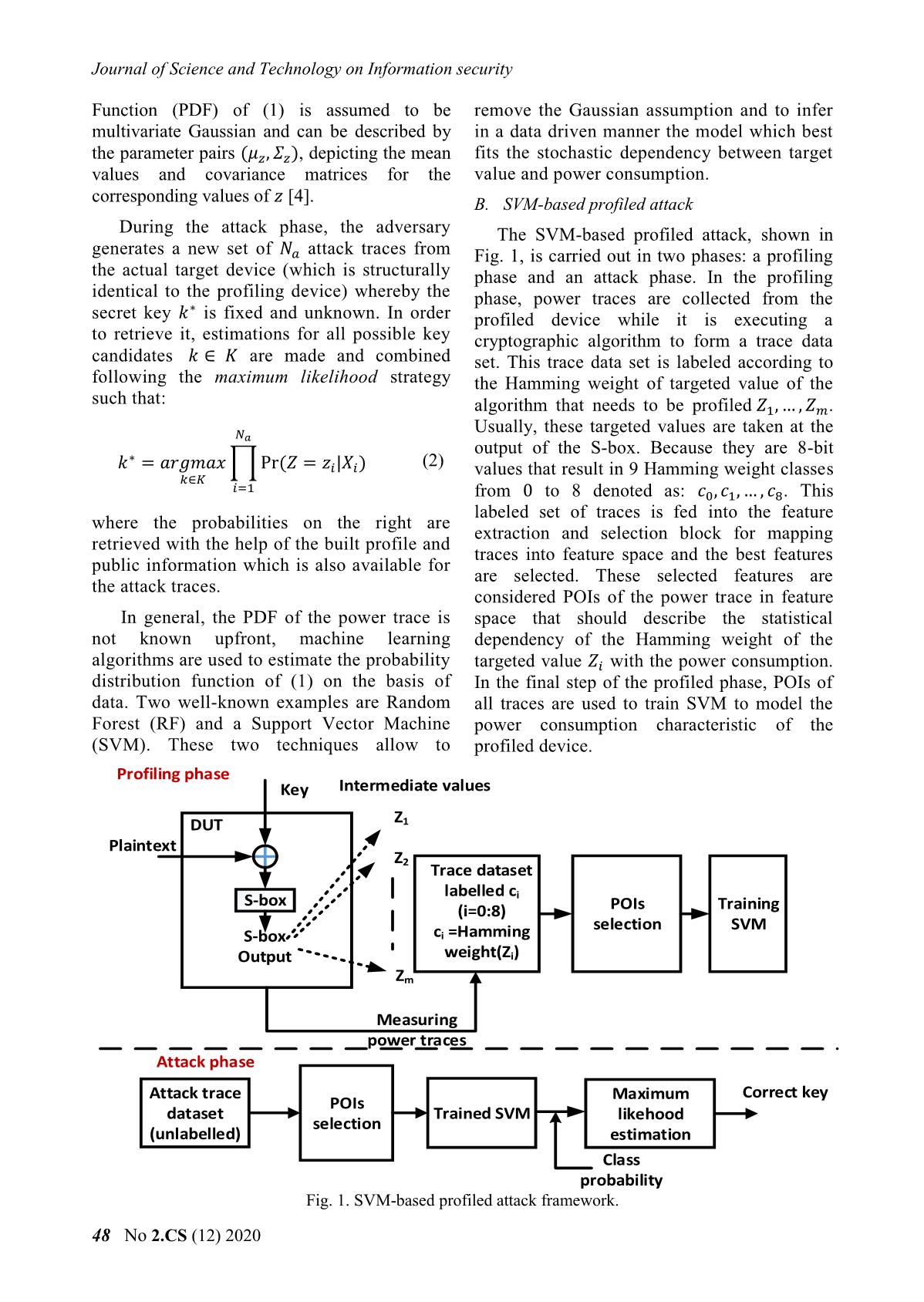
A novel points of interest selection method for svm-based profiled attacks
Hiện nay, tấn công mẫu được xem là
một trong những tấn công kênh kề (SCA) mạnh.
Các thuật toán học máy, ví dụ như máy vector hỗ
trợ (SVM), thường được sử dụng để nâng cao
hiệu quả của tấn công mẫu. Một thách thức đối
với tấn công mẫu sử dụng SVM là cần phải tìm
được các điểm thích hợp (POI) hay các đặc trưng
từ vết điện năng tiêu thụ. Công trình nghiên cứu
này đề xuất một phương pháp mới đề tìm POI
của vết điện năng tiêu thụ bằng cách kết hợp kỹ
thuật phân tích mode biến phân (VMD) và quá
trình trực giao hóa Gram-Schmidt (GSO). Trong
đó, VMD được sử dụng để phân tách vết điện
năng tiêu thụ thành các tín hiệu con còn gọi là
VMD mode và việc lựa chọn POIs trên VMD
mode này được thực hiện dựa trên quá trình
This manuscript is received on November 11, 2020. It is
commented on Decemeber 4, 2020 and is accepted on
Decemeber 4, 2020 by the first reviewer. It is commented on
Decemeber 15, 2020 and is accepted on Decemeber 25, 2020
by the second reviewer.
GSO. Dựa trên phương pháp lựa chọn POIs này,
chúng tôi đề xuất phương pháp tấn công mẫu sử
dụng SVM có hiệu quả tốt hơn các tấn công mẫu
khác ở cùng kịch bản tấn công. Các thí nghiệm
tấn công được thực hiện trên tập dữ liệu được thu
thập từ thẻ thông minh Atmega8515 cài đặt AES-
128 chạy trên nền tảng thiết bị tấn công kênh kề
Sakura-G/W và tập dữ liệu DPA Contest v4, để
chứng minh tính hiệu quả của phương pháp của
chúng tôi, trong việc giảm số lượng vết điện năng
tiêu thụ cần cho cuộc tấn công, đặc biệt trong
trường hợp các điện năng tiêu thụ có nhiễu.

Trang 1

Trang 2

Trang 3
Trang 4

Trang 5

Trang 6
Trang 7
Trang 8
Trang 9
Trang 10
Tải về để xem bản đầy đủ
Tóm tắt nội dung tài liệu: A novel points of interest selection method for svm-based profiled attacks

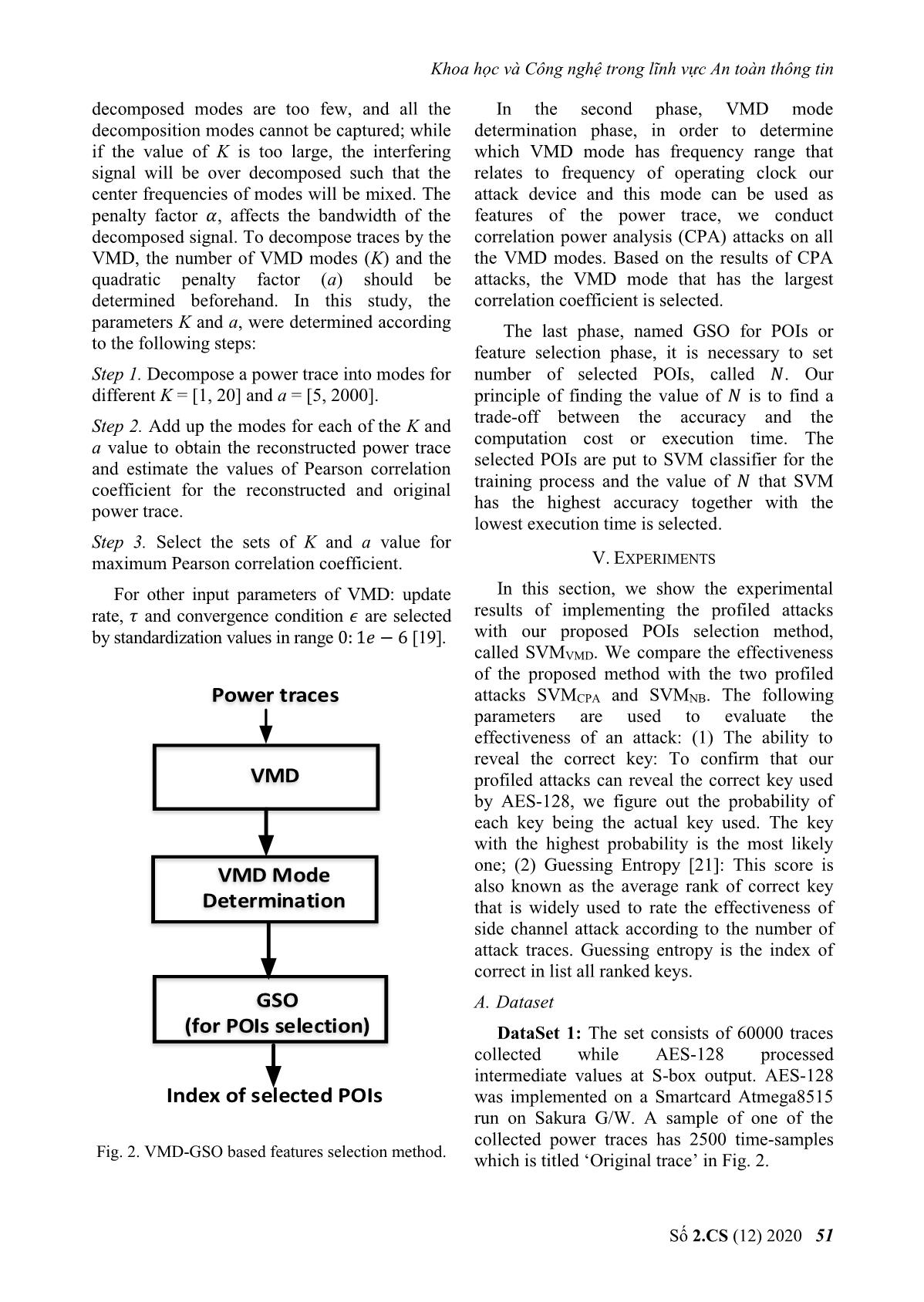
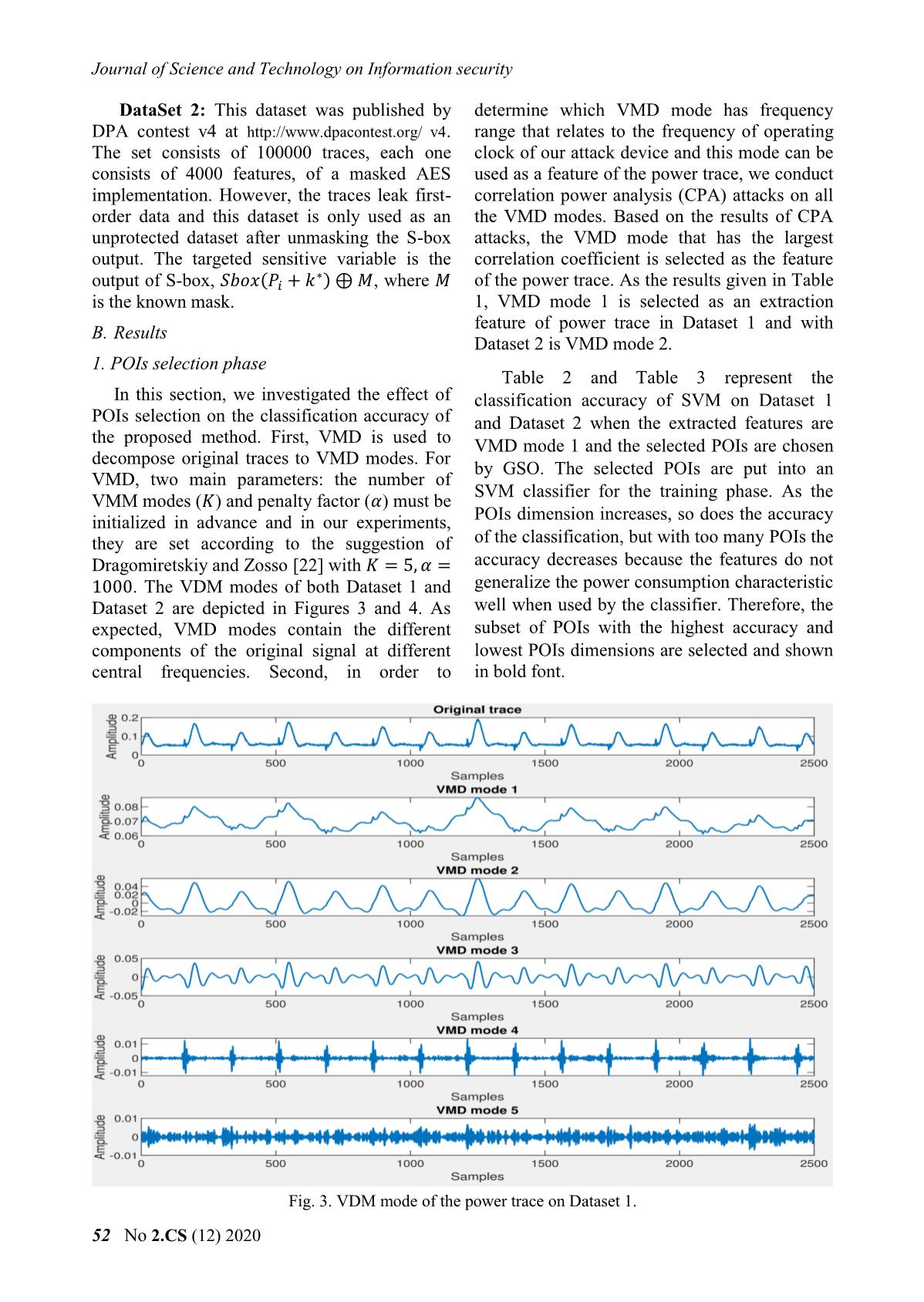
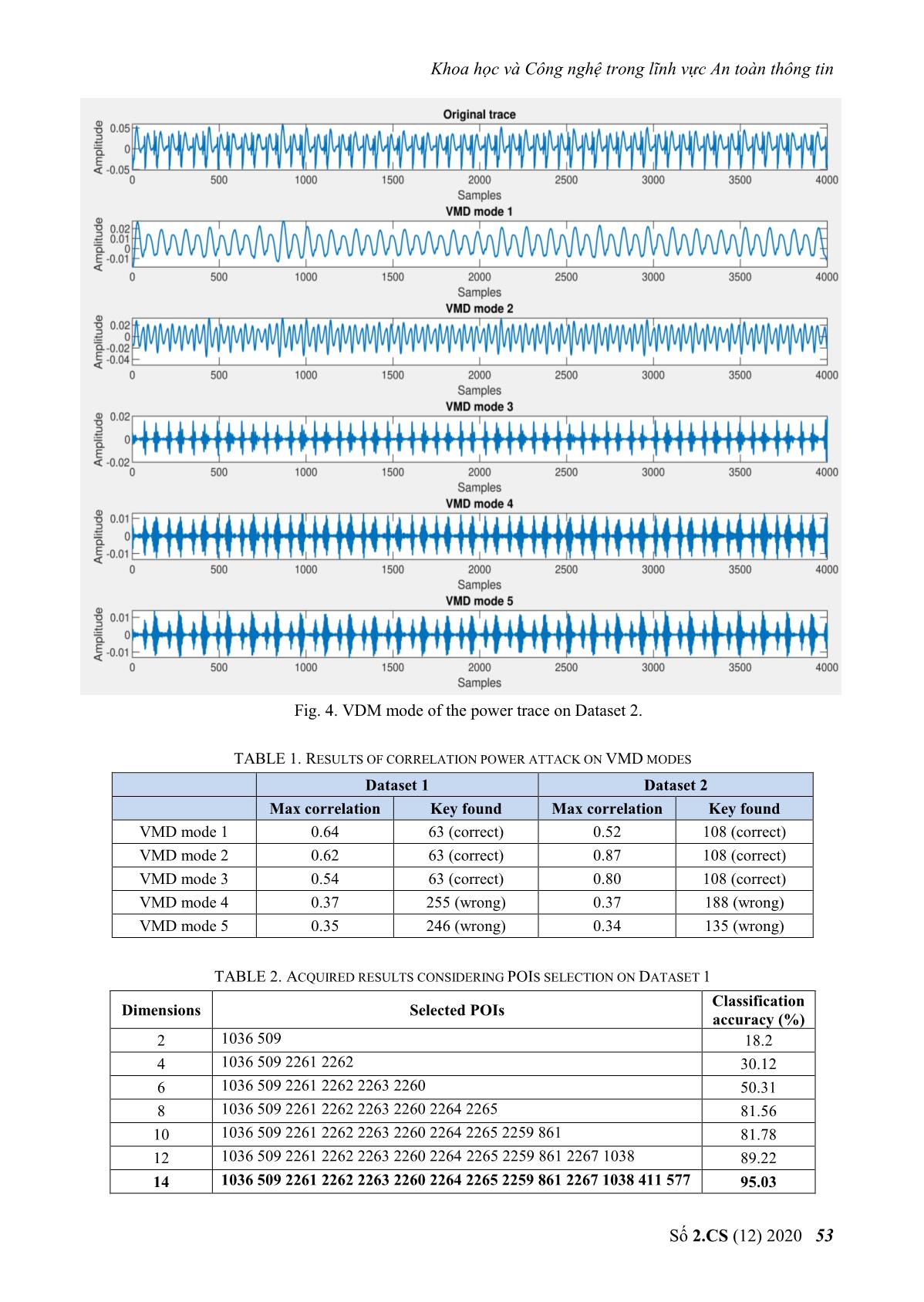
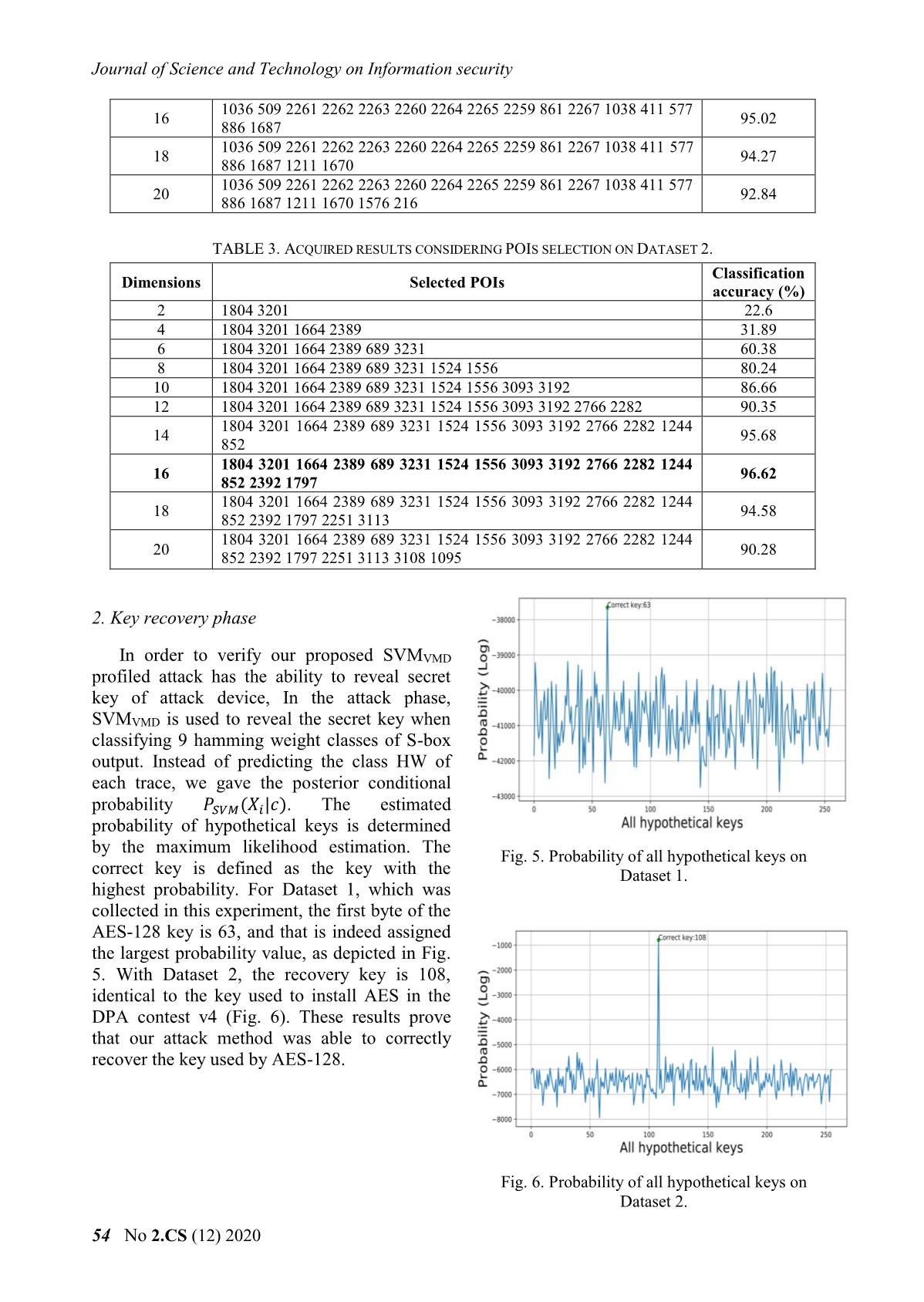
s to VMD modes. For by GSO. The selected POIs are put into an VMD, two main parameters: the number of SVM classifier for the training phase. As the VMM modes (퐾) and penalty factor (훼) must be initialized in advance and in our experiments, POIs dimension increases, so does the accuracy they are set according to the suggestion of of the classification, but with too many POIs the Dragomiretskiy and Zosso [22] with 퐾 = 5, 훼 = accuracy decreases because the features do not 1000. The VDM modes of both Dataset 1 and generalize the power consumption characteristic Dataset 2 are depicted in Figures 3 and 4. As well when used by the classifier. Therefore, the expected, VMD modes contain the different subset of POIs with the highest accuracy and components of the original signal at different lowest POIs dimensions are selected and shown central frequencies. Second, in order to in bold font. Fig. 3. VDM mode of the power trace on Dataset 1. 52 No 2.CS (12) 2020 Khoa học và Công nghệ trong lĩnh vực An toàn thông tin Fig. 4. VDM mode of the power trace on Dataset 2. TABLE 1. RESULTS OF CORRELATION POWER ATTACK ON VMD MODES Dataset 1 Dataset 2 Max correlation Key found Max correlation Key found VMD mode 1 0.64 63 (correct) 0.52 108 (correct) VMD mode 2 0.62 63 (correct) 0.87 108 (correct) VMD mode 3 0.54 63 (correct) 0.80 108 (correct) VMD mode 4 0.37 255 (wrong) 0.37 188 (wrong) VMD mode 5 0.35 246 (wrong) 0.34 135 (wrong) TABLE 2. ACQUIRED RESULTS CONSIDERING POIS SELECTION ON DATASET 1 Classification Dimensions Selected POIs accuracy (%) 2 1036 509 18.2 4 1036 509 2261 2262 30.12 6 1036 509 2261 2262 2263 2260 50.31 8 1036 509 2261 2262 2263 2260 2264 2265 81.56 10 1036 509 2261 2262 2263 2260 2264 2265 2259 861 81.78 12 1036 509 2261 2262 2263 2260 2264 2265 2259 861 2267 1038 89.22 14 1036 509 2261 2262 2263 2260 2264 2265 2259 861 2267 1038 411 577 95.03 Số 2.CS (12) 2020 53 Journal of Science and Technology on Information security 1036 509 2261 2262 2263 2260 2264 2265 2259 861 2267 1038 411 577 16 95.02 886 1687 1036 509 2261 2262 2263 2260 2264 2265 2259 861 2267 1038 411 577 18 94.27 886 1687 1211 1670 1036 509 2261 2262 2263 2260 2264 2265 2259 861 2267 1038 411 577 20 92.84 886 1687 1211 1670 1576 216 TABLE 3. ACQUIRED RESULTS CONSIDERING POIS SELECTION ON DATASET 2. Classification Dimensions Selected POIs accuracy (%) 2 1804 3201 22.6 4 1804 3201 1664 2389 31.89 6 1804 3201 1664 2389 689 3231 60.38 8 1804 3201 1664 2389 689 3231 1524 1556 80.24 10 1804 3201 1664 2389 689 3231 1524 1556 3093 3192 86.66 12 1804 3201 1664 2389 689 3231 1524 1556 3093 3192 2766 2282 90.35 1804 3201 1664 2389 689 3231 1524 1556 3093 3192 2766 2282 1244 14 95.68 852 1804 3201 1664 2389 689 3231 1524 1556 3093 3192 2766 2282 1244 16 96.62 852 2392 1797 1804 3201 1664 2389 689 3231 1524 1556 3093 3192 2766 2282 1244 18 94.58 852 2392 1797 2251 3113 1804 3201 1664 2389 689 3231 1524 1556 3093 3192 2766 2282 1244 20 90.28 852 2392 1797 2251 3113 3108 1095 2. Key recovery phase In order to verify our proposed SVMVMD profiled attack has the ability to reveal secret key of attack device, In the attack phase, SVMVMD is used to reveal the secret key when classifying 9 hamming weight classes of S-box output. Instead of predicting the class HW of each trace, we gave the posterior conditional probability 푃푆 ( 푖| ). The estimated probability of hypothetical keys is determined by the maximum likelihood estimation. The Fig. 5. Probability of all hypothetical keys on correct key is defined as the key with the Dataset 1. highest probability. For Dataset 1, which was collected in this experiment, the first byte of the AES-128 key is 63, and that is indeed assigned the largest probability value, as depicted in Fig. 5. With Dataset 2, the recovery key is 108, identical to the key used to install AES in the DPA contest v4 (Fig. 6). These results prove that our attack method was able to correctly recover the key used by AES-128. Fig. 6. Probability of all hypothetical keys on Dataset 2. 54 No 2.CS (12) 2020 Khoa học và Công nghệ trong lĩnh vực An toàn thông tin Fig. 7 and Fig. 8 report the GE corresponding to different numbers of traces used for attacks with Dataset 1 when SVMVMD, SVMCPA and SVMNB are used to predict hamming weight classes. As expected, the GEs of all attacks decrease as the number of traces increases. Moreover, the larger the size of the training set, the lower the GE. The reason for this is that the performance of SVM is determined by its parameters, and the size of the training set is critical to finding the best parameters for the SVM. With Dataset 2, we performed the same experiments as for Dataset 1, and the GE calculated in the attack phases are presented in Figures 9 and 10. The overall Fig. 8. Attack performance with 200 traces/HW performance of all the attacks is the same as class on Dataset 1. those for Dataset 1. Again, SVMVMD achieves the best GE values. In Table 4, for each dataset we give the number of traces required by the profiled attacks based on SVM for guessing entropy to reach 0. SVMVMD requires the minimum number of traces to recover the key, 10.2 and 5.3 traces on average, corresponding to 100 and 200 profiling traces respectively. These empirical results indicate that the SVM-based profiled attack with our proposed POIs selection method is more effective than the attacks with the CPA and normal-based POI selection method. This can be explained by the combining of VMD and GSO for POI selection allowing more effective selection of trace Fig. 9. Attack performance with 100 traces/HW characteristics than the CPA and normal-based class on Dataset 2. POI selection methods. Fig. 7. Attack performance with 100 traces/HW Fig. 10. Attack performance with 200 traces/HW class on Dataset 1. class on Dataset 2. Số 2.CS (12) 2020 55 Journal of Science and Technology on Information security 3. Results in the case of noisy traces Fig. 14. Attack results on Dataset 2 with 푆 푅2 = 10 noise added to power traces. Fig. 11. Attack results on Dataset 1 with 푆 푅1 = 20 noise added to power traces. The power traces are usually polluted with noise in practice. To examine the effectiveness of our proposed SVMVMD profiled attack in noisy condition, additive Gaussian noise is added to the power traces. In our experiments, two noise levels of standard deviation 푆 푅1 = 20 and 푆 푅2 = 10 are added to both Dataset 1 and Dataset 2. In addition, different feature extraction techniques were used for the SVM- based profiled attacks to investigate their effects on the efficiency of the attacks in the presence of noise. Overall, the guessing entropy of all the attacks increase with the level of noise, but the attack based on SVM with combining of VMD and GSO is the least sensitive to noise. The Fig. 12. Attack results on Dataset 1 with 푆 푅2 = 10 noise added to power traces. results of our attacks with 200 profiling traces per Hamming weight class, presented in Fig. 11, 12, 13 and 14 and Table 5, show that out of SVMCPA, SVMNB and SVMVMD, the proposed method, SVMVMD, has the best performance at both noise levels while SVMCPA and SVMNB are comparable to each other. After adding noise to the power trace, the number of traces required for GE to reach 0 increased by only 25% approximately with the proposed attack, while it increased by over 100% for the other methods. This proves that the VMD signal is insensitive to noise so the SVMVMD attack should work well under noisy conditions. This property is very useful in real attack scenarios where Fig. 13. Attack results on Dataset 2 with 푆 푅1 = 20 collected measurement traces invariably noise added to power traces. contain noise. 56 No 2.CS (12) 2020 Khoa học và Công nghệ trong lĩnh vực An toàn thông tin TABLE 4. NUMBER OF TRACES USED BY THE ATTACKS TO ATTAIN GE=0 Num. of. Dataset 1 Dataset 2 profiling traces SVMVMD SVMCPA SVMNB SVMVMD SVMCPA SVMNB 100 10.2 18.1 17.6 10.3 19.2 18.3 200 5.3 9.2 8.7 4.7 9.4 7.3 TABLE 5. NUMBER OF NOISY TRACES USED BY THE ATTACKS TO ATTAIN GE=0 Dataset 1 Dataset 2 Noise level SVMVMD SVMCPA SVMNB SVMVMD SVMCPA SVMNB 푆 푅1 = 20 7.4 19.0 17.0 6.7 18.8 14.6 푆 푅2 = 10 8.6 25.7 23.6 9.8 21.6 20.2 VI. CONCLUSION [3] Gierlichs B., Batina L., Tuyls P., Preneel B. In this work, the combining of variational “Mutual Information Analysis”. In: Oswald mode decomposition and Gram-Schmidt E., Rohatgi P. (eds) Cryptographic Hardware orthogonalization was proposed as a POIs and Embedded Systems – CHES 2008. CHES selection method of power traces. The VMD 2008. Lecture Notes in Computer Science, vol mode that has central frequency related to clock 5154. Springer, Berlin, Heidelberg. operation frequency of the attack device can be [4] Chari S., Rao J.R., Rohatgi P. “Template used as features of power traces and GSO can Attacks”. In: Kaliski B.S., Koç .K., Paar C. be used as a POIs selection method. (eds) Cryptographic Hardware and Embedded Systems - CHES 2002. CHES 2002. Lecture Experimental results show that an acceptable Notes in Computer Science, vol 2523. classification accuracy can be achieved when Springer, Berlin, Heidelberg. SVM classifier uses these selected features as its input. Compared to other SVM-based [5] Heuser A., Zohner M. “Intelligent Machine profiled attacks, the SVMVMD required the Homicide.” In: Schindler W., Huss S.A. (eds) minimum number of traces for successful key Constructive Side-Channel Analysis and Secure Design. COSADE 2012. Lecture Notes recovery. Furthermore, SVMVMD is less sensitive to noise so can be used well with noisy in Computer Science, vol 7275. Springer, Berlin, Heidelberg. power traces. In our opinion, this work suggests a new approach for feature extraction from [6] Hospodar, G., Gierlichs, B., De Mulder, E. et power traces using variational mode al. “Machine learning in side-channel analysis: decomposition, and this method should also be a first study.” J Cryptogr Eng 1, 293. 2011. tested in combination with other feature [7] Hospodar, G., De Mulder, E., Gierlichs, B., selection methods and learning algorithms for Vandewalle, J., Verbauwhede, I. “Least profiled attacks. Squares Support Vector Machines for Side- Channel Analysis”. In: COSADE 2011. CASED, Darmstadt. REFERENCES [1] Kocher P., Jaffe J., Jun B. “Differential Power [8] S. Picek et al. “Side-channel analysis and Analysis”. In Proceedings of the 19th Annual machine learning: A practical perspective”. International Cryptology Conference on 2017 International Joint Conference on Neural Advances in Cryptology. London (UK), 1999, Networks (IJCNN), Anchorage, AK, 2017, pp. pp. 388–397. 4095-4102. [2] Brier E., Clavier C., Olivier F. “Correlation [9] Zheng, Y., Zhou, Y., Yu, Z., Hu, C., Zhang, Power Analysis with a Leakage Model”. In: H. "How to compare selections of points of Joye M., Quisquater JJ. (eds) Cryptographic interest for side-channel distinguishers in Hardware and Embedded Systems - CHES practice?" Information and Communications 2004. CHES 2004. Lecture Notes in Computer Security: 16th International Conference, Science, vol 3156. Springer, Berlin, Heidelberg. ICICS 2014, Hong Kong, China. Số 2.CS (12) 2020 57 Journal of Science and Technology on Information security [10] Rechberger C., Oswald E. "Practical Template [18] Bartkewitz, T., Lemke-Rust, K. "Efficient Attacks." Information Security Applications. template attacks based on probabilistic multi- WISA 2004. class support vector machines". In Mangard, [11] Gierlichs B., Lemke-Rust K., Paar C. S. (ed.) Smart Card Research and Advanced "Templates vs. Stochastic Methods". In Goubin Applications:11th International Conference, L., Matsui M. (eds) Cryptographic Hardware CARDIS 2012, Graz, Austria, 2012. and Embedded Systems - CHES 2006. Lecture [19] Dragomiretskiy K and Zosso D. "Variational Notes in Computer Science, vol 4249, Springer, Mode Decomposition". IEEE Transactions on Berlin, Heidelberg, 2006, pp. 15-29. Signal, vol. 62, pp. 513-544, 2014. [12] Stefan Mangard, Elisabeth Oswald, and [20] H. Stoppiglia, G. Dreyfus, R. Dubois, Y. Thomas Popp. “Power Analysis Oussar. "Ranking a random feature for Attacks:Revealing the Secrets of Smart variable and feature selection". J. Mach. Cards”. Springer US, 2007. Learn, vol. 3, pp. 1399-1414, 2003. [13] Lomné V., Prouff E., Roche T. "Behind the [21] Standaert FX., Malkin T.G., Yung M. "A Scene of Side Channel Attacks". In Sako K., Unified Framework for the Analysis of Side- Sarkar P. (eds) Advances in Cryptology - Channel Key Recovery Attacks". In In: Joux ASIACRYPT 2013. ASIACRYPT 2013. A. (eds) Advances in Cryptology - Lecture Notes in Computer Science, vol EUROCRYPT 2009. EUROCRYPT 2009. 8269, Springer, Berlin, Heidelberg, 2013, Lecture Notes in Computer Science, vol 5479, pp. 506-525. Springer, Berlin, Heidelberg, 2009. [14] Lerman, L., Bontempi, G., Markowitch, O. "Side channel attack: an approach based on machine learning". In COSADE 2011 - ABOUT THE AUTHORS Second International Workshop on Tran Ngoc Quy Constructive Side-Channel, 2011. Workplace: Academy of [15] Liu, J., Zhou, Y., Han, Y., Li, J., Yang, S., Cryptography Techniques Feng, D. "How to characterize side-channel Email: quyhvm@gmail.com leakages more accurately?". In ISPEC 2011 - Education: Master’s degree in Information Security Practice and Electronic and Communication Experience:7th International Conference, Techniques. Guangzhou, China, 2011. Recent research direction: hardware attack, side [16] Houssem Maghrebi, Thibault Portigliatti, and channel attack, IoT security. Emmanuel Prouff. "Breaking cryptographic implementations using deep learning techniques". In Claude Carlet, M. Anwar Nguyen Hong Quang Hasan, and Vishal Saraswat, editors, Security, Workplace: Academy of Privacy, and Applied Cryptography Cryptography Techniques Engineering, Springer International Email: quangnh@actvn.edu.vn Publishing. ISBN 978-3-319-49445-6, 2016, Education: Received Master’s degree pp. 3-26. in 2003 and Assoc. Professor title in [17] Picek, S., Heuser, A., Jovic, A., Legay, A. "On 2016. the relevance of feature selection for profiled Recent research direction: cryptographic design, side side-channel attacks". Cryptology ePrint channel attack, hardware security. Archive, Report 2017/1110, https://eprint.iacr.org/2017/, 2017. 58 No 2.CS (12) 2020
File đính kèm:
 a_novel_points_of_interest_selection_method_for_svm_based_pr.pdf
a_novel_points_of_interest_selection_method_for_svm_based_pr.pdf

